Advanced Airdrop Strategy: The Law of Survival of Penetrating the Witch's Mist

Reprinted from chaincatcher
02/18/2025·2MAuthor: 0x Lao Dong
Core rules for project parties to filter users
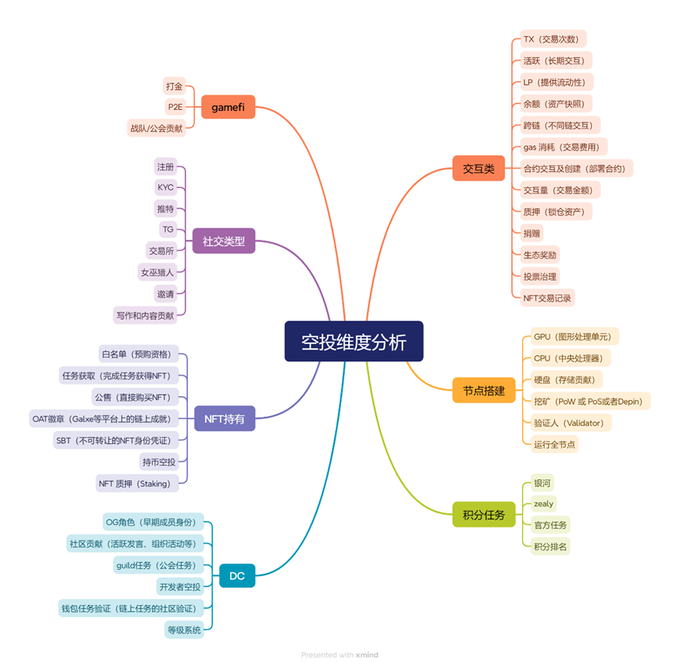
When designing airdrop strategies, project parties rarely screen on a single standard, but instead evaluate the quality of users from multiple dimensions to ensure that airdrops can be distributed to truly valuable addresses. From the perspective of the project party, they most prefer high TVL, high net worth users , and real active users who can participate in ecological construction for a long time . Based on these principles and combined with the strategies of historical airdrop projects, Lao Dong summarized several core screening dimensions.
1. Interaction category filtering criteria
-
Number of transactions, transaction volume and activity : reflects the user's activity on the chain. Frequent transactions and in-depth interactions indicate that the user has a certain investment in the ecosystem, but excessive data may also be a volume-brushing behavior. For example, Starknet W does more mistakes
-
Gas consumption : The total transaction fee paid by the user can indirectly reflect their actual participation and actual contribution. For example, Zkfair, which uses gas consumption to distribute the current morph, and provides points through gas
-
Contract interaction & creation : can be used to measure whether users participate in multiple ecological projects, helping to distinguish between real users and simple brushing users. For example, arb zksync has weighted the number of contract interactions
2.NFT & Assets Screening Criteria
-
Whitelist, public sale, task acquisition : Generally, such NFTs are limited and can control deflation. As a certificate of airdrop, it also means that users have a high degree of participation in the project. For example, XAI all issue airdrops based on NFT.
-
OAT badge and SBT : As an on-chain achievement or non-transferable identity credential, it can effectively prove the user's long-term contribution and true participation. For example, Odos' pilot OAT and Linea's LXP
-
Coin holding airdrop, NFT pledge : Holding tokens or pledging NFT not only shows the user's trust in project assets, but may also bring additional incentives, and also helps evaluate users' asset quality and risk control. For example, MOCA and PENGU's NFT airdrop tokens.
3. Points Tasks and Task Platform
-
Points accumulative and ranking : Complete tasks through platforms such as Galxe, Zealy or the official itself to obtain points. The higher the points, the higher the participation; at the same time, the ranking of points can be used as an important basis for airdrop allocation. For example, IO's Galaxy Points Mission, SCA's Points Airdrop, and many LSD projects' Points Airdrops.
-
Cross-ecological tasks : Users are required to complete tasks on multiple platforms or ecology, and more comprehensively evaluate the overall activity and ecological contribution of users. For example, many Odyssey tasks, move, and linea need to complete many ecological tasks to obtain rewards.
4. Community and social contributions
-
Twitter/Discord/Telegram active : users complete social tasks in the community, post tweets, etc., or DC, TG speak, participate in discussions, help socialize to do some translations, etc., thereby obtaining the corresponding identity. This type of task is relatively complex and has Higher airdrop value. For example, the current kaito gets points through Twitter interactions, etc., and the move's gorilla character is worth thousands of U.S. dogs issues airdrops based on TG's account age and activity.
-
Early Membership (OG Roles) and Invitation Contribution : Users who join early or get new recruits are more likely to receive airdrops to inspire long-term participation, such as the IP OG Roles have several thousand tokens airdrops.
-
Content creation and social media interaction : Promotion and discussion on platforms such as Twitter, Medium, YouTube, etc. help project dissemination, and also reflect users' sense of identity with the project. For example, the creator role of move.
5. Node construction and technical contribution
- Full nodes, mining, and verifiers : Technical participation in the operation of nodes, participation in mining or serving as verifiers, directly supporting network security and performance is a contribution that the project party attaches great importance to. For example, the IO worker uses GPU to mine points, the nillion node runs through the CPU, and the grass obtains points through IP and traffic.
6. GameFi and entertainment interaction
-
Gold-making, P2E : Earning tokens through in-game tasks in the GameFi project not only reflects the user's participation, but also shows the user's dependence on the project entertainment ecosystem. For example, CATI raises cats to make money tokens. Bigtime bigtime game to earn tokens.
-
Offensive and Defensive Confrontation: Witch Detection Anatomy and Counterattack Strategy
Project party’s witch identification strategy
According to data analysis in the previous article, among the 100 projects in 2024, the proportion of witches who were clearly checked reached 32%.
In the airdrop activity, the project party checks the core essence of the witches and is also a means of screening, filtering out high-quality, real and large-contribution addresses , and avoiding the airdrops being occupied by large-scale and low-quality addresses. It is not just for the studio, even individual users. It may be regarded as a witch address because of the inability to continue interaction, just like the project party constantly optimizes the screening rules, there are still studios that can get good results. Therefore, understanding the methods of checking witches and adopting corresponding defensive strategies is the key to ensuring that good results can be obtained. Here Lao Dong lists some more obvious types of witch risks.
Witch Defense Tactics Manual
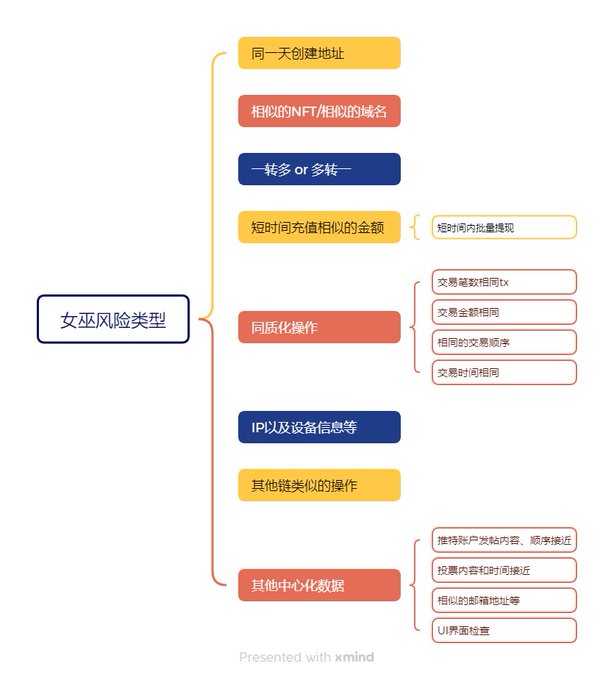
1. Address creation & capital flow abnormality
The project party will give priority to checking the creation time, recharge path, and fund collection of addresses. Such address aggregation behavior is the most likely way to be investigated. The main methods include:
-
Create multiple addresses on the same day: If a large number of new addresses are created and recharged on the same day, they are easily marked as batch witch accounts.
-
One transfer or Multiple transfer: Transfer money to multiple small accounts at the same address, or the funds from multiple addresses are collected into the same wallet, which is considered to be an abnormal fund allocation.
-
Recharge similar amounts in a short time: If multiple addresses recharge the same amount or close to the amount at similar times, they may be determined to be operated by the same controller.
-
Batch withdrawal in a short time: If funds from multiple addresses are withdrawn to the same wallet at the same time, it is a high-risk behavior.
Prevention strategies:
-
When creating a new address, create a small number of accounts every day and randomly select the recharge time to avoid centralized operations.
-
Use CEX (Binance, OKX, etc.) sub-accounts as transfer stations to avoid direct collection on the chain.
-
Randomize the amount and time of funds recharge to avoid batch operations in fixed amounts and fixed time.
-
When withdrawing, set aside the time interval and try to withdraw with sub-addresses of different CEXs.
2. Anomalies of on-chain interaction behavior
The project will analyze the interaction mode of the address. This type is collectively called homogeneous interaction, focusing on the following behaviors:
-
Similar NFT or Domain Name: If multiple addresses receive the same NFT or Domain Name, it is easily recognized as a batch operation.
-
The number of transactions is similar: the number of interactions between multiple addresses and the interaction contracts are similar, and it is easily judged as a robot operation.
-
Same transaction order & transaction amount: If the interaction order, amount, and transaction object of the address are the same, it is likely to be recognized as a batch account.
-
Fixed time interaction: If the interaction time of multiple addresses is concentrated in a certain period of time (for example, completing the task within 24 hours), the risk is higher.
Prevention strategies:
-
Use different accounts to complete different tasks, open up interaction time, and avoid performing the same operations at the same time.
-
Insert "smoke bomb projects" during interaction, such as participating in some DEX interactions, lending and other low-cost dapps, making the on-chain behavior more natural.
-
Randomly interact with different contracts. Do not interact with the same DEX, bridge, or contracts for all accounts, and select some addresses to interact with some contracts.
-
Time interaction is 24 hours a day, and random time interaction is not fixed time batch synchronization operations.
3. IP and off-chain data analysis
In addition to on-chain data, the project will also analyze IP addresses, UI interface interactions, browser fingerprints, and social media data to screen the witch through off-chain data:
-
Same IP / Same Device: If multiple accounts use the same IP or the same browser fingerprint, the risk of being detected as the same person is operating extremely high.
-
Similar social media behavior: If the posting content, like order and interaction mode of multiple Twitter accounts are similar, it is easy to be excluded by the project party. DC is not active and kicked out by the channel.
-
Email association: Multiple accounts use similar mailbox naming rules, which may trigger risk control.
-
UI interface check: Directly interact through contracts, without interacting in the project's UI interface, some projects will trigger risk control such as electric sheep
Prevention strategies:
-
Use proxy IP and fingerprint browser to change device information.
-
Pay attention to the randomness of social interaction when raising an account and avoid homogeneous content.
-
Register with different email addresses to avoid overly similar email addresses.
-
Try to use front-end interactive scripts to avoid being checked on the UI interface
Gradient strategy: reasonably allocate accounts to reduce the risk of
detection and killing
In order to improve the success rate of airdrops, it is recommended to adopt a gradient strategy to divide accounts of different categories to avoid being blocked by consecutive seats using the same model. At present, project parties are increasingly favoring high-quality numbers. The lowest and highest addresses of ZK are rewarded with a reward of 100 times, and the STRK is 20 times, and the ARB is 16.32 times. From ZK, you can make 100 high-quality accounts, which is equivalent to the income of 100 minimum living allowance accounts. It can reduce energy in operation and also reduce the risk of witches. But at the same time, the minimum living allowance number and the lottery number must also be available. For example, Tensor, Magic Eden is the victory of the minimum living allowance number, and HMSTR is the victory of the lottery number, with the sun shining. Different strategies are chosen, and the final result is completely different.
Premium number (regardless of cost, key account maintenance) - All dimensions reach at least the top 1%
-
High-quality interaction, participate in multiple ecology, bind social accounts, and provide human nature proofs such as gitcoin.
-
Personal use of wallets, small but high-quality products, improve the contribution of the on-chain ecosystem.
-
Simulate real user behavior, operate for a long time, and avoid airdrops at one time.
Minimum insurance number (minimum airdrop threshold, moderate operation) - all dimensions reach at least the top 20%
-
Only participate in core airdrop missions, and do not perform obvious witch operations.
-
Trading in moderation to avoid excessive frequent or regular interactions.
Lottery number (batch number, low-cost trial and error)
-
Only do simple and cost-effective tasks and strictly control costs.
-
A more radical and unrestrained strategy may be adopted, but it will not affect the main account.
Conclusion
In the current environment of rapid development of AI+ chain analysis technology, witches’ detection methods are becoming more and more accurate, and simple batch operations are difficult to work.
Therefore, for the studio, witch operations need to have higher randomness and real-person simulation, and at the same time, it is necessary to flexibly adjust the strategy, combining gradient accounts, dispersed interactions, and optimizing fund paths to reduce the probability of being banned.
For individuals, if they do not have the operational capabilities of the studio team, it is recommended that a small number of high-quality accounts be operated in a refined manner, and increase airdrop revenue by participating in multiple ecology, improving social activity, and building a real identity chain. Only by knowing one's opponent and oneself, mastering the core screening logic, and flexibly adjusting the operation methods can one be invincible in airdrop activities!

 jinse
jinse

 panewslab
panewslab