What did North Korean hackers do with the money they stole from crypto platforms?

Reprinted from panewslab
12/22/2024·5MSource: Chainalysis
Compiled by: Tao Zhu, Golden Finance
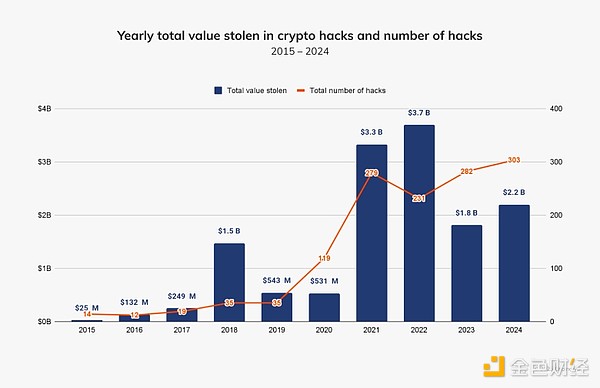
Cryptocurrency hacks remain an ongoing threat, with more than $1 billion worth of cryptocurrency stolen in four of the past ten years (2018, 2021, 2022, and 2023). 2024 marks the fifth year since reaching this troubling milestone, highlighting that as cryptocurrency adoption and prices rise, so does the amount that can be stolen.
In 2024, stolen funds increased by approximately 21.07% year-on-year to US$2.2 billion, and the number of individual hacking incidents increased from 282 in 2023 to 303 in 2024.
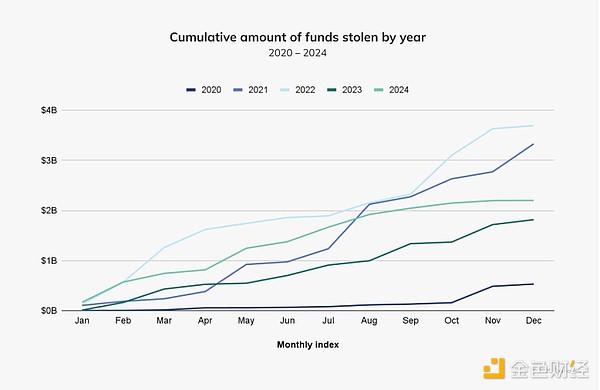
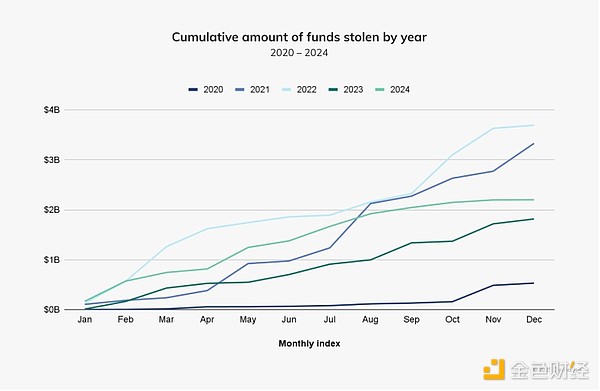
 Interestingly, the intensity of cryptocurrency hacks changed around the first
half of the year. In our mid-year crime update, we noted that the cumulative
value stolen between January and July 2024 has reached $1.58 billion,
approximately 84.4% higher than the value stolen during the same period in
2023. As we can see in the chart below, the ecosystem is easily on track by
the end of July, with the year rivaling the $3 billion-plus in 2021 and 2022.
However, the upward trend in cryptocurrency theft in 2024 slowed significantly
after July and has remained relatively stable since then. Later, we will
explore the potential geopolitical reasons for this change.
Interestingly, the intensity of cryptocurrency hacks changed around the first
half of the year. In our mid-year crime update, we noted that the cumulative
value stolen between January and July 2024 has reached $1.58 billion,
approximately 84.4% higher than the value stolen during the same period in
2023. As we can see in the chart below, the ecosystem is easily on track by
the end of July, with the year rivaling the $3 billion-plus in 2021 and 2022.
However, the upward trend in cryptocurrency theft in 2024 slowed significantly
after July and has remained relatively stable since then. Later, we will
explore the potential geopolitical reasons for this change.
