Tee concise manual: from basic concept to the best practical guide for safe use

Reprinted from panewslab
01/28/2025·3MOriginal title: Securing Tee Apps: A Developer's Guide
Original author: Prateek, Roshan, Siddhartha & Linguine (Marlin), Krane (Asula)
Compilation: Shew, Xiayang Godrealmx
Since Apple announced the launch of private clouds and NVIDIA with confidential calculations in the GPU, the trusted execution environment (Tee) has become more and more popular. Their confidential guarantee helps protect user data (may include private keys), and isolation ensures that the execution of the program deployed on it will not be tampered with -whether it is humans, other programs or operating systems. Therefore, it is not surprising that the use of Tee to build products in the Crypto X AI field is not surprising.
Like any new technology, Tee is experiencing an optimistic experiment. This article hopes to provide basic conceptual guidelines for developers and general readers, so that they can understand what Tee, Tee's security models are, common vulnerabilities, and the best practice of using Tee safely. (Note: In order to make the text easy to understand, we consciously replaced the TEE term with simpler equivalent words).
What is Tee
Tee is an isolation environment in the processor or data center. The program can run in it without any interference in the rest of the system. In order to avoid interference by other parts, we need a series of designs, which mainly include strict access control, that is, other parts of control systems and data access in Tee. At present, Tee is ubiquitous in mobile phones, servers, PCs, and cloud environments, so it is very easy to access and the price is reasonable.
The content of the above may sound vague and abstract. In fact, different servers and cloud suppliers implement Tee methods, but their fundamental purpose is to avoid the Tee interference by other programs.
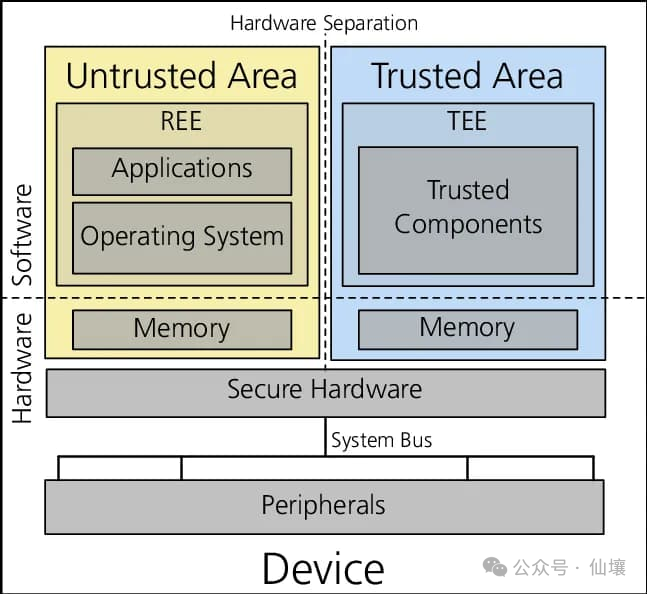
Most readers may log in to the device with biometric information, such as unlocking mobile phones through fingerprints. But how do we ensure that malicious applications, websites or jailbreak operating systems cannot access and steal these biometric information? In fact, in addition to encrypted data, the circuit in the TEE device does not allow any program to access the memory and processor area occupied by sensitive data.
Hardware wallet is another example of the Tee application scenario. The hardware wallet is connected to the computer and communicates with it, but the computer cannot directly access the notes stored in the hardware wallet. In the above two cases, users believe that equipment manufacturers can correctly design chips and provide appropriate firmware updates to prevent confidential data in Tee from being exported or viewed.
Security model
Unfortunately, there are many types of Tee implementation. These different implementations (Intelsgx, InteltdX, AMDSEV, AWSNITROENCLAVES, and ARMTRUSTZONE) all need independent security model modeling analysis. In the rest of this article, we will mainly discuss IntelSGX, TDX and AWSNITRO, because these Tee systems have more users and have complete available development tools. The above system is also the most common Tee system in Web3.
Generally speaking, the workflow of applications deployed in Tee is as follows:
- "Developers" wrote some code, these code may have been open source or there may be no
- Then, the developer packs the code into the ENCLAVE image file (EIF), and the file can run in the Tee
- EIF is hosted on a server with a Tee system in a certain stage. In some cases, developers can directly use personal computer custody EIF with Tee to provide services outside
- Users can interact with the application through a predefined interface.
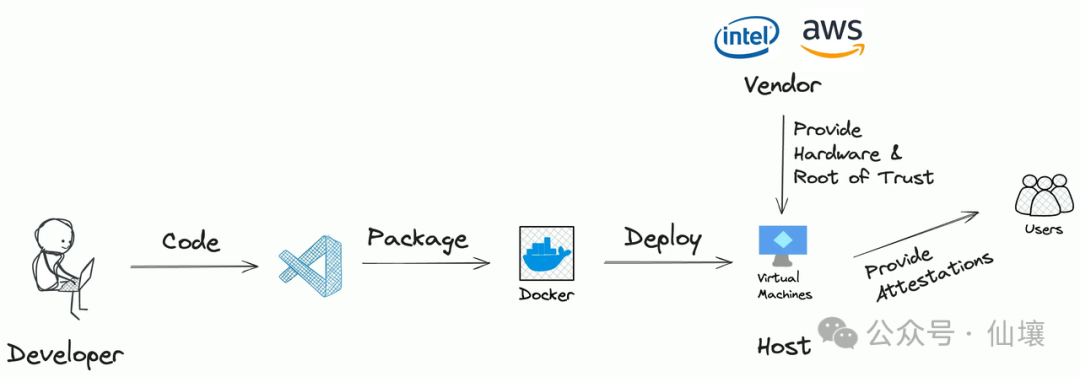
Obviously, there are 3 potential risks:
- Developers: What is the role of code for preparing EIF? The EIF code may not meet the business logic of the project party's external publicity, and may steal the privacy data of users
- Server: Is the Tee server running an EIF file that is consistent with expected? Or is EIF really executed in Tee? The server may also run other programs in Tee
- Supplier: Is the design of Tee safe? Are there any data in the back door leaking all data to the supplier?
Fortunately, the current TEE already has a plan to eliminate the above risks, and you can repeat the reproducible builds and remote provers.
So what is repetitive construction? Modern software development often needs to introduce a large number of dependencies, such as external tools, libraries or frameworks, etc. These dependent documents may also have hidden dangers. Now the NPM and other solutions use the code hash corresponding to the dependent file as the unique identifier. When NPM finds that a dependent file is inconsistent with the hash value of the record, it can be considered that the dependent file has been modified.
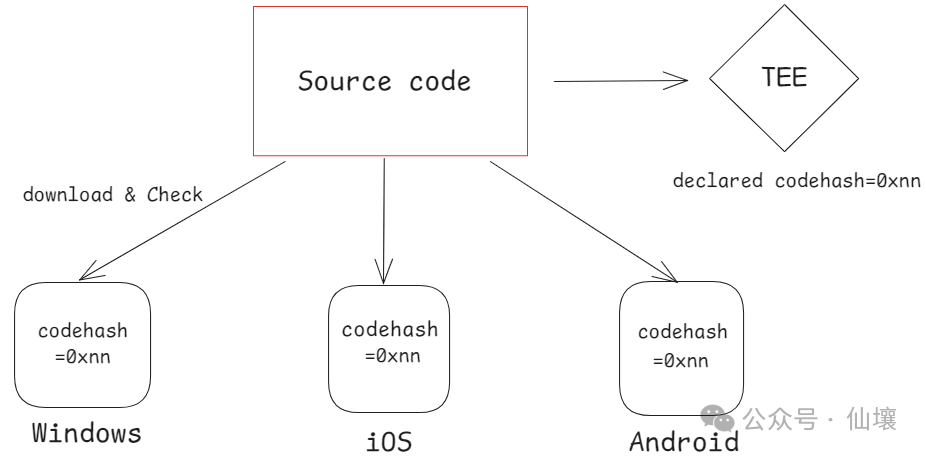
The repetitive construction can be considered a set of standards. The goal is that when any code runs on any device, as long as it is constructed in accordance with the processes specified in advance, you can eventually get a consistent hash value. Of course, in practice, we can also use the products other than hash as the identifier. Here we call it code measurement.
NIX is a commonly used tool that can be repeatedly constructed. When the source code of the program is made public, anyone can check the code to ensure that the developers have not inserted abnormal content. Anyone can use Nix to build code to check whether the product constructed is the same as the product deployed in the production environment in the production environment. Code measurement/hash. But how do we know the code measure value of the program in Tee? This involves the concept called "remote certificate".
