The transaction did not lose money, but the assets evaporated? How to accurately harvest your assets with MEV sandwich attack?

Reprinted from panewslab
03/24/2025·1MWith blockchain technology constantly maturing and ecology becoming increasingly complex, MEV (maximum extractable value) was originally regarded as an occasional loophole caused by transaction sorting defects, and is gradually evolving into a highly complex and systematic profit harvesting mechanism. Among them, the sandwich attack has attracted much attention because it uses the transaction sorting power to insert its own transactions before and after the target transaction, and manipulates asset prices to achieve low buying and high selling arbitrage. It has become one of the most controversial and destructive attack methods in the DeFi ecosystem.
**1. Basic concepts of MEV and sandwich attacks. Evolution and status and
cases of MEV sandwich attacks.**
Source and technological evolution of MEV:
MEV (Maximum Extractable Value) was originally called miner extractable value, and refers to the additional economic benefits that miners or validators can obtain during the block construction process by using manipulation of transaction order, inclusion or exclusion rights. Its theoretical basis lies in the openness of blockchain transactions and the uncertainty of transaction sorting in memory pools. With the development of tools such as Lightning loans and transaction packaging (bundles), the originally sporadic arbitrage opportunities have gradually been amplified, forming a complete profit harvesting chain. From the initial incident to the current systematic and industrial arbitrage model, MEV not only exists in Ethereum, but also presents different characteristics on multiple chains such as Solana and Binance Smart Chain.
The principle of sandwich attack:
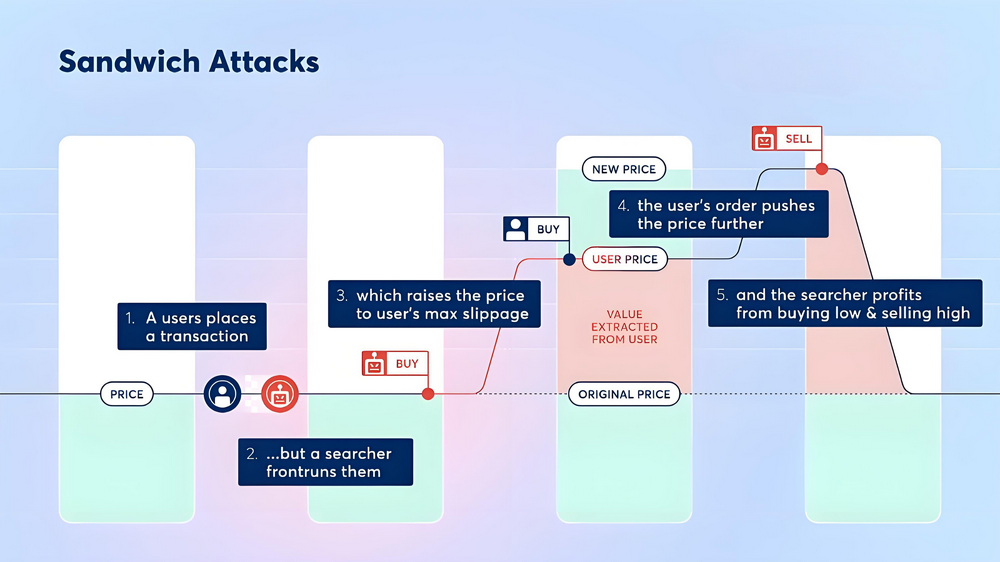
Sandwich attack is a typical operation method in MEV extraction. The attacker uses the real-time monitoring ability of memory pool transactions to submit transactions separately before and after the target transaction, forming a "front-run" transaction sequence, and then achieves arbitrage through price manipulation. Its core principles include:
-
Front-Run : When an attacker detects a large amount or high slippage, submit his or her own pay order immediately to push up or lower the market price.
-
Victim Transaction : The target transaction is executed after the price is manipulated, because there is a significant deviation between the actual transaction price and the expected price, the trader bears additional costs.
-
Back-Run : Following the target transaction, the attacker submits a reverse transaction, selling (or buying) previously acquired assets at a high price, thereby locking in the spread profit.
This operation is like "sandwich" the target transaction between one's own two transactions, so it is called a "sandwich attack".
2. Evolution, status and cases of MEV sandwich attacks
(1) From sporadic vulnerabilities to systematic mechanisms
Initially, MEV attacks only occasionally and are smaller in scale due to the inherent shortcomings of transaction sorting mechanisms in blockchain networks. However, with the surge in DeFi ecological transaction volume and the continuous development of tools such as high-frequency trading robots and flash loans, attackers have begun to build highly automated arbitrage systems, transforming this attack method from sporadic events to a systematic and industrial arbitrage model. By utilizing high-speed networks and precision algorithms, attackers can first deploy pre- and post-transactions in a very short time, use Lightning loans to obtain large amounts of funds, and complete arbitrage operations in the same transaction. Currently, cases of a single transaction on multiple platforms where hundreds of thousands or even millions of dollars of profits have appeared. This transformation marks that the MEV mechanism has developed from occasional loopholes to a mature profit-harvest system.
(2) Attack modes with different platform characteristics
Due to differences in design concepts, transaction processing mechanisms, and validator structures, different blockchain networks have different implementation characteristics. like:
-
Ethereum : An open and transparent memory pool allows all transaction information to be confirmed to be monitored, and attackers often preempt transaction packaging order by paying higher gas fees. To cope with this problem, mechanisms such as MEV-Boost and Proposer-Builder Separation (PBS) have been introduced into the Ethereum ecosystem in order to reduce the risk of single node manipulating transaction sorting.
-
Solana : Although Solana does not have a traditional memory pool, due to the relatively concentrated validator nodes, some nodes may even collude with the attacker to leak transaction data in advance, allowing the attacker to quickly capture and utilize target transactions, thus making sandwich attacks frequently occur in this ecosystem and make a large profit.
-
Binance Smart Chain (BSC) : Although the ecological maturity of BSC is different from Ethereum, its lower transaction costs and simplified structure also provide space for some arbitrage behaviors. Various robots can also use similar strategies to achieve profit extraction in this environment.
This difference in cross-chain environment has prompted attack methods and profit distribution to be unique on different platforms, and it also puts forward higher requirements for prevention strategies.
(3) Latest data and cases
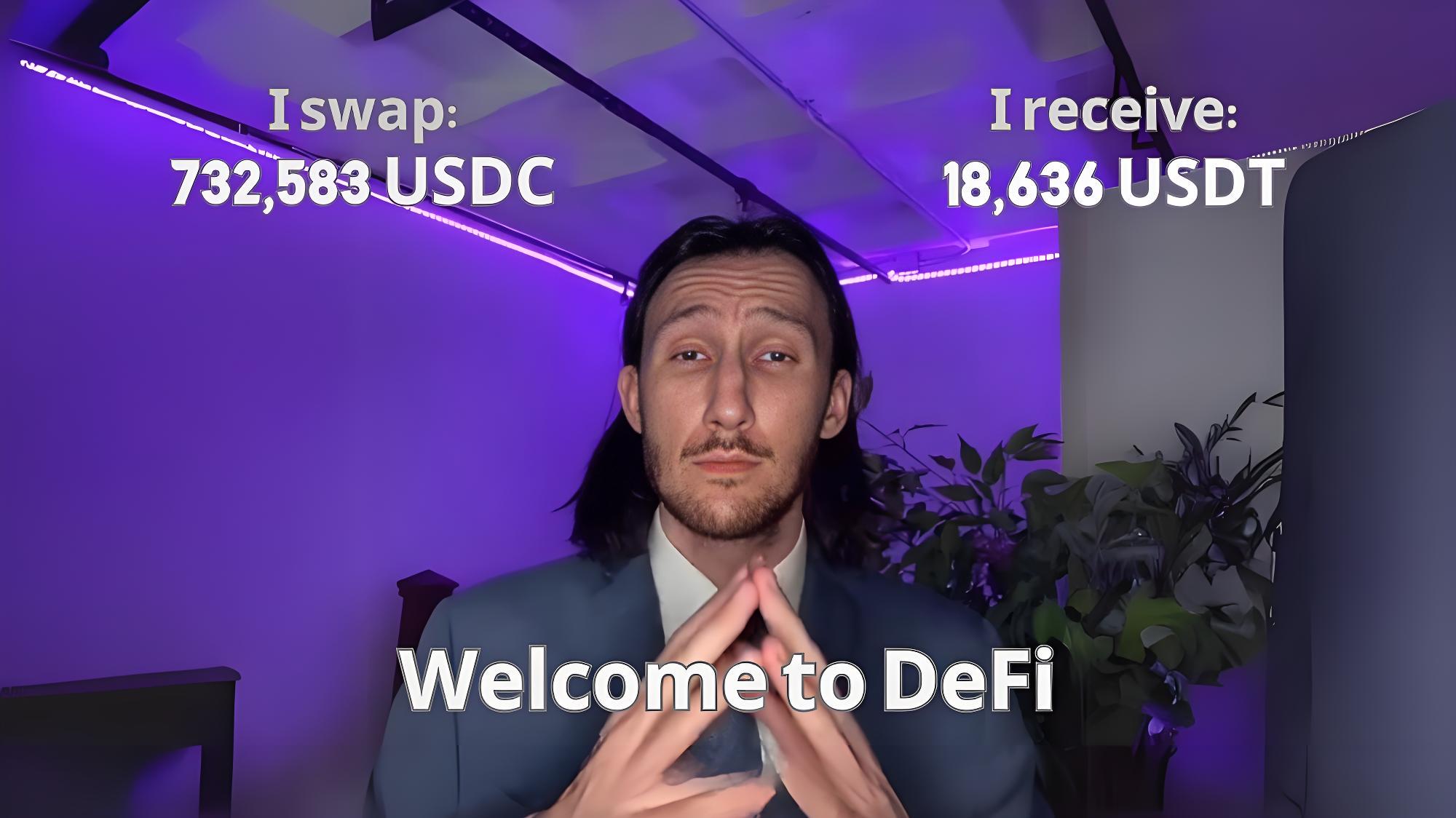
Uniswap Platform Case : On March 13, 2025, a trader lost $732,000 in a transaction worth about 5 SOLs while a trader was involved in a sandwich attack due to a sandwich attack. The incident shows that the attacker used the pre-transaction to seize the block packaging rights and inserted the transaction before and after the target transaction, causing the victim's actual transaction price to deviate significantly from expectations.
Continuous evolution on the Solana chain: In the Solana ecosystem, sandwich attacks are not only frequent, but new attack modes have emerged. Some verifiers are even suspected of colluding with the attacker to obtain users' trading intentions in advance by leaking transaction data, and then implement accurate attacks. This has led to the revenue of some attackers on the Solana chain growing from tens of millions of dollars to hundreds of millions of dollars in just a few months.
These data and cases show that MEV sandwich attacks are no longer accidental events, but are characterized by systematization and industrialization along with the increasing transaction volume and complexity of blockchain networks.
3. Operation mechanism and technical challenges of sandwich attack
As the overall market transaction volume continues to expand, the frequency of MEV attacks is on the rise with a single profit. The transaction cost-to-income ratio of sandwich attacks on some platforms has even reached a high level. The following are several conditions that need to be met for the implementation of sandwich attacks:
-
Transaction listening and capture : Attackers must monitor transactions to be confirmed in the memory pool in real time and identify transactions with a greater price impact.
-
Competition for priority packaging rights : Using higher gas fees or priority fees, attackers will first package their transactions into blocks to ensure they are executed separately before and after the target transaction.
-
Accurate calculation and slippage control : When executing pre- and post-trading transactions, the trading volume and expected slippage must be accurately calculated, which not only drives price fluctuations, but also ensures that the target transaction does not fail due to exceeding the set slippage.
Implementing such an attack requires not only high-performance trading bots and fast network responses, but also high miner bribery fees (such as increased gas fees) to ensure transaction priority. These costs constitute the main expenditure of the attacker, and in the fierce competition, multiple robots may also attempt to seize the same target transaction at the same time, further compressing the profit margin. These technological and economic barriers continue to prompt attackers to update their algorithms and strategies in a fierce competition environment, and also provide a theoretical basis for the design of prevention mechanisms.
4. Industry response and prevention strategies
Prevention strategies for ordinary users:
-
Set reasonable slippage protection : When submitting a transaction, slippage tolerance should be reasonably set based on the current market volatility and expected liquidity conditions to avoid transaction failure due to too low settings, and not maliciously attacked due to too high settings.
-
Use privacy trading tools : use technical means such as private RPC, order packaging and auctions, and hide transaction data outside the public memory pool to reduce the risk of being attacked.
Recommendations for technological improvement at the ecosystem level:
-
Transaction sorting and proposer-builder separation (PBS) : By separating block construction from block proposal responsibilities, a single node's control over transaction sorting is restricted, thereby reducing the possibility that validators can use the advantage of sorting to perform MEV extraction.
-
MEV-Boost and transparency mechanism : Introducing solutions such as third-party relay services (Relay) and MEV-Boost to make the block construction process open and transparent, reduce dependence on a single node, and improve overall competitiveness.
-
Off-chain order flow auction and outsourcing mechanism : With the help of outsourcing orders (such as CoW protocol) and order flow auction mechanism, batch matching of orders is achieved, which not only improves the possibility of users obtaining the best price, but also makes it difficult for attackers to operate alone.
-
Smart contracts and algorithm upgrades : With the help of artificial intelligence and machine learning technology, we will improve the real-time monitoring and prediction capabilities of abnormal data fluctuations on the chain, and help users avoid risks in advance;
As the DeFi ecosystem continues to expand, transaction volume and transaction complexity continue to increase, MEV and its related attack methods will face more technological confrontations and economic games. In the future, in addition to the improvement of technical means, how to reasonably allocate economic incentives while ensuring decentralized characteristics and network security will become an important topic of common concern to the industry.
V. Conclusion
The MEV sandwich attack evolved from the initial occasional vulnerability to a systematic profit harvesting mechanism, posing a serious challenge to the DeFi ecosystem and user asset security. The latest cases and data in 2025 show that the risks of sandwich attacks still exist and continue to escalate on mainstream platforms such as Uniswap or Solana. In order to protect user assets and market equity, the blockchain ecosystem needs to work together in technological innovation, transaction mechanism optimization and regulatory coordination. Only in this way can the DeFi ecosystem find a balance between innovation and risk and achieve sustainable development .



 jinse
jinse