a16z: A paper sorts out 7 token categories. How to distinguish between online tokens and company-supported tokens?

Reprinted from panewslab
03/10/2025·2MBy Miles Jennings, Scott Duke Kominers, and Eddy Lazzarin, a16z
Compiled by: Glendon, Techub News
With the increasing activity of token-based network models becoming more active and innovative, developers are thinking about how to distinguish between different types of tokens—and which tokens are best for their business. Meanwhile, consumers and policy makers are trying to better understand the role and risks of blockchain tokens in applications.
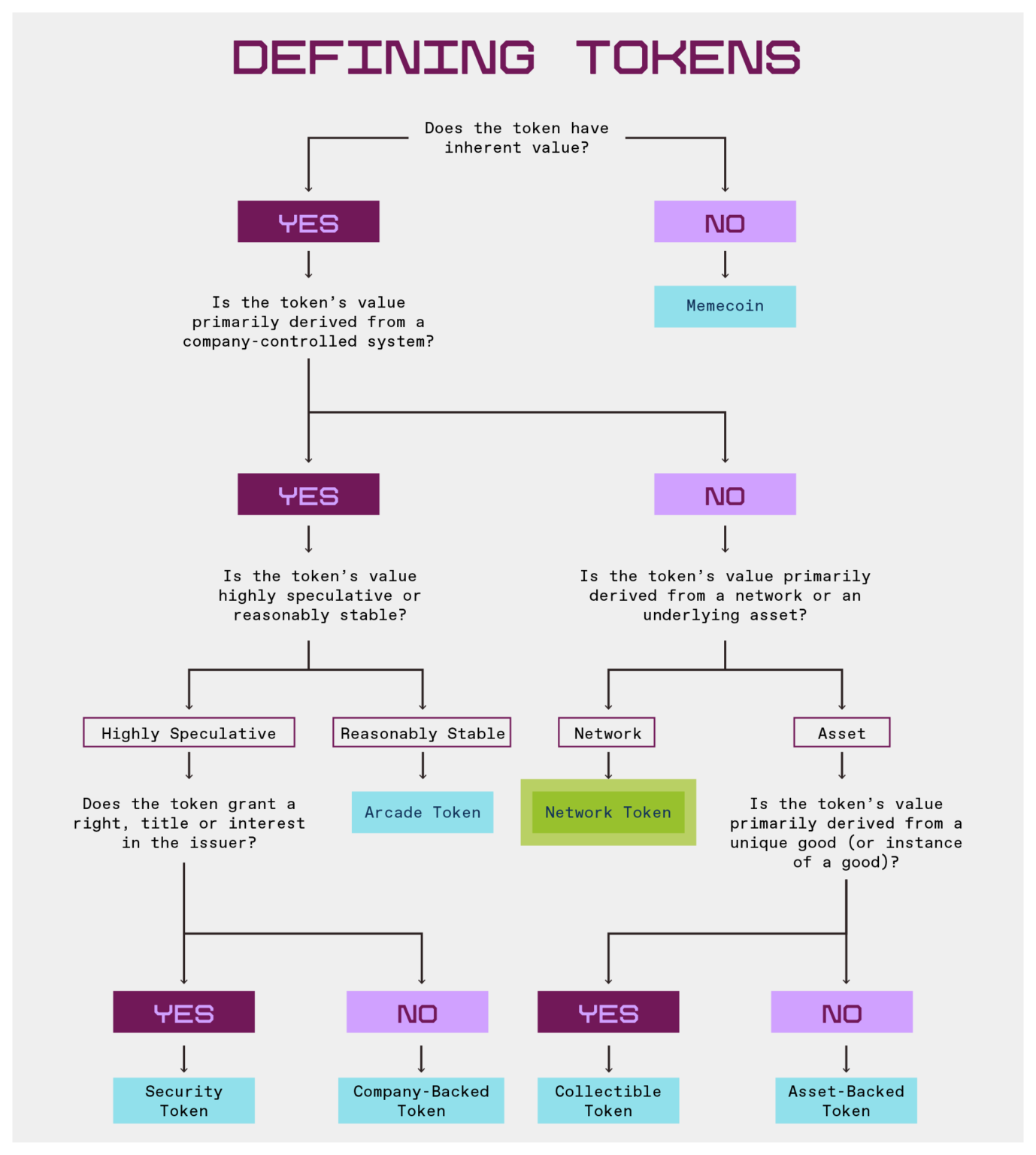
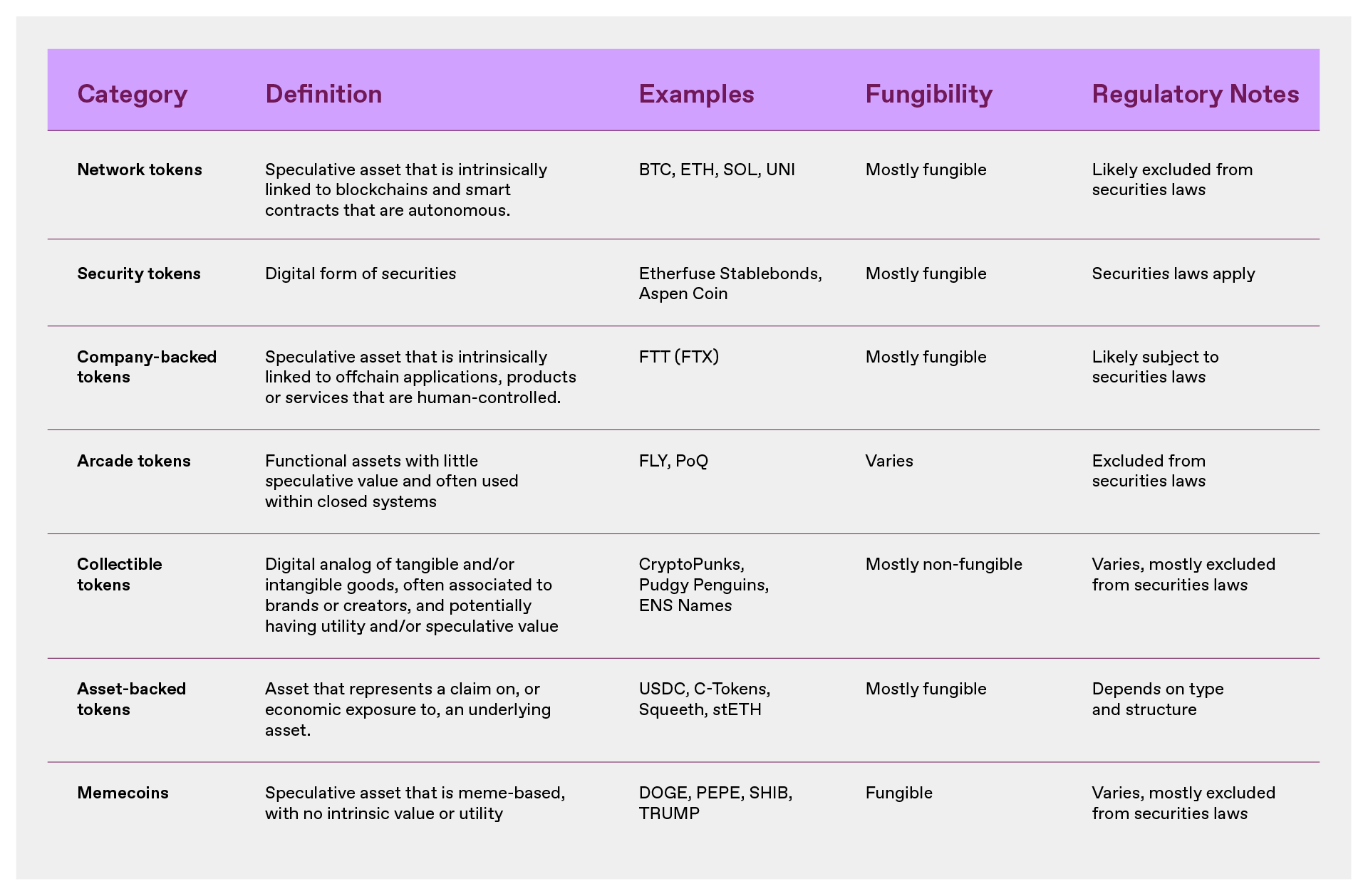
To help sort out the token categories, this article provides definitions, examples and a classification framework to understand the seven most commonly constructed categories of tokens by developers: Network Tokens, Security Tokens, Company-Backed Tokens, Arcade Tokens, Collectible Tokens, Asset-Backed Tokens and Memecoin.
Tokens and their characteristics
The essence of tokens is to achieve true digital ownership.
More precisely, blockchain is a decentralized computer composed of a network of individual computers that maintain shared ledgers—in fact, a " cloud computer ". Tokens are data records on these ledgers that track quantity, permissions, and other metadata. The key is that these data records can only be changed according to blockchain encoding rules, which can be used to grant enforceable rights.
Under this technical framework, there are many details that have an impact on design, function, value and risk:
Programmability
Since tokens are embedded in software, they can be programmed to represent almost anything – any digital form or property record. This means that tokens can be designed as digital value storage in Bitcoin, productive and consumer assets in Ethereum, collectibles such as digital transaction cards and game items, payment stablecoins such as USDC, and even digital stocks.
Rights and circulation attributes
Some tokens give various rights (such as voting rights or economic interests), while some tokens only allow the use of products or network services. Some tokens are freely transferred between users, while others are limited; some are interchangeable, i.e. all units are equivalent, while others are non-interchangeable, i.e. they represent unique personal assets (unique, such as transaction cards, or even Mona Lisa).
These design choices are important because they determine whether a token is a good store of value or medium of exchange; whether it is a productive asset with inherent functional and/or economic value; or whether it is an essentially worthless speculative tool. At the same time, the characteristics of tokens also directly affect their legal characterization.
Therefore, whether you are a blockchain project developer, investor, or an average user who uses tokens, it is crucial to understand the token type -never confuse Memecoin with online tokens. This article is also intended to help investors eliminate this confusion.
Token type
Network tokens
Internet tokens are essentially closely related to the programmatic functions of blockchain or smart contract protocols, and their value also comes from this.
Network tokens are often built-in usefulness; they can be used to operate networks, reach consensus, coordinate protocol upgrades, or incentivize network operations. The networks associated with these tokens usually (in most cases should) contain economic mechanisms that drive the value of the token. These include programmatic repurchases, dividends, and other changes to the total supply of tokens through token creation ("faucet") or destruction ("sink") to introduce inflation and deflation pressures to serve the network.
Internet tokens can have similar trust dependencies as commodities and securities. Recognizing this, both the Securities and Exchange Commission’s 2019 Framework and FIT21 stipulate that network tokens will be excluded from U.S. securities laws when these trust dependencies are mitigated through the decentralization of the underlying network. The core essence of decentralization is that systems can run without human control (individual, corporate or management team).
Network tokens are best used to guide the creation of a new network , assign ownership or control of the network to its users, and/or ensure that the network can self-fund for continuous and secure operations. Examples of network tokens include BTC, ETH, DOGE, SOL, and UNI. In the context of smart contract protocols such as Uniswap and Aave, network tokens are sometimes called "protocol tokens" or "application tokens".
Company supports tokens
The company supports tokens that have an inherent connection with off-chain applications, products or services operated by the company (or other centralized organizations). The value of such tokens comes from this, which essentially relies on the continuous operation of centralized entities.
Like online tokens, companies support tokens may use blockchains and smart contracts (for example, to facilitate payments). But because they are primarily related to off-chain operations, not network ownership, companies can unilaterally control their issuance, utility, and value. Like "casino tokens" (described below), company support tokens usually have their own embedded utility. But unlike "casino tokens", companies support tokens are speculative.