Remote proof is a signature message from the Tee platform (trusted party), which contains the code measure value of the program, the Tee platform version, etc. Remote proof lets external observer know that a program is executed in the security location (XX version of the XX version) that can be accessed.
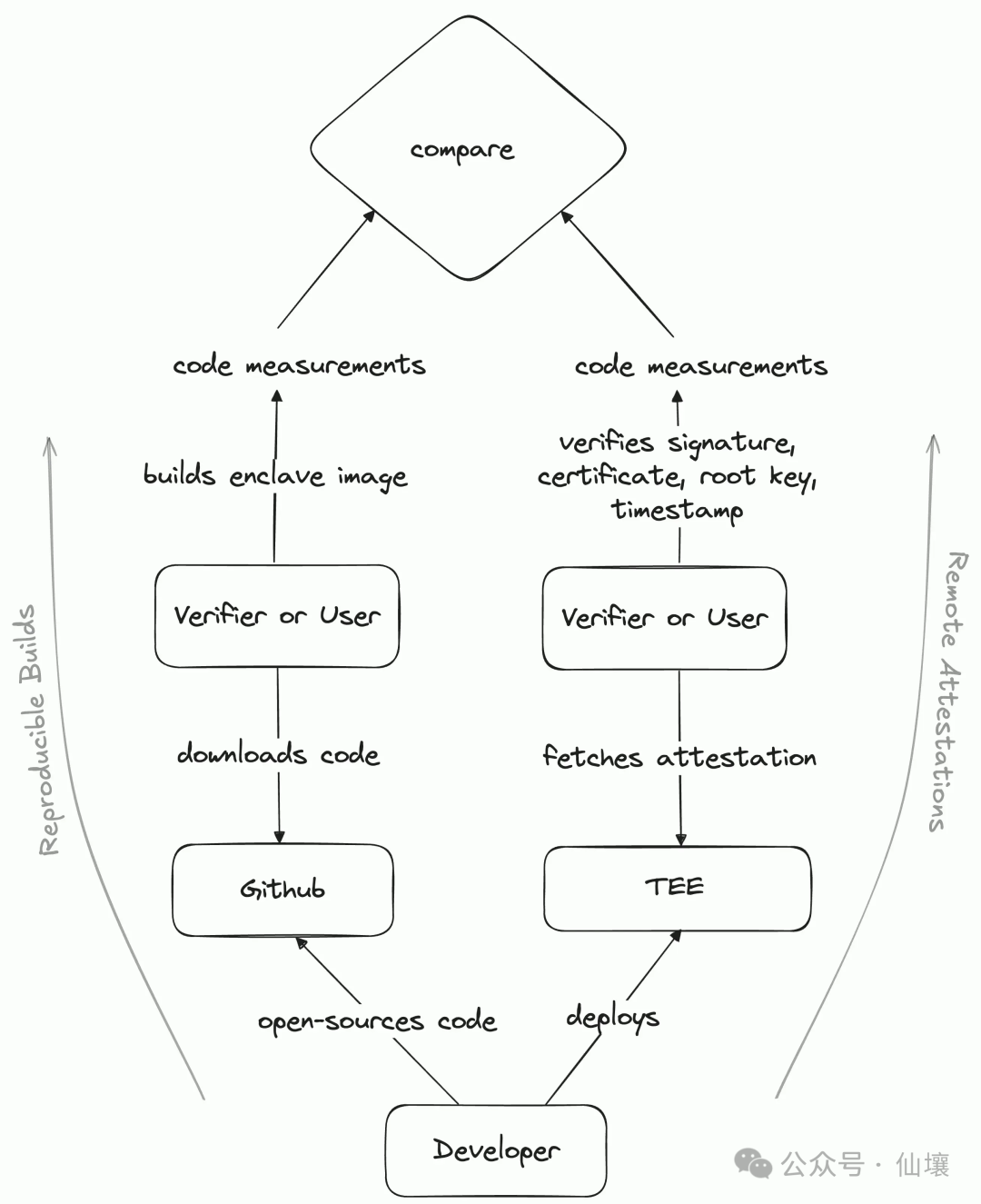
Can be repeatedly constructed and remote proofs allow any user to know the actual code and Tee platform version information running in Tee, thereby preventing developers or servers from evil.
However, in the case of Tee, it always needs to trust its suppliers. If the Tee supplier is evil, it can directly forge remote proof. Therefore, if the supplier is regarded as a possible attack medium, it is best to avoid relying only on Tee, and it is best to combine them with the ZK or consensus agreement.
Tee's charm
In our opinion, Tee's particularly popular characteristics, especially for the deployment friendship of AI Agent, mainly the following points:
- Performance: Tee can run the LLM model, and its performance and cost overhead are similar to ordinary servers. And ZKML needs to consume a lot of computing power to generate the ZK certificate of LLM
- GPU support: NVIDIA provides Tee computing support in its latest GPU series (Hopper, Blackwell, etc.)
- Correctability: LLMS is non -definitivity; entering the same prompt multiple times will get different results. Therefore, multiple nodes (including observer trying to create a scam certificate) may never reach a consensus on the operation results of LLM. In this scenario, we can trust the LLM that runs in Tee cannot be manipulated by the evil. The program in the Tee is always running according to the writing method, which makes the Tee more suitable for the reliability of the LLM reasoning results than OPML or consensus.
- 保密性:TEE中的数据对外部程序不可见。 As a result, the key to generated or received in Tee is always safe. This feature can be used to ensure that any message signed by the key comes from the internal program of Tee. Users can rest assured that the private key can be tube to Tee and set some signature conditions, and can confirm that the signature conditions set pre -set from Tee
- Networking: Through some tools, procedures running in Tee can safely access the Internet (no need to disclose or respond to the server running the Tee, and at the same time, it can still provide the correct data retrieval guarantee for third parties). This is very useful for searching information from a third -party API. It can be used to outsourcing the calculation to the trusted but proprietary model provider
- Write permissions: Contrary to the ZK scheme, the code running in the Tee can build messages (whether it is tweets or transactions) and send them out through the API and RPC network
- Developers are friendly: Tee -related frameworks and SDK allows people to write code in any language, and easily deploy programs in the cloud server like a cloud server
Regardless of whether it is good or bad, it is difficult to find a alternative to use the use case of Tee. We believe that the introduction of Tee further expands the development space of applications on the chain, which may promote the emergence of new application scenarios.
Tee is not a silver bomb
Programs running in Tee are still easily affected by a series of attacks and errors. Just like smart contracts, they are easy to encounter a series of problems. For simplicity, we classify the possible vulnerabilities as follows:
- Developer negligence
- Runtime vulnerability
- Architecture design defect
- Operating issue
Neglect of developers
Whether intention or unintentional, developers can weaken the security guarantee of the program in Tee through intentional or unintentional code. This includes:
- Occupible code: TEE's security model depends on external verification. The transparency of the code is essential for verification of external third parties.
- There is a problem with code measurement: Even if the code is public, if there is no third -party re -constructing code and checking the code measure value in the remote certificate, and then check according to the code measurement provided in the remote certificate. This is similar to receiving ZK proof but not verified.
- Unsafe code: Even if you carefully generate and manage the key in Tee, the logic contained in the code may leak the key in the Tee during the external call process. In addition, the code may contain back doors or vulnerabilities.与传统后端开发相比,它要求软件开发和审计过程具有高标准,类似于智能合约开发。
- 供应链攻击:现代软件开发使用大量第三方代码。供应链攻击对TEE的完整性构成重大威胁。
Runtime vulnerability
No matter how cautious developers, developers may become villains at the time of runtime. Developers must carefully consider whether the following items will affect the security guarantee of the project:
- Dynamic code: It may not always be transparent to all code. Sometimes, the use case itself needs to dynamically execute the opaque code loaded to the Tee during the runtime. This type of code is easy to leak secrets or destroy the variables, and this kind of situation must be carefully prevented.
- Dynamic data: Most applications use external APIs and other data sources during execution. The security model is extended to these data sources. These data sources are in the same position as the prophecy aircraft in DEFI, and incorrect or even outdated data may cause disaster. For example, under the use case of AI Agent, over -reliance on LLM services, such as Claude.
- Unsafe and unstable communication: Tee needs to run in a server containing Tee components. From a security point of view, the server running Tee is actually a perfect intermediate person (MITM) between Tee and external interaction. The server can not only peep at the external connection of Tee and check the content being sent, but also examine specific IPs, restrict connections and inject data packets in the connection. It aims to deceive one side to make it think that it comes from XX.
For example, running in TEE can handle the matching engine that can handle encrypted transactions. The engine cannot provide fair sorting guarantees (anti -MEV), because router/gateway/host can still discard, delay or prioritize according to the IP address of the data packet source.
Architectural defect
The technology stack used by the Tee application should be cautious. When constructing a TEE application, the following problems may occur:
- Applications with a large attack surface: The attack surface of the application refers to the number of code modules that need to ensure a completely secure code module. The code with a large attack surface is very difficult to audit and may hide bugs or available vulnerabilities. This usually conflicts with the experience of developers. For example, compared with the TEE program that does not depend on Docker, the TEE program attack relying on Docker is much larger. Compared with the Tee program that uses the lightest operating system, Enclaves, which depends on the mature operating system, has a greater attack surface
- Transplantability and activity: In Web3, applications must be anti -review. Anyone can start Tee and take over unrealistic system participants, and enable applications in Tee to be transplanted. The biggest challenge here is the portability of the key. There is a key derived mechanism in some Tee systems, but once the key derived mechanism in the Tee is used, then other servers cannot generate the key in the external Tee program locally, which makes the Tee program is usually limited to the same machine. This is not enough To maintain transplantation
- Unsafe trust root: For example, when running AI Agent in Tee, how to verify whether the given address belongs to the agent? If you do not design it carefully, it will cause the real trust to be an external third party or a key custody platform, not the Tee itself.
Operating issue
In the end, it is not the most unimportant point that there are some actual precautions for how to truly run a server to execute the Tee program:
- Unsafe platform versions: Tee platform occasionally receive security updates. These updates will be reflected as platform versions in the remote certificate. If your TEE is not running on the security platform version, hackers can use the known attack medium to steal the key from the Tee. To make matters worse, your Tee may run on a safe platform version today, and it may be unsafe tomorrow.
- There is no physical security: Although you have done their best, Tee may be attacked by side channels, and people usually need physical access and control of the server where Tee is located. Therefore, physical security is an important deep defense layer. A related concept is that cloud proves that you can prove that Tee is running in the cloud data center, and the cloud platform has physical security assurance.
Build a safe Tee program
We divide our suggestions into the following points:
- The safest solution
- The necessary prevention measures taken
- Proposal dependence on use cases
1. The safest solution: no external dependencies
Creating a highly secure application may involve eliminating external dependencies, such as external input, API or services, thereby reducing the attack surface. This method ensures that the application is running independently, and it is not possible to damage external interaction with integrity or security. Although this strategy may limit the diversity of the program, it can provide extremely high security.
If the model is running locally, it can achieve this level of security for most Cryptoxai use cases.
2. The necessary prevention measures taken
Regardless of whether the application has external dependencies, the following content is necessary!
Take the Tee application as a smart contract, not a back -end application; keep a lower update frequency and strictly test.
The construction of the TEE program should be as strict as when writing, testing and updating smart contracts. Like smart contracts, TEE runs in a highly sensitive and unable to tamper. The error or accidental behavior may lead to serious consequences, including complete losses of funds. Thorough audit, extensive testing, and minimum, carefully audit updates are essential to ensure the integrity and reliability of Tee -based applications.
Audit code and check the construction pipeline
The security of the application depends not only on the code itself, but also the tools used in the construction process. Safety constructing pipelines are essential to prevent vulnerability. TEE only guarantees that the code provided will run according to the expected process, but it cannot repair the defects introduced during the construction process.
In order to reduce the risk, the code must be strictly tested and audited to eliminate errors and prevent unnecessary information leakage. In addition, it can be repeatedly constructed to play a vital role, especially when the code is developed by one party and used by the other. It can be repeatedly constructed whether the program that allows anyone to verify the Tee is matched with the original source code to ensure transparency and trust. If there is no repeated construction, it is almost impossible to determine the exact content of the execution program in the Tee, which endangers the security of the application.
For example, the source code of Deepworm (project running a worm brain simulation model in Tee) is completely open. The execution program in the Tee is constructed using the NIX pipe to be reappeared.
Using audited or verified libraries
When processing sensitive data in the Tee program, please use the audited library for key management and private data processing. Unexpected libraries may expose the keys and damage the security of the application. Priority considering the full review and security -centric dependencies to maintain the confidentiality and integrity of the data.
Always verify proof from Tee
Users who interact with Tee must verify the remote certification or verification mechanism generated by Tee to ensure safe and credible interaction. Without these inspections, the server may manipulate the response, which cannot distinguish the real Tee output and tampered data. Remote proof provides key proofs for code libraries and configurations running in TEE. We can judge whether the program executed in Tee is consistent with expected based on remote proof.
Specific verification can be verified on the chain (Intelsgx, AWSNITRO), using ZK (Intelsgx, AWSNITRO), or the user or hosting service (such as T16Z or MarlinHub).
3. Proposal dependence on use cases
According to the target use case and structure of the application, the following prompts may help make your application more secure.
Make sure that the interaction between users and Tee in the security channel is always
The server where the Tee is located is essentially trusted. The server can intercept and modify communication. In some cases, the server reads data but does not change the data may be acceptable, and in other cases, even reading data may not be desirable. In order to reduce these risks, it is important to establish a secure end -to -end encryption channel between users and Tee. At least, please make sure the message contains the signature to verify its authenticity and source. In addition, users need to always check Tee to give remote proofs to verify whether they are communicating with the correct Tee. This ensures the integrity and confidentiality of communication.
For example, Oyster can support safe TLS by using CAA records and RFC8657. In addition, it also provides a TEE native TLS protocol called scallop, which does not depend on Webpki.
Knowing that Tee memory is instantaneous
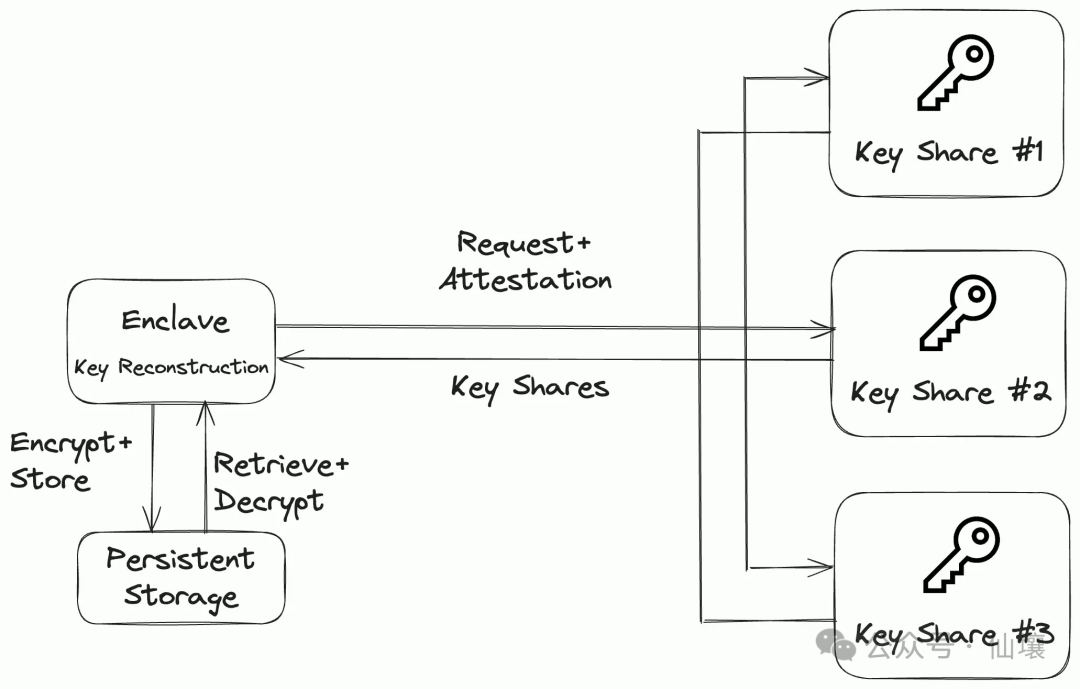
Tee memory is transient, which means that when the Tee is closed, the content (including the encryption key) will be lost. If there is no security mechanism to save this information, the key data may be unable to access it permanently, which may cause funds or operations to be in trouble.
Multi -party computing (MPC) networks with IPFS such as IPFS can be used as solutions for this problem. The MPC network splits the key to multiple nodes to ensure that no single node holds a complete key, and at the same time allows the network to rebuild the key when needed. Data using this key can be securely stored on IPFS.
If necessary, the MPC network can provide a key to the new Tee server running the same image, provided a key to meet specific conditions. This method ensures elasticity and strong security, and data accessibility and confidentiality can be maintained even in unwilling environments.
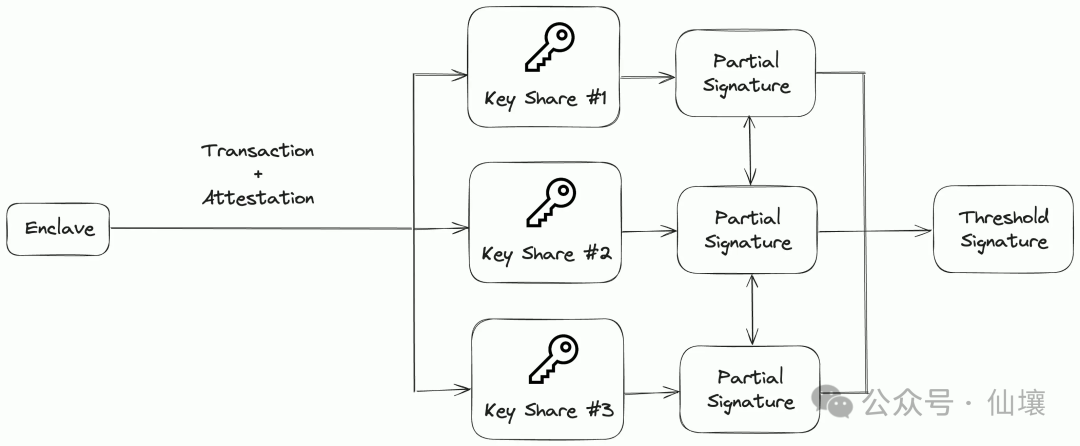
There is another solution, that is, Tee handed over the relevant transactions to different MPC servers. The MPC server signed the aggregation signature and the transaction was finalized. The flexibility of this method is much lower and cannot be used to save the API key, password or any data (no trusted third -party storage services).
Reduce the attack surface
For cases of safety key types, it is worth trying to reduce peripheral dependencies at the cost of sacrificing developers at the cost. For example, DSTACK comes with a minimum kernel based on YOCTO, which contains only modules required for DSTACK work. It may even be worth using old technologies like SGX (more than TDX), because this technology does not need to guide loading programs or operating systems to become part of TEE.
Physical isolation
By physical isolation with possible human intervention, the security of Tee can be further enhanced. Although we can host the Tee server in data centers and cloud providers, I believe that data centers can provide physical security. But projects like Spacecoin are exploring a quite interesting alternative -space. Spacetee's thesis relies on security measures, such as measuring the inertia after the launch to verify whether the satellite is deviated from the expected process in the process of entering the orbit.
Multiple proofer
Just as Ethereum relies on multiple client implementation to reduce the BUG risk that affects the entire network, Multiprovers uses different Tee implementation schemes to improve security and elasticity. By running the same calculation steps across multiple Tee platforms, multiple verifications can ensure that vulnerabilities in a certain Tee implementation will not endanger the entire application. Although this method requires that the calculation process is certain, or define the consensus between different Tee implementation schemes under non -confirmation, it also provides significant advantages such as faulty isolation, redundancy and cross -verification, making it a reliable reliability that needs to be reliable A good choice for applications for sexual guarantee.

Look forward to the future
Tee has obviously become a very exciting field. As mentioned earlier, the continuity of AI's ubiquitous access to user -sensitive data means that large technology companies such as Apple and NVIDIA are using Tee in their products and provided Tee as part of its products.
On the other hand, the encrypted community has always paid great attention to safety. As developers try to expand the application and use cases, we have seen that Tee becomes popular as a solution that provides correctly weighing solutions between functional and trust assumptions. Although TEE is not as trusted as a complete ZK solution, we expect Tee to be the first time that TEE will slowly integrate Web3 and large technology companies products.



 chaincatcher
chaincatcher