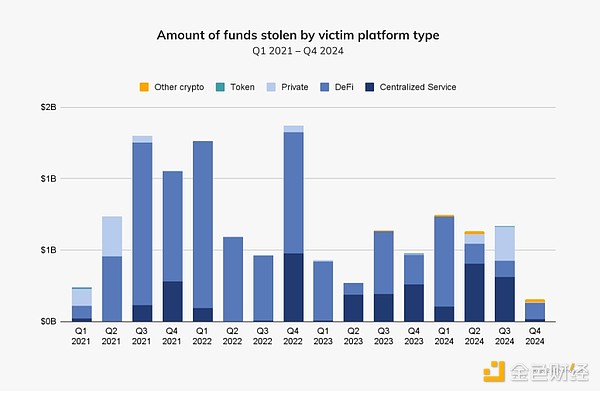
Interesting patterns also emerged in 2024 in terms of the amount stolen by victim platform type. In most quarters from 2021 to 2023, decentralized finance (DeFi) platforms were the primary target of cryptocurrency hackers. DeFi platforms may be more vulnerable to attacks because their developers tend to prioritize rapid growth and bringing products to market rather than implementing security measures, making them prime targets for hackers.
While DeFi still accounted for the largest share of stolen assets in the first quarter of 2024, centralized services were the most targeted in the second and third quarters. Some of the most notable centralized services hacks include DMM Bitcoin (May 2024; $305 million) and WazirX (July 2024; $234.9 million).
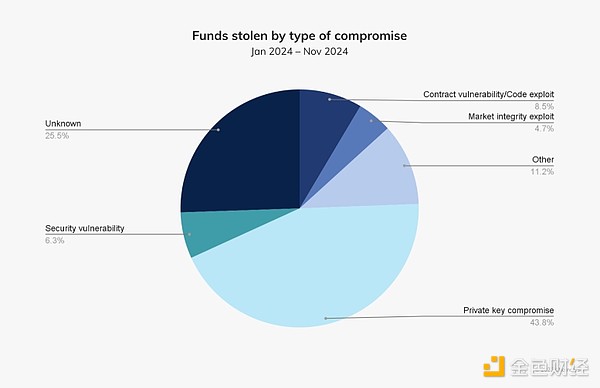
This shift in focus from DeFi to centralized services highlights the increasing importance of security mechanisms commonly used by hackers, such as private keys. In 2024, private key leaks accounted for the largest proportion of stolen cryptocurrencies, reaching 43.8%. For centralized services, keeping private keys secure is critical as they control access to user assets. Given the vast amounts of user funds managed by centralized exchanges, the impact of a private key leak could be devastating; we need only look at the $305 million DMM Bitcoin hack, one of the largest cryptocurrency breaches to date and possibly Occurs due to poor private key management or lack of adequate security.
After leaking private keys, malicious actors often launder stolen funds through decentralized exchanges (DEX), mining services, or mixing services, obfuscating transaction trails and complicating tracking. By 2024, we could see money laundering by private key hackers differ significantly from money laundering by hackers leveraging other attack vectors. For example, after stealing private keys, these hackers often turn to bridging and hybrid services. Among other attack vectors, decentralized exchanges are more commonly used for money laundering activities.
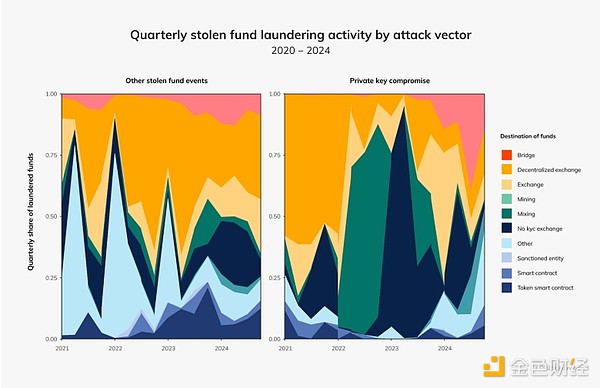
North Korean hackers will steal more from crypto platforms in 2024 than
ever before
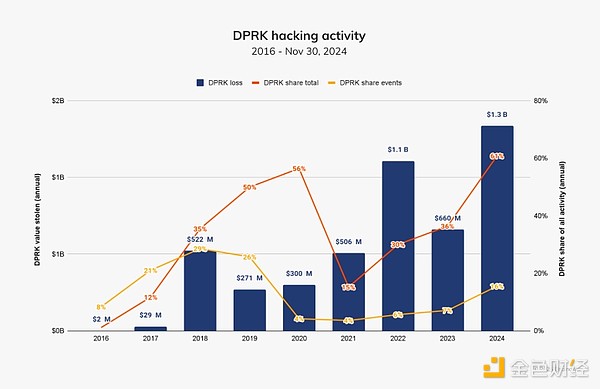
North Korea-linked hackers are notorious for their sophisticated and ruthless tactics, often using advanced malware, social engineering and cryptocurrency theft to fund state-sponsored operations and circumvent international sanctions. U.S. and international officials have assessed that Pyongyang uses stolen cryptocurrency to fund its weapons of mass destruction and ballistic missile programs, jeopardizing international security. By 2023, North Korea-related hackers will have stolen approximately $660.5 million through 20 incidents; by 2024, this number has increased to $1.34 billion across 47 incidents, an increase of 102.88% in the value stolen. These figures accounted for 61% of the total amount stolen that year and 20% of the total number of incidents.
Note that in last year's report, we published information that North Korea had stolen $1 billion through 20 hacking attacks. After further investigation, we determined that certain large hacks previously attributed to North Korea may no longer be relevant, so the amount was reduced to $660.5 million. However, the number of incidents remained the same, as we discovered other smaller hacks attributed to North Korea. Our goal is to continually re-evaluate our assessment of North Korea-related hacking incidents as we obtain new on-chain and off-chain evidence.
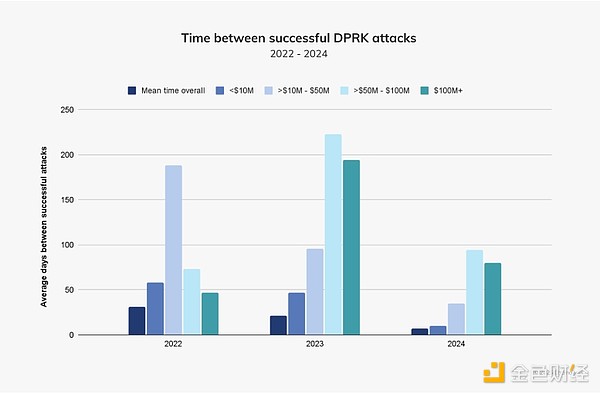
Unfortunately, North Korea’s cryptocurrency attacks appear to be becoming more frequent. In the chart below, we examined the average time between successful DPRK attacks based on exploit size and found that attacks of all sizes declined year over year. Notably, attacks worth $50 to $100 million and more than $100 million will occur much more frequently in 2024 than in 2023, indicating that North Korea is getting better and faster at large-scale attacks. This is in stark contrast to the previous two years, when profits were often less than $50 million each time.
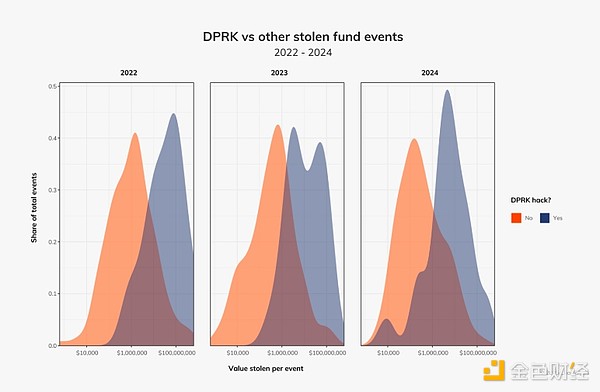
When comparing North Korea’s activities to all other hacking campaigns we monitor, it’s clear that North Korea has been responsible for the majority of large-scale attacks over the past three years. Interestingly, the amount of North Korean hacks is lower, and the density of hacks, especially around $10,000, is also increasing.
Some of these incidents appear to be linked to North Korean IT practitioners, who are increasingly infiltrating cryptocurrency and Web3 companies, compromising their networks, operations, and integrity. These employees often use sophisticated tactics, techniques, and procedures (TTPs) such as false identities, hiring third-party recruitment agencies, and manipulating remote work opportunities to gain access. In the latest case, the U.S. Department of Justice (DOJ) on Wednesday indicted 14 North Korean nationals working as remote IT practitioners in the United States. Companies have made more than $88 million by stealing proprietary information and extorting employers.
To mitigate these risks, companies should prioritize thorough employment due diligence—including background checks and identity verification—while maintaining strong private key security to protect critical assets, where applicable.
While all of these trends point to North Korea being very active this year, most of its attacks occurred early in the year, with overall hacking activity stalling in the third and fourth quarters, as shown in the earlier chart.
In late June 2024, Russian President Vladimir Putin and North Korean leader Kim Jong Un will also hold a summit in Pyongyang to sign a mutual defense agreement. So far this year, Russia has released millions of dollars in previously frozen North Korean assets under U.N. Security Council sanctions, signaling a growing alliance between the two countries. North Korea, meanwhile, has deployed troops to Ukraine, supplied ballistic missiles to Russia and reportedly sought advanced space, missile and submarine technology from Moscow.
If we compare the average daily losses from DPRK vulnerabilities before and after July 1, 2024, we can see that the amount of value stolen dropped significantly. As shown in the figure below, the amount stolen by North Korea subsequently dropped by approximately 53.73%, while the amount stolen by non-North Korea increased by approximately 5%. Therefore, in addition to shifting military resources to the conflict in Ukraine, North Korea, which has significantly increased its cooperation with Russia in recent years, may also have changed its cybercriminal activities.
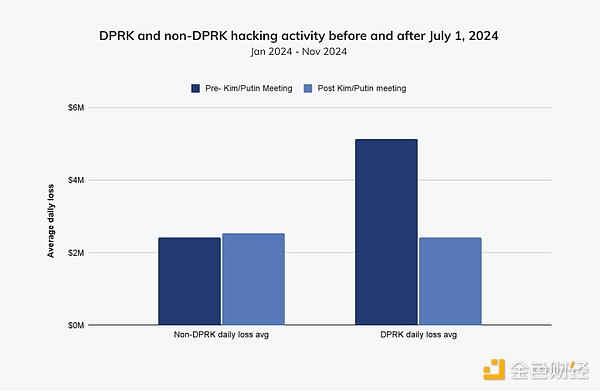
The decline in North Korean theft after July 1, 2024 is clear and the timing is clear, but it is worth noting that this decline is not necessarily related to Putin's visit to Pyongyang. Additionally, some events in December may change this pattern at the end of the year, and attackers often launch attacks during the holidays.
Case Study: North Korea Attack on DMM Bitcoin
One notable example of a North Korea-related hack in 2024 involved the Japanese cryptocurrency exchange DMM Bitcoin, which suffered a hack that resulted in the loss of approximately 4,502.9 Bitcoins, worth $305 million at the time. Attackers targeted vulnerabilities in the infrastructure used by DMM, resulting in unauthorized withdrawals. In response, DMM, with the support of the group company, fully paid customer deposits by finding equivalent funds.
We were able to analyze the on-chain flow of funds after the initial attack, and in the first phase we saw the attackers move millions of dollars worth of cryptocurrency from DMM Bitcoin to several intermediate addresses before eventually reaching the Bitcoin CoinJoin mixing server.
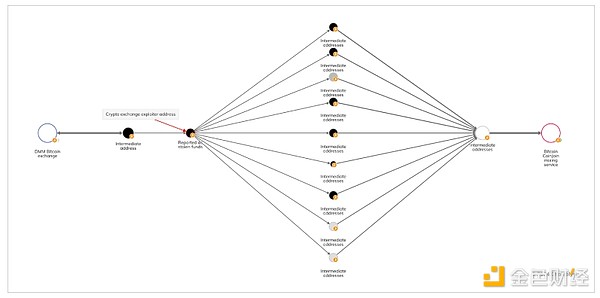
After successfully mixing the stolen funds using the Bitcoin CoinJoin mixing service, the attackers moved some of the funds through some bridging services to Huioneguarantee, an online marketplace associated with Cambodian conglomerate Huione Group, a major player in the field . Facilitate cybercrime.
DMM Bitcoin has transferred its assets and customer accounts to SBI VC Trade, a subsidiary of Japanese financial group SBI Group, with the transition scheduled to be completed in March 2025. Fortunately, emerging tools and predictive techniques are emerging, which we’ll explore in the next section, to prepare you for preventing such destructive hacks from happening.
Stop hackers with predictive models
Advanced predictive technologies are transforming cybersecurity by detecting potential risks and threats in real-time, providing a proactive approach to protecting digital ecosystems. Let’s look at the example below, involving decentralized liquidity provider UwU Lend.
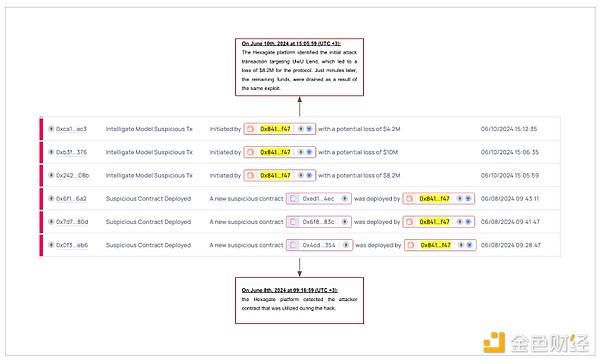
On June 10, 2024, the attacker obtained approximately US$20 million in funds by manipulating UwU Lend's price oracle system. The attacker launched a flash loan attack to change the price of Ethena Staked USDe (sUSDