Zero misunderstandings on-chain interactions, please accept the Web3 security transaction guide

Reprinted from panewslab
04/10/2025·2MWith the continuous expansion of the on-chain ecosystem, on-chain transactions have gradually evolved into an indispensable daily operation for Web3 users. User assets are accelerating the migration from centralized platforms to decentralized networks, and this trend also means that the responsibility for asset security is shifting from the platform to the user themselves. In an on-chain environment, users need to be responsible for every step of interaction. Whether it is importing a wallet, accessing a DApp, or signing and authorizing and initiating transactions, any blind signing or operational error may become a security risk, causing serious consequences such as private key leakage, authorization abuse or phishing attacks.
Although the current mainstream wallet plug-ins and browsers have gradually integrated functions such as phishing recognition and risk reminder, in the face of increasingly complex attack methods, it is still difficult to completely avoid risks by relying solely on the passive defense of tools. In order to help users more clearly identify potential risk points in on-chain transactions, our security team has sorted out the high-risk scenarios throughout the process based on practical experience, and combined with protection suggestions and tool usage techniques, a systematic on-chain transaction security guide was developed to help every Web3 user build an "independent and controllable" security line.
Core guidelines for secure transactions:
- Reject blind signatures: Do not sign transactions or messages that you do not understand.
- Repeated verification: Before conducting any transaction, be sure to verify the accuracy of the relevant information multiple times.

1|Safe transaction suggestions
Secure transactions are the key to protecting digital assets. Research shows that using a secure wallet and two-step verification (2FA) can significantly reduce risks. The following are specific suggestions:
- Use a secure wallet:
Choose a reputable wallet provider, such as hardware wallets such as Ledger or Trezor, or software wallets such as Metamask. Hardware wallets provide offline storage, reducing the risk of online attacks and are suitable for storing large assets.
- Double check transaction details:
Always verify the receiving address, amount and network before confirming the transaction (for example, make sure you are using the correct chain, such as Ethereum or BNB Chain, etc.) to avoid losses caused by input errors.
- Enable two-step verification (2FA):
If the trading platform or wallet supports 2FA, be sure to enable it to increase account security, especially when using a hot wallet.
- Avoid public Wi-Fi:
Do not trade on public Wi-Fi networks to prevent phishing and man-in-the-middle attacks.
2|How to conduct safe transactions
A complete DApp transaction process includes multiple links: wallet installation, access to DApp, connecting to wallet, message signature, transaction signature, and post-transaction processing. There are certain safety risks in each link. The following will introduce the precautions in actual operations in turn.
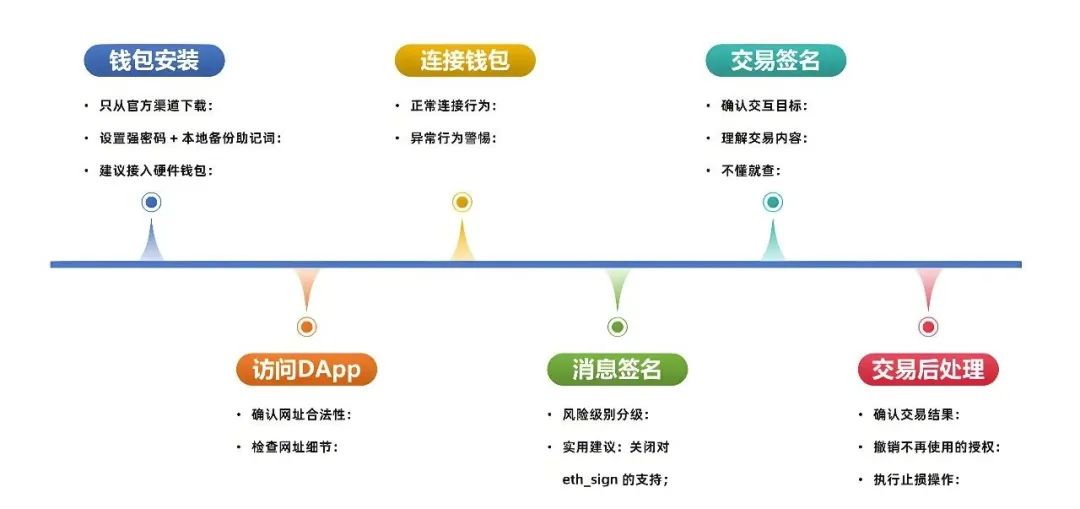
Note: This time we will mainly talk about the secure interaction process on Ethereum and various EVM compatible chains. The tools and specific technical details used by other non-EVM chains may vary.
1: Wallet installation:
At present, the mainstream way of using DApps is to interact through browser plug-in wallets. Mainstream wallets used by EVM chains include MetaMask, etc.
When installing a Chrome plug-in wallet, you need to confirm that you download and install it from the Chrome app store to avoid installing it from third-party websites in case of installing wallet software with backdoors. Users with conditions recommend using a hardware wallet in combination to further improve overall security in private key storage.
When installing wallet backup seed phrases (usually 12-24 words recovery phrases), it is recommended to store them in a safe place, away from digital devices (e.g., written on paper and saved in a safe).
2: Visit DApp
Web phishing is a common method in Web3 attacks. A typical case is to induce users to access phishing DApp applications in the name of airdrops, and after the user connects to the wallet, it induces them to sign token authorization, transfer transactions or token authorization signatures, resulting in asset losses.
Therefore, when accessing DApps, users need to be vigilant to avoid falling into the trap of web phishing.
Before accessing the DApp, you should confirm the correctness of the URL. suggestion:
- Avoid direct access through search engines: Phishing attackers may rank their phishing websites at the top by purchasing ad slots.
- Avoid clicking links in social media: URLs posted in comments or messages may be phishing links.
- Repeatedly confirm the correctness of the DApp URL: it can be proofread through DApp markets such as DefiLlama, project official social media accounts, etc.
- Add a secure website to your browser favorites: access it directly from your favorites later.
After opening the DApp web page, you also need to perform a security check on the address bar:
- Check whether the domain name and URL look fake.
- Check whether it is an HTTPS link, and the browser should display the lock 🔒 flag.
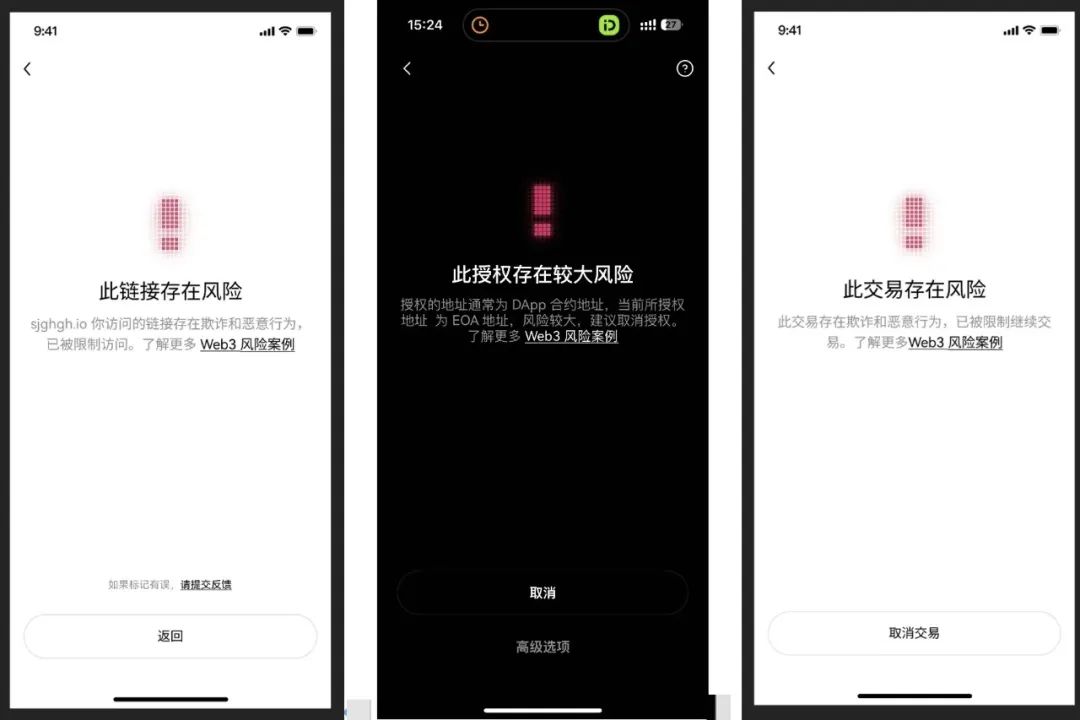
Currently, the mainstream plug-in wallets on the market also integrate certain risk warning functions, which can display strong reminders when accessing risk websites.
3: Connect to the wallet
After entering the DApp, the connection operation may be triggered automatically or after actively clicking Connect. The plug-in wallet will conduct some inspections, information displays, etc. for the current DApp.
After connecting to the wallet, usually the DApp will not proactively call the plug-in wallet when the user has no other operations. If the DApp frequently calls the wallet to sign messages after logging in, sign transactions, and even pops up signatures after refusing to sign, it is also likely that it is a situation of a phishing website and needs to be handled with caution.
4: Message Signature
In extreme cases, for example, the attacker attacked the official website of the protocol or replaced the page content through front-end hijacking. It is difficult for ordinary users to identify website security in this scenario.
At this time, the signature of the plug-in wallet is the ultimate barrier for users to save their own assets. As long as you refuse to drop a malicious signature, you can protect your own assets from loss. When signing any messages and transactions, users should carefully review the signature content and refuse blind signing to avoid asset losses.
Common signature types include:
- eth_sign: Sign the hash data.
- personal_sign: Signing plain text information is most common when user login verification or license agreement confirmation.
- eth_signTypedData (EIP-712): Signature structured data, commonly used for Permit, NFT orders, etc. of ERC20.
5: Transaction signature
Transaction signatures are used to authorize blockchain transactions, such as transferring money or calling smart contracts. Users use private keys to verify transaction validity on the Internet. At present, many plug-in wallets will decode and display relevant content for messages to be signed. You must follow the principle of not blindly signing. Safety suggestions:
- Carefully check the payee’s address, amount and network to avoid errors.
- Large-value transactions are recommended to sign offline to reduce the risk of online attacks.
- Pay attention to gas fees, ensure reasonableness, and avoid scams.
For users with certain technical reserves, some common manual inspection methods can also be used: copy the interactive target contract address to a blockchain browser such as etherscan for review. The review content mainly includes whether the contract is open source, whether there are a large number of transactions recently, and whether Etherscan has put official tags or malicious tags on the address.
6: Post-transaction processing
After avoiding phishing web pages and malicious signatures, it does not mean that everything is going well, and risk management is still needed after the transaction.
After the transaction, you should check the transaction's linkage status in time to confirm whether it is consistent with the expected status when signing. If abnormalities are found, timely stop loss operations such as asset transfer and authorization cancellation are carried out.
ERC20 Approval Authorization Management is also very important. In some cases, after the user authorized tokens to certain contracts, these contracts were attacked many years later, and the attacker used the token authorization amount of the attacked contract to steal user funds. To avoid such situations, our security team recommends that users follow the following criteria to prevent risks:
- Minimize authorization. When authorizing tokens, there should be a limited number of authorized corresponding tokens according to the transaction needs. If a transaction requires 100 USDT of authorization, the number of authorizations for this transaction is limited to 100 USDT, and do not use the default unlimited authorization.
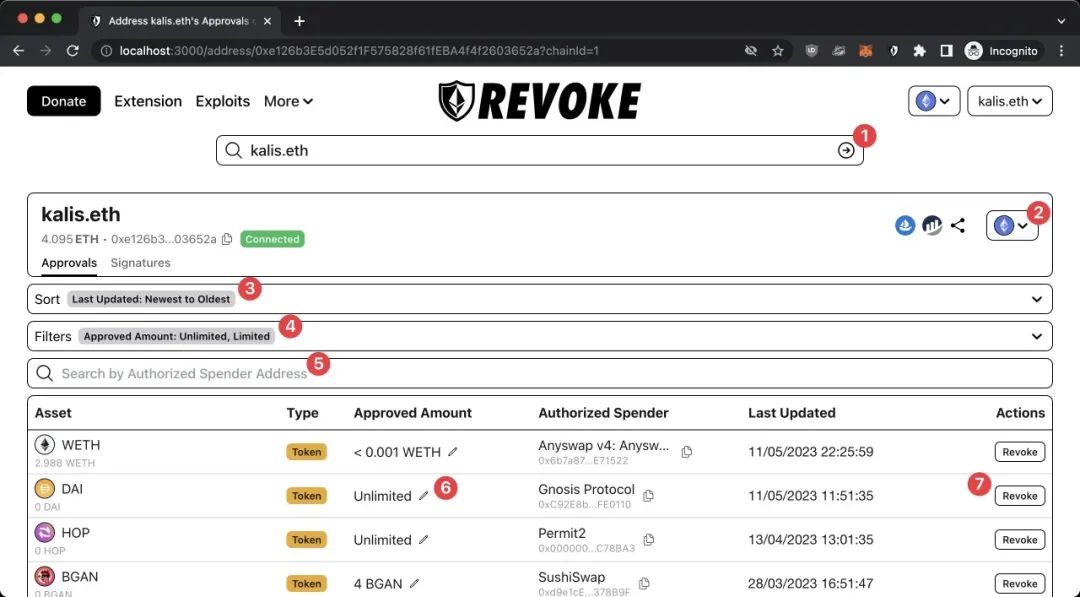
- Revoke unwanted token authorization in a timely manner. Users can log in to revoke.cash to query the authorization status of the corresponding address, revoke the authorization of the protocol that has not interacted for a long time, and prevent subsequent vulnerabilities from the agreement, which can lead to asset losses due to exploiting the user's authorization limit.
Three|Fund isolation strategy
In the case of risk awareness and sufficient risk prevention, it is also recommended to conduct effective fund isolation to reduce the degree of damage to funds in extreme cases. Recommended strategies are as follows:
- Use Gnosis Safe to store large assets by signing up or cold wallets;
- Use a plug-in wallet or EOA wallet (such as MetaMask) as a hot wallet for daily interactions;
- Change the hot wallet address regularly to prevent the address from being exposed to a risky environment.
If you accidentally get fished, we recommend that you implement the following measures immediately to reduce your losses:
- Use tools such as Revoke.cash to cancel high-risk authorization;
- If the permit signature is signed but the assets have not been transferred yet, a new signature can be initiated immediately to invalidate the old signature nonce;
- If necessary, quickly transfer remaining assets to a new address or cold wallet.
4|How to safely participate in airdrop activities
Airdrops are a common way to promote blockchain projects, but there are also hidden risks. Here are a few suggestions:
- Project background research: Ensure the project has a clear white paper, public team information and community reputation;
- Use a dedicated address: register a dedicated wallet and email address to isolate the risks of the main account;
- Click on links with caution: only obtain airdrop information through official channels to avoid clicking suspicious links in social platforms;
5|Suggestions on Selection and Use of Plug-in Tools
There are many contents of blockchain security codes, and it is possible that not every interaction can be carefully checked. Choosing a secure plug-in is crucial and can help us make risk judgments. The following are specific suggestions:
- Trusted extensions: Use browser extensions that are commonly used by people, such as Metamask (for the Ethereum ecosystem). These plugins provide wallet functionality and support DApp interaction.
- Check Rating: Check user ratings and install numbers before installing new plugins. High ratings and large amounts of installations usually indicate that plugins are more reliable and reduce the risk of malicious code.
- Stay updated: Update your plugins regularly for the latest security features and fixes. Expired plugins may contain known vulnerabilities and are easily exploited by attackers.
Six | Conclusion
By following the above security transaction guidelines, users can interact more calmly in the increasingly complex blockchain ecosystem and effectively improve asset protection capabilities. Although blockchain technology has decentralization and transparency as its core advantages, this also means that users need to independently deal with multiple risks including signature phishing, private key leakage, and malicious DApps.
To achieve true security on-chain, relying solely on tool reminders is far from enough. Establishing systematic security awareness and operating habits is the key. Only by using hardware wallets, implementing fund isolation strategies, regularly checking authorization and updating plug-ins and other protective measures, and implementing the concept of "multi-factor verification, refusal of blind signing, and fund isolation" in transaction operations, can we truly achieve "free and safe linking".

