Revealing the Shocking Crypto Case of North Korean Hackers: Why is it so strong? Where does the money go

Reprinted from jinse
06/12/2025·3DDeng Tong, Golden Finance
On June 11, 2025, according to Kyodo News, Japanese Prime Minister Shigeru Ishiba plans to propose to strengthen the crackdown on North Korea 's malicious online activities such as theft of cryptocurrency at the G7 summit (G7 summit) held in Canada from June 15 to 17. This will be the first time the G7 summit discussed North Korea's cryptocurrency stealing. According to several relevant Japanese government officials, the move aims to strengthen supervision through cooperation between multiple countries and cut off the channels for North Korea to illegally obtain cryptocurrency funds using cyber attacks, which are believed to be used to develop weapons of mass destruction.
What shocking cases have North Korean hackers done? How much cryptocurrency has been stolen? Why is North Korea good at hacking? Where did all this money be used?
1. A shocking case done by North Korean hackers
Top 1: Bybit, $1.46 billion
On February 21, 2025, Bybit, a cryptocurrency exchange based in Dubai, encountered an incident of approximately US$1.46 billion in crypto assets. Preliminary reports show that attackers used malware to trick exchanges into approving transactions to transfer funds to thieves’ accounts, the largest cryptocurrency theft to date. Elliptic analyzed a variety of factors, including the analysis of the money laundering paths of stolen crypto assets, and determined that the mastermind behind the Bybit theft was North Korea's Lazarus Group.
Top 2: Ronin Network, $620 million
In March 2022, the Ethereum sidechain built for Axie Infinity’s play-and- earning game was exploited, stealing $620 million worth of Ethereum and USDC. Ronin can only recover a small portion of the stolen funds. The attack was blamed on the Lazarus Group, a group that is allegedly linked to the North Korean government.
Top 3: DMM Bitcoin, $308 million
On May 31, 2024, 4,502.9 Bitcoins were stolen from the Japanese exchange DMM Bitcoin. At the time of the incident, these Bitcoins were worth $308 million. The FBI, the Department of Defense and the Japanese Police Department said the theft was done by hackers related to North Korea.
Top 4: KuCoin, $275 million
In September 2020, Singapore-based cryptocurrency exchange KuCoin's $275 million worth of cryptocurrency was stolen, including $127 million in ERC20 tokens for use in Ethereum smart contracts. However, the subsequent tracking of the chain successfully frozen $170 million in assets. Institutions such as Tether and Circle also cooperated to mark the stolen money, which ultimately forced the hackers to return part of the funds. North Korean hacker group Lazarus Group has been accused of being the killer of the burglary.
Top 5: WazirX, $230 million
On July 18, 2024, Indian cryptocurrency exchange WazirX suffered a loss of US$230 million. There is evidence that the hacker may be the North Korean government-backed Lazarus Group, which has converted most of the stolen assets into Ethereum.
Top 6: Atomic Wallet, $100 million
In June 2023, users of the Atomic Wallet service were stolen from more than $100 million worth of cryptocurrency, and the FBI later confirmed its connection to the North Korean hacker group Lazarus Group.
Top 7: Radiant Capital, $50 million
On October 16, 2024, the lending agreement Radiant Capital was stolen about $50 million. Radiant Capital said the hacker launched an attack via Telegram sending malware sent by a North Korean-alien hacker who impersonated a former contractor and we are highly convinced that the attack was conducted by a North Korean (DPRK) affiliated threat actor.
Top 8: Stake.com, $41 million
In September 2023, the online casino and gambling platform Stake.com, a $41 million cryptocurrency, was stolen, and the perpetrator was Lazarus Group.
Top 9: Upbit, $41 million
In November 2019, Upbit was stolen 342,000 Ethereums, worth $41 million at the time. The police believed that it was a crime committed by North Korean hackers Lazarus and Andariel based on the results of North Korean IP address analysis, virtual asset flow, traces of North Korean vocabulary use and evidence obtained in cooperation with the FBI.
2. Explain the Lazarus Group, a North Korean hacker organization
1. Introduction to Lazarus Group
The Lazarus Group is allegedly operated by the North Korean government. While little is known about the organization, researchers have blamed the organization for multiple cyber attacks launched since 2010. According to North Korean defector Jin Guosong, the force is called the "414 Liaison Office" within North Korea.
The earliest known attacks in the group, known as Operation Troy, occurred between 2009 and 2012. This is a cyber espionage campaign that targets the South Korean government in Seoul based with simple distributed denial of service attack (DDoS). They also launched attacks in 2011 and 2013. Although uncertain, they may also be behind the attacks on South Korea in 2007. The group's most well-known attack was the 2014 attack on Sony Pictures. The attack on Sony Pictures uses more complex technologies, highlighting the organization becoming more advanced over time.
In 2015, Lazarus Group reportedly stole $12 million from Austrian banks in Ecuador and $1 million from Tien Phong banks in Vietnam. They also target banks in Poland and Mexico. The 2016 bank robbery, including an attack on the Bangladesh bank, successfully stole $81 million, and the incident was blamed on the group. According to reports, in 2017, Lazarus Group stole $60 million from Taiwan’s Far East International Bank, and although the actual amount of the stolen money is unclear, most of the funds have been recovered.
Lazarus Group has also created many cases, so I will not repeat them here.
2. How to Lazarus Group Launder Money
Lazarus Group’s money laundering process: The first step is to exchange all stolen tokens into “native” blockchain assets, such as ETH. This is because tokens have issuers that can in some cases “freeze” wallets containing stolen assets, while ETH or Bitcoin has no central authority to freeze.
The second step is to "layer" the stolen funds in an attempt to cover up the transaction path. The transparency of blockchain means that these transaction paths can be traced, but these hierarchical strategies will complicate the tracking process and secure valuable monetization time for money launderers. The layering process can take many forms, including: transferring funds through a large number of cryptocurrency wallets; transferring funds to other blockchains using cross-chain bridges or exchanges; switching between different crypto assets using DEXs, token exchange services or exchanges; and using “coin mixers” such as Tornado Cash or Cryptomixer.
North Korea’s Lazarus Group is the most “professional” and most resource-rich crypto asset money launderers, constantly adjusting their technology to avoid the identification and seizure of stolen assets.
For details, please see the Golden Finance article "The Biggest Theft Case in History: Bybit Hacker Fund Tracking"
3. "Takes" of Lazarus Group members
Members of the North Korean hacker group Lazarus Group once used false identities to set up two shell companies in New Mexico and New York, Blocknovas LLC, and Softglide LLC, to spread malware through false recruitment and specialize in attacking cryptocurrency developers. Cybersecurity company Silent Push disclosed that these companies used fake interviews to induce victims and steal sensitive information such as encrypted wallets and passwords, which has caused many developers to be caught. Silent Push called this a rare case of "North Korean hackers registering legal companies in the United States to commit cyber attacks."
3. How much money did North Korean hackers steal?
The UN team of experts investigating North Korea 's sanctions evasion estimated in 2024 that North Korea has stolen more than $3 billion in cryptocurrency since 2017.
According to the Chainalysis report, in 2023, North Korea-related hackers stole about $660.5 million through 20 incidents; in 2024, this figure increased to $1.34 billion in 47 incidents, with the value of the stolen increased by 102.88%. These figures account for 61% of the total amount of stolen in that year and 20% of the total number of incidents.
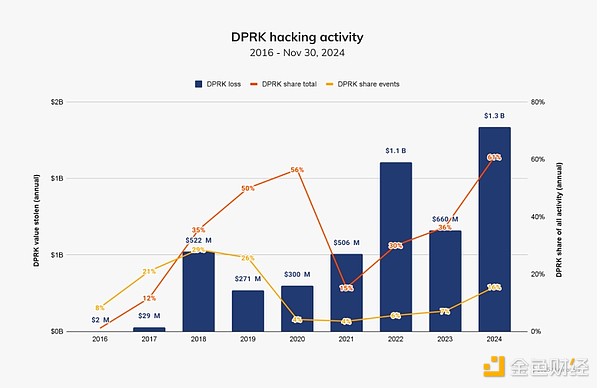
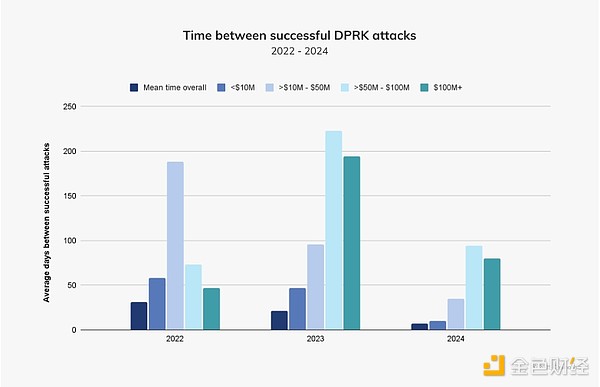
In 2024, attacks worth between $5 billion and $100 million and above occur much more frequently than in 2023, indicating that North Korea is doing better and faster in large-scale attacks. This is in sharp contrast to the previous two years, where its profits tend to be less than $50 million each time.
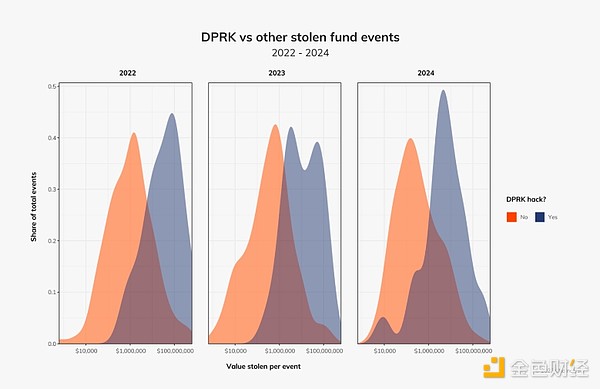
North Korea has been responsible for most large-scale attacks over the past three years. Interestingly, North Korean hackers have a lower amount, especially the density of hacker attacks worth around $10,000 is also increasing.
4. Where is the money used?
North Korea has never admitted to being behind the Lazarus Group, but is considered the only country in the world to use hackers to gain economic benefits.
In 2023, a UN monitoring agency reported that cyber theft accounts for half of the country's total foreign exchange revenue. It is believed that most of the proceeds go to its weapons programs.
Over the past decade, North Korea has incorporated crimes with economic interests into its growing offensive cyber strategy. According to CNBC, the hackers were mainly commanded by North Korea's main foreign intelligence agency, the Reconnaissance General Bureau, [and the stolen funds were used to fund the country's nuclear weapons program.](https://www.cnbc.com/2023/09/06/north-korea-hackers-stole-crypto-to- fund-nuclear-program-trm-chainalysis.html)
In 2020, the United States will include North Koreans suspected of participating in the Lazarus Group on the online wanted list. But unless they leave their country, the chances of these people being arrested are slim.
5. Why is North Korea good at hacking?
In a country where most people have no access to the Internet, why have so many top hackers been cultivated?
Tai Yongho, former Pyongyang ambassador to London who defected to South Korea in 2016, once pointed out that Kim Jong-un spent most of his time studying in Switzerland, but he also saw the importance of computers in modern life. Therefore, after returning to China with his younger brother Kim Jong-chul, their father was inspired. “Kim Jong Il quickly realized the advantages of these computers and networks.”
Kim Jong Il soon set up a specialized school that specializes in teaching high-tech espionage, intelligence and war. Five years later, it received a generous reward: Hackers stole South Korea's top-secret military plans, including documents explaining possible wars between North Korea and its northern neighbors, and a plot to "behead" North Korea by assassinating Kim Jong-un.
Today, North Korea's cyber forces are believed to have more than 8,000 people, most of whom are math geniuses carefully selected from schools. In North Korea, they belong to a harmless “Reconnaissance General Administration”, but in practice, their network codenames include Lazarus, BeagleBoyz, Hidden Cobra and APT38 (“APT” stands for “Advanced Persistent Threat”).
These students have been trained for a long period of high-intensity, but they can also gain certain privileges—including exemption from material benefits such as state-run labor programs, cars and comfortable housing, and rare opportunities to travel abroad, such as participating in global math competitions such as the International Mathematical Olympics.
However, their actions so efficiently are not solely derived from their exquisite technical expertise. Most cyber theft also exploits human weaknesses, such as sending “phishing” emails, making friends with employees, tricking them into revealing passwords, etc.
"North Korea has a very closed system and economy, so they have created a successful hacking and money laundering industry, and they don't care about the negative impressions of cybercrime," said Dr. Dorit Dole of cybersecurity firm Check Point.
Source: Golden Finance, CoinDesk, The Block, The Telegraph, BBC, Reuters, The Economist, Chainalysis, Wikipedia, CNBC


 chaincatcher
chaincatcher

