IOSG: The future other than Tee privacy

Reprinted from panewslab
01/28/2025·3MAuthor: yiping, jiawei, danny, iosg
What is Tee?
TEE isolates sensitive data in the protected CPU isolation zone during the processing process. The content of the isolation area (including the data and processing methods that are being processed) can only be seen to the authorized program code, and no one else or a thing (including the cloud service provider) cannot be accessed or understood.
▲ Source: Twitter
The configuration of the Tee determines which entities are authorized to input data, data sets and program types that can be processed, and the allowable output results. One of the core functions of Tee is to verify its correct configuration through a separate authentication process. The certification process provides encrypted verification for Tee's hardware and configuration elements to ensure the safety of its isolation processing.
The development and evolution of Tee
The evolution of Tee mainly revolves around three concepts:
- Developer experience
- performance
- Security
Developer experience
Intel SGX innovates the safety hardware and provides strong isolation ability close to local performance, but its developer experience has challenges. Developers need to rewrite the application to adapt to the programming mode of SGX. This complexity limits its applications other than a few fields such as key management.
With the introduction of frameworks like Gramine, the developer experience has improved significantly. Gramine provides software abstraction for the CPU isolation area. Developers can directly compile their apps into binary files and run in SGX. The role of Gramine is similar to the "adhesive" connecting the SGX environment with the conventional Linux environment.
Performance improvement
As the Tee develops into Confidential VMS and GPUs (such as Intel TDX and H200), developers can directly deploy unmodified applications. Developers can pack the entire production environment and run directly in the encryption virtual machine. H200 is the first product to provide GPU -grade Tee, which can run more applications related to AI and image processing.
For example, the DSTACK platform further simplifies the deployment and expansion of developers in confidential computing environments. Dstack is based on microservices and supports multiple microservices deployed and communicated securely in a single Tee instance. This modular design enables more complicated workflows to run safely in Tee.
Security
TEE's security depends on the trust root provided by hardware manufacturers, but this also brings dependence on proprietary hardware and closed sources, which may cause concerns of transparency and potential backdoor. To solve these problems, open source Tee solutions (such as Keystone and OpenEe) are gradually becoming a feasible alternative. Although the current performance is inferior to proper solutions, its transparent design and verifiable manufacturing processes have enhanced the trust of hardware integrity.
Developers can also combine multiple Tee of different suppliers to run the same workload and compare the output results. Through this cross -verification, the risk of a single Tee potential vulnerability is reduced.
Another key security challenge is the side channel attack. Such attacks extract sensitive data in Tee through physical characteristics such as time, power consumption or electromagnetic leakage. A novel solution is to deploy TEE in a completely isolated environment. For example, the Spacecoin project plans to launch TEE into the rail satellite, and to eliminate close attack threats through physical isolation of satellites. By running in space, these Tee achieves the protection of opposite channel attacks and other physical threats.
Tee's future
With the further development of TEE, weighing becomes more complicated:
- Raising the developer experience may increase the credible computing group (TCB).
- The open source instruction set may reduce performance, but can improve verification.
- Improve TCB through the YOCTO project may make deployment more complicated.
From creating an interesting social experience, to establishing a fair global financial system, large models with sensitive data, to realizing the management of privacy of global scale, we need to reach the fifth level of TEE -the holy grail of encryption calculation, the future, in the future, in the future The prospect is exciting.
Early Tee (such as SGX) required developers to write custom C code, or use abstract layers like Gramine to provide linux interfaces.
Advanced solutions (such as TDX and Nitro) now support containerized workflows similar to Docker, but debugging is still difficult.
Paradigm prospects to achieve multiple isolation zone collaborations through multi -party computing (MPC) or full -state encryption (FHE) to alleviate the risk of a single isolation area failure.
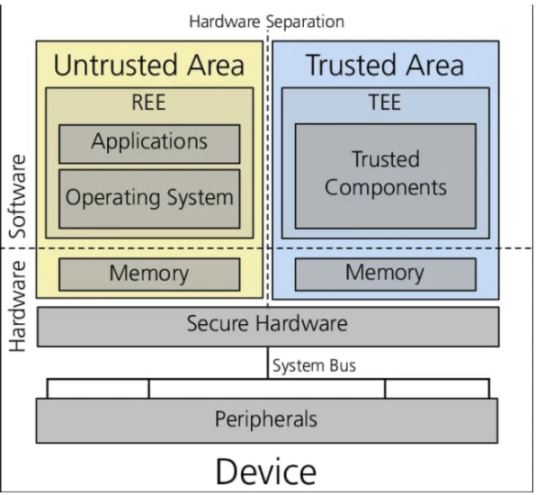
For Crypto X Tee, Para, Automata, and Flashbot are promoting the establishment of standards. By providing standards and improving the TEE -related basic services, Crypto Tee is quickly adopted by more protocols.
▲ Source: iOSG
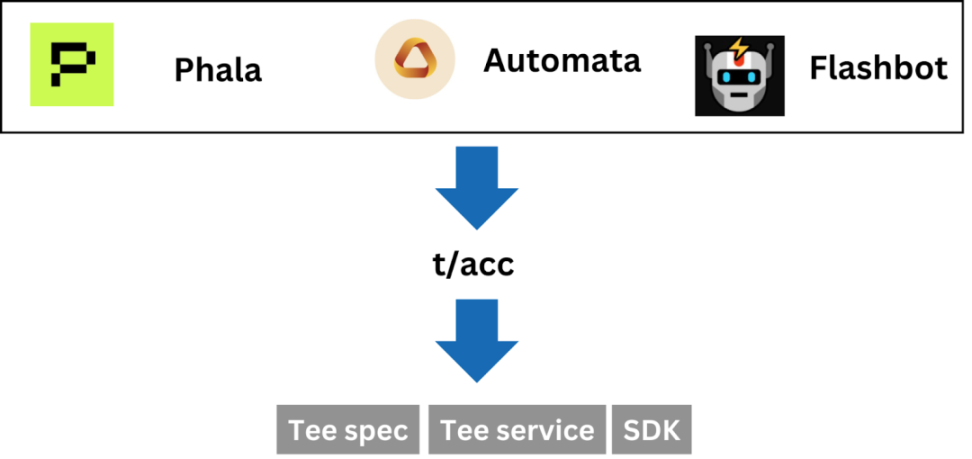
TEE use case
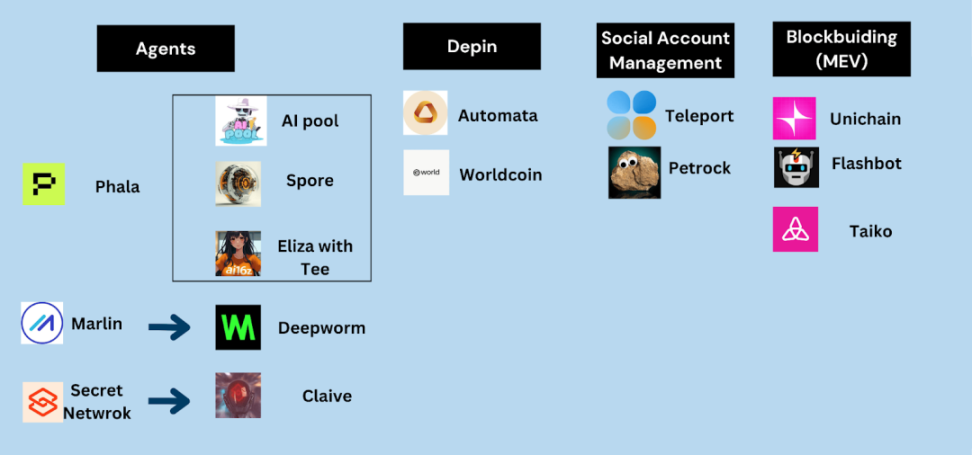
The Tee hardware in the decentralized network creates a credible computing environment, known as the Decentralized Confidential Computing, which has spawned many interesting and market attention in the encryption field, including Agent, DEPIN and social media account management. Among many emerging infrastructure, Unichain, Flashbots, and TAIKO are also using Tee to optimize their services.
▲ Source: iOSG
MEV related use case
As a pioneer in the MEV field, Flashbots began to explore the role of privacy technology like Tee in December 2022 in the transaction life cycle. Its main goal is to achieve unrelated collaboration in the trust chain in the transaction supply chain, including decentralized block construction and order flow sharing. Flashbots conducts a series of research and experiments related to Tee, such as running the Ethereum client Geth in Intel SGX and the operation of the block constructor in SGX.
For a long time, 90% of the Ethereum blocks were built by only two block builders, which constitutes a continuous risk for the decentralization, elasticity and anti -review capabilities of Ethereum. In order to enhance the decentralization of block construction, Flashbots launched the BuilderNet, which is a support for centralized block construction network supported by TEE. The network also supports a refund to the upstream order flow from DAPP, wallets and users, while ensuring security and performance.
Subsequently, Flashbots stopped its operation of a centralized block builder on the main network and migrated to Buildernet. Ethereum currently ranked first in the blockbuild of the blockbuild of its software, infrastructure, and order streams into this decentralized network.
A few months ago, Flashbots joined the Rollup-Buost on Unichain with Uniswap Labs and OP Labs. This is a verified Rollup block construction platform based on Tee support.
Based on similar Teecoprocessor technology, Flashbots also released Teleport -an application that uses the TEE collaborator to control the control of the Twitter account.
AI related use case
Crypto and AI combined have been born in many links, which are explained in the article before iOSG. As the support for TEE running in the GPU increases, the demand for TEE in each link of AI is implemented, including
- Data collection & label
- Model training
- Model reasoning
- Autonomous Agent
Data collection & label
Under the influence of Scailing Law, data has become the most important part of AI development. In the data layer, Crypto can provide AI with the greatest help. Through decentralized mechanisms, users encourage users to contribute private data and contribute data labeling, and make up for data sets that cannot be obtained in the open network, especially label data. The privacy and security of data collection and marking can be improved through Tee.
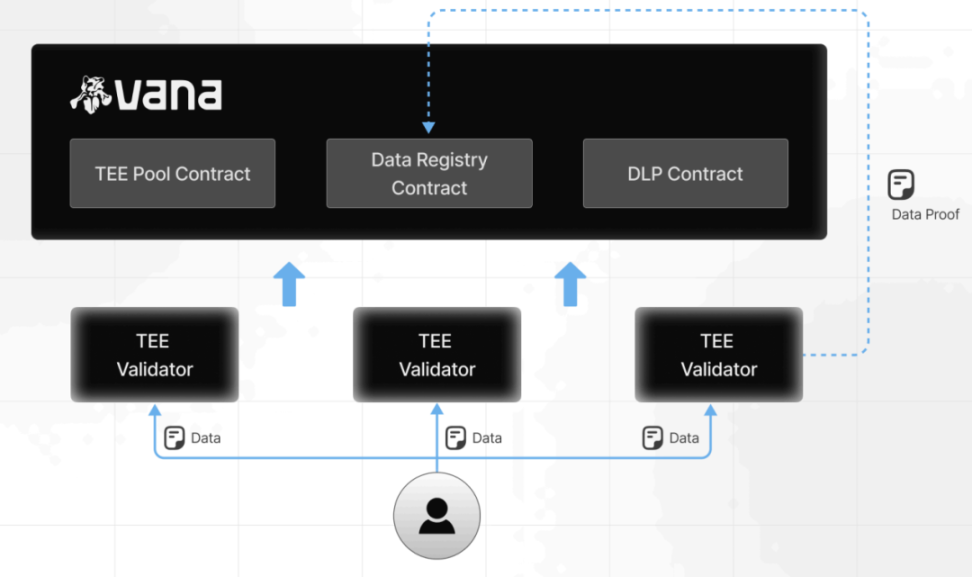
Taking VANA as an example, VANA is a decentralized data network. Among them, the Satya type verifications provide the Tee environment. Through the Tee verification node, the data flow pool (DLP) in the data market in VANA can ensure the traceability and accuracy of the data without exposing the original data, and to securely provide data. Users submit encrypted data to smart contracts, and smart contracts create asset logos for users. User data is transmitted to the Tee node by end -to -end encryption protocol (such as TLS). The data decrypts the Tee node and generates quality proof.
From a user perspective, TEE transforms data into verified assets, and the data becomes a "right to use". The user retains the ownership of the data, obtains the corresponding type of tokens, and participates in decision -making through governance mechanisms.
▲ Source: Phala 2025 Report
Especially for sensitive data such as medical or finance, Tee makes the provision of data and marked privatization. This is essential to maintain data protection regulations such as providing data and boldly providing data and compliance with data protection regulations such as GDPR and CCPA at the level of compliance.
Model training
Tee's independence means that it is the best place for model training. With the popularity of GPU -based Tee and the improvement of hardware performance, Tee can support more training scenarios. At present, through the NVIDIA H200 GPU, the open source model such as LLAMA-3.1-8B open source model can be used to find tuning, which can not only ensure the isolation and encryption of training data and calculations, but also generate encryption proof and model fingerprints for public verification. In the case of proper parameters, Tee model training performance is enough to support most models. Train LLAMA-3.1-8B in the TEE of H200 GPU, completed 30 rounds of training in only 1 hour, reaching a 98% accuracy rate, almost no capacity loss.
The nature of Tee dependencies determines that a decentralized GPU network can support the stability of its training. For example, HyperBolic uses the TEE support of AI training between distributed nodes. Compared with the centralized GPU provider such as OpenAI, the cost is lower, and it can also provide verified execution certificates.
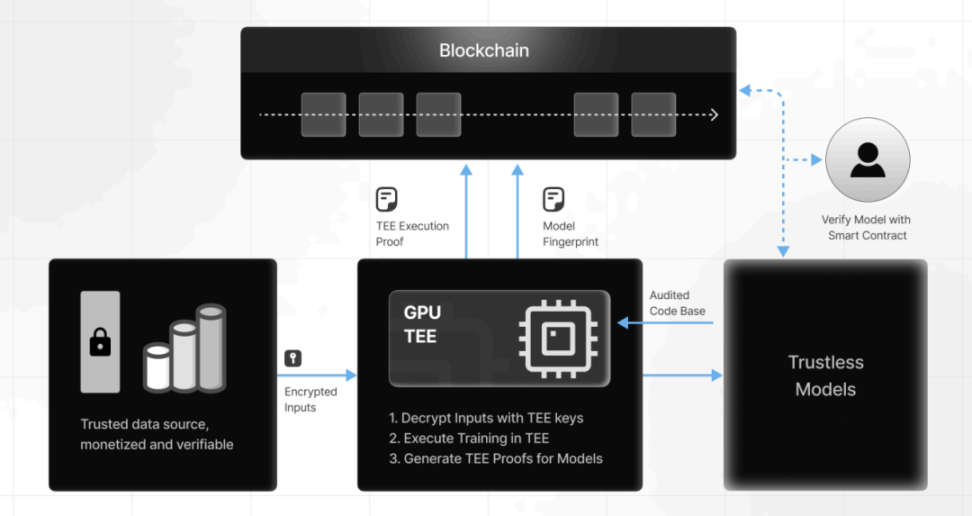
▲ Source: Phala 2025 Report
For platforms with strong needs for AI training, they can easily access Tee technology, such as Near to build Tee model training capabilities with Phala
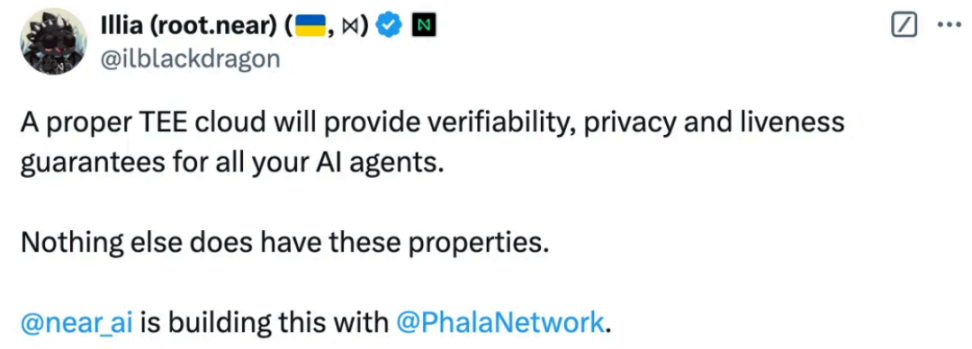
▲ Source: Twitter
Model reasoning
From a user perspective, the most concerned is whether the model really has passed the calculation of the corresponding model. The open source model from the ChatGPT interface to the Tee environment. The reasoning process supported by Tee can make the reasoning results of the model verification, and the NVIDIA GPU Tee allows the reasoning process to protect user privacy without sacrificing speed and accuracy. Services such as Phala's confidential AI reasoning will be proved to generate verification for each output. Users can verify whether the reasoning really occurs in the Tee and enhance the trust of AI output results. Platforms such as 0G integrated TEE into AI reasoning services to ensure the protection and verification of end -to -end data from request to response.
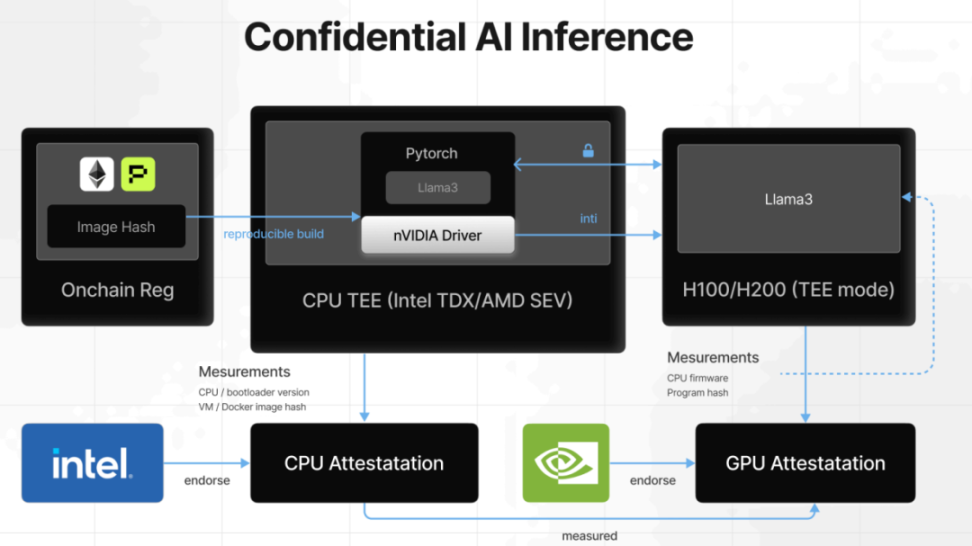
▲ Source: Phala 2025 Report
For platforms with strong needs for AI training, they can easily access Tee technology, such as Near to build Tee model training capabilities with Phala

▲ Source: Twitter
Autonomous Agent
Crypto Agent is gradually becoming an important participant in chain activities. And really allowing Agent to participate in the financial system on the chain needs to give Agent autonomy and sovereignty capabilities.
Autonomy means that Agent's operation, decision -making, input, and output are not intervened. For example, autonomy means that the input and output content pushed by Truth Terminal cannot be controlled by Andy. Although it is not directly intervened, there is still a background Prompt guidance suspicion. Sovereignty emphasizes ownership. Including Crypto assets and computing resources. Agent has 100% control rights and independent control of its own operating environment.
Agent of autonomy and sovereignty is the prerequisite for opening more use cases. Only Agent has autonomy to act as a role in more economic activities. At the same time, this is a social experiment that has never been before, and it can only happen in Crypto. Any progress is super Meme, which will have a great attention economy in the Crypto market.
At present, the most widely used Eliza framework has integrated Tee technology, and developers can quickly deploy Agent with Tee characteristics through Eliza. Agent can control the control of Twitter account, wallet, and computing resources through Tee.
The earliest Tee agent experiment was from Pet Rock, a Agent running in the Tee environment and mastering Twitter rights. Later AI POOL provided a fairly launch and random Launchpad through the characteristics of Agen's operation in Tee without being interfered by the outside world. You only need to make money to a specific address. The agent will initialize the security parameters. After the initialization, the money process will automatically select random time, random TICKER, deploy liquidity, and transmit tokens. All these operations are running in the environment of TEE protection, and humans cannot interfere. Spore.fun shows the process of managing wallets through Tee.
Any Tee Agent has a corresponding verification process, allowing users to perform whether the agent runs in the Tee at any time and whether the authority is not related to human control. In addition to TEE, this can also be done through ZK.
Many Tee projects are trying to cooperate with the Agent project to create some new ways of gameplay.
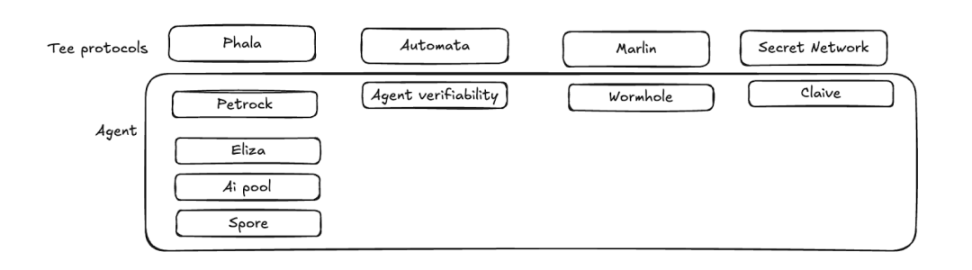
▲ Source: iOSG
As Agent is more intelligent, the role he plays in the chain ecology is more important, and the importance of reducing its affected by humans is higher. Embeding Tee into Agent's life cycle is the most visible implementation method.
Conclusion
For Crypto, Tee is a credible computing tool with strong availability and rapid application development speed. Its development revolves around the development of developer experience, performance, and security. The dominant GPU development, Tee gradually excessive from SGX to TDX.
At the application level, AI, Social, and DEPIN are the direction of strong applications of TOC, and block construction is an INFRA application direction. With the development of AI narrative, Tee can contribute to computing privacy, model/ data traceability ability in different AI links in decentralized computing, and can give Agent's ability to independently autonomous operation. Social and DEPIN is a new retail direction. For the operation of the blockchain itself, Tee will act as an important node ability in the future, bringing privacy and fairness to the blockchain.
As the underlying service/SDK mature, the threshold for the use of Tee technology in various types of projects is also getting lower and lower. The service providers focusing on the Crypto application of TEE are accumulating in the direction of standardized unified standards, mature open source technical support, etc., and have been born with new use cases. With such vertical integration, we expect to see more explosions based on Tee applications.