Given these characteristics—though firms support tokens do not give holders clear rights, ownership or interests like traditional securities—they have similar trust dependencies to securities: their value is essentially dependent on systems controlled by individuals, companies, or management teams. Therefore, while a company supports that tokens are not securities itself, when such tokens attract investment, their transactions may be subject to U.S. securities laws.
Companies support tokens may become legal categories. However, they have been used primarily in the U.S. history to illegally circumvent securities laws—to attract investments in applications, products or services controlled by a company, and may act as a substitute for equity or profit interests in the company. Examples of corporate support tokens include FTT, which acts as a profit interest in the FTX exchange, or assuming that a cloud service provider issues tokens that enable holders to access cloud services and obtain some on-chain revenue from such services. In addition, BNB is also a typical example of a company supporting tokens, which evolved into a network token with the launch of Binance Smart Chain. Company support tokens are sometimes called "startup tokens", or because of their links to off-chain applications, they are also called "app tokens".
In that case, what is the specific difference between online tokens and company-supported tokens?
Distinguish between network tokens and company-supported tokens
It is not easy to distinguish between online tokens and company-supported tokens, because both types of tokens may be practical and gain a certain value from the on-chain functions of the blockchain and the off-chain operations of the company. But it is necessary to distinguish them: the risks posed by online tokens and corporate support tokens pose very different to holders and should therefore be treated differently according to applicable laws. So, where is the boundary?
The only key feature that distinguishes online tokens from companies supporting tokens is that the value of online tokens mainly comes from blockchain or smart contract protocols. This feature is important because these systems can operate in an autonomous and decentralized manner, requiring manual intervention or control. Because of this, blockchain-based networks can be truly open: the system's network effects are captured on-chain and attributed to token holders, and these network effects can in principle be accessed and expanded by anyone.
On the contrary, the value of the company's support token comes mainly from off-chain systems or sources that cannot operate independently - that is, a centralized system that requires manual intervention and control. Such associations are often obvious, such as the price of tokens is pegged to the profits of off-chain applications, products or services, or the tokens are useful in these systems. But it can also be implicit—for example, a token that has no practical purpose but with the help of a company’s brand may imply that the company will give it value.
In either case, if the token is inherently associated with a system that cannot operate autonomously and its value is mainly (or expected) derived from that system, then it is a company-backed token. Due to the lack of autonomy, any relevant network (even if it seems to be public) is actually closed, just like a Web2 social network controlled by a single company, so the network effect of the token ultimately belongs to the company that controls the system, not the user.
The open differences in network design (closed vs. openness) have real economic and regulatory consequences.
-
Network tokens are associated with an open network that is uncontrolled, so it is more similar to commodities: they operate in a way that makes it impossible for either party to unilaterally influence or build risks associated with tokens. This elimination of trust dependence distinguishes network tokens from securities. If the network directs value to tokens through its functions such as programmatic repurchase and destroying tokens, the detrustworthiness feature is further strengthened.
-
If a company supports tokens, there is a security-like trust dependence: if the value of the token comes from a closed network controlled by a single entity, the entity can unilaterally change the expected value of the token. For example, the control entity can change the purpose of tokens, issue additional tokens, or even shut down the entire system at will. This shows that when people invest in companies to support tokens, securities laws should apply.
Two typical cases can further clarify this difference:
-
ETH is a typical network token. It enables holders to trade on the Ethereum network and provides holders with economic benefits to the network. The network is decentralized and autonomous (no control by human or management team). Therefore, the US SEC has clearly confirmed that the securities laws do not apply to ETH.
-
FTT is a typical company-backed token. Its value relies entirely on the ongoing operation of the FTX exchange, which itself is a centralized exchange operated and controlled by a company. FTX Company extracts a portion of the exchange's profits to repurchase FTT, thereby driving its economic value. Therefore, FTT is essentially a profit interest in FTX—its purpose and value are controlled by FTX—and therefore it should be subject to securities laws.
However, the tokens between two extreme cases can become complicated. But judging whether a token is an online token or a company supports token, you can usually draw conclusions by answering the following three questions:
1. Is the system's network design open?
2. Will the network effects of this system benefit protocol and token holders?
3. Can the system enable the protocol and token holders to obtain value independently?
If all the above answers are "yes", then theoretically the system can continue to run even if the initial development team exits (even if the functionality is limited). This is crucial because it means that the system can operate without being controlled.
Other examples also help illustrate these concepts, such as most of the tokens associated with the decentralized exchange (DEX) protocol are network tokens, although the initial development team usually operates front-end websites and off-chain routing software. The reason is:
-
The DEX protocol is usually an open network, and any developer (not only the initial team) can build a front-end website or routing tool based on the protocol.
-
Key functions such as DEX's liquidity are controlled by the protocol itself, not by the development team.
-
The economic mechanism embedded in the protocol (such as the "fee switch") allows value to flow independently to token holders, and the system is sustainable even if the initial team ceases to operate.
Take games as an example. Even if most Web3 games do not run completely on the chain (relying on off-chain services such as servers), as long as the core assets (props, characters, etc.) are issued on the chain and are not controlled by unilaterally, the system can still be regarded as an open network. If the protocol designs an economic mechanism to make value flow to the token (for example, through an on-chain transaction fee allocation), the token belongs to the network token.
In contrast, imagine what would happen if Apple launched an app store token?
Users holding tokens can enjoy discounts in the app store, or they can pay for app fees, and the app store will distribute profits to token holders through smart contracts. However, despite the use of blockchain technology, the value of its tokens still relies entirely on closed systems (app stores) controlled by Apple. The use of blockchain will not allow third parties to take advantage of Apple's network effects and build competitive app stores in their systems. In addition, the value will come from proprietary off-chain products and services controlled by Apple (app store). Even with an on-chain programmatic economic mechanism, the token value will be zeroed once Apple closes its store. Therefore, the risk profile of such tokens is closer to stocks, which is very different from online tokens and may apply to securities laws.
Securities tokens
Securities tokens represent the digital form of securities, which can be in traditional forms (such as corporate stocks or corporate bonds), or have special characteristics such as providing profit interests in a limited liability company, a share of athletes' future income, and even securitization rights to future litigation settlement payments .
Securities usually give holders certain rights, ownership or interests, and their issuers usually have unilateral powers to influence or construct asset risks. As the U.S. SEC is expected to modernize securities laws to allow on-chain trading, the number and type of securities to be tokenized may increase, which may increase the efficiency and liquidity of the securities market. But even if the categories continue to grow, digital securities will remain subject to U.S. securities laws.
Securities tokens have been used to raise funds for commercial enterprises. Examples of securities tokens include Etherfuse Stablebonds and Aspen Coin , which is partly owned by The St. Regis Aspen Resort.
Casino Tokens
"Casino Tokens" can specifically refer to "functional tokens in closed scenarios" and provide practicality within the system and are not used for investment purposes. Such tokens are often used as currencies in the digital economy, such as digital gold in games, loyalty points in membership programs, or points for redeemable digital products and services.
Importantly, casino tokens are different from securities tokens, network tokens and company-backed tokens because they are designed specifically to prevent speculation. For example, these tokens may not have a supply cap (meaning an unlimited amount can be minted) and/or have limited transferability; if not used, they may expire or depreciate, or they may have monetary value and utility only in the system in which they are issued. Especially critical is that they do not provide, promise or imply financial returns. Given that they are not suitable as investment products, casino tokens are generally not subject to U.S. securities laws.
Because of this, casino tokens are best suited to be used as currency in the digital economy, and issuers gain economic benefits by controlling the monetary policy of that digital economy (i.e. acting as a central bank) and maintaining stable token value, rather than benefiting from the appreciation of token value. For example, FLY , which is the loyalty and payment token of the Blackbird restaurant network, and another example is Pocketful of Quarters, an in-game asset. They embody the concept of casino tokens very well. Casino tokens are sometimes called "utility tokens", "loyalty tokens" or "points".
Collect tokens
The value, utility or significance of a collection token comes from records of ownership of tangible or intangible goods. For example, a collection token can be a digital simulation or representation of a work of art, musical work, or literature; a collection or commodity, such as a ticket stub for a concert; a membership of a club or community; or an asset in a game or a metaverse, such as a digital sword or a plot of land in the metaverse .
These tokens are usually irreplaceable and are often practical. For example, collectible tokens can be used as an activity license or ticket; can be used in video games (such as representing a sword); or can provide ownership in relation to intellectual property rights. Since collectible tokens are often associated with finished products or products and do not rely on the efforts of third parties, they are generally not subject to U.S. securities laws.
Collection tokens are best used to convey ownership of tangible or intangible goods. Many (though not all) "NFT" products fall into this category. Examples include NFTs that convey ownership of digital art or other media; profile pictures such as CryptoPunks and Bored Apes (“pfps”), as well as other virtual fashion and branded merchandise; game items; and account records or identifiers (such as ENS domains ).
Some collectible tokens are directly associated with physical products, either providing a digital extension of the physical product experience, such as Pudgy Penguins toys and Generative Goods collection cards, or providing a digital representation of physical goods for easy tracking and/or exchange, such as NFT event tickets and BAXUS’s alcohol NFTs.
Asset-backed tokens
The value of asset-backed tokens originates from claiming rights or economic risks to one or more underlying assets. These underlying assets may include real-world assets (such as commodities, fiat currencies, or securities) or digital assets (such as cryptocurrencies or liquidity pool equity).
Asset-backed tokens can be sanctioned in whole or in part and can be used for different purposes: acting as a store of value, a hedging tool, or an on-chain financial primitive. Unlike collectible tokens that get value from ownership of unique goods such as digital artwork, in-game items, or event tickets, asset-backed tokens function more like financial instruments, gaining value from their collateral, price-linking mechanisms, or redemption rights. However, the regulatory processing of asset-backed tokens depends on their structure and purpose. Some tokens, such as fiat-backed stablecoins, are usually not subject to U.S. securities laws. Other tokens, such as certain derivative tokens, may be subject to securities or commodities if they represent investment contracts or tools similar to futures.
There are many use cases for asset-backed tokens, including:
-
Stablecoin: pegged to currency or assets;
-
Derivative tokens: Provide synthetic exposure to underlying assets or financial positions;
-
Liquidity Provider (LP) tokens: Represents claims for collective assets in the Decentralized Finance (DeFi) protocol;
-
Deposit receipt token: A pledged or custodial asset.
The most common examples include USDC (a stablecoin backed by fiat currency), Compound’s C token (a LP token), Lido’s stETH (a liquid staked token), and OPYN’s Squeeth (a derivative token that tracks the price of ETH).
Memecoin
Memecoin is a token that has no inherent utility or value, usually associated with internet memes or community-driven movements, and has no fundamental connection to the network, company, or application.
Memecoin’s price is driven entirely by speculation and related market forces and is therefore extremely vulnerable to manipulation. Its main characteristics are the lack of intrinsic purposes (if there is a purpose, they are no longer Memecoin), the lack of practicality, and the resulting zero-sum nature and volatility. Memecoin is generally not subject to U.S. securities laws , but is still subject to anti-fraud and market manipulation laws.
The most typical examples are PEPE, SHIB, and TRUMP.
Among the 7 token types mentioned above, not all tokens are perfectly included—developers will iterate and experiment with new models regularly. For example, if social and reputation tokens are not investable, they may be more like “casino tokens” and if they are controlled by centralized issuers, they may be more like companies supporting tokens. As token features change or new features increase, tokens can also evolve from one category to another, making classification difficult.
But the decisive characteristics of dividing these categories are the expected sources of value accumulation, and the following flowchart helps illustrate this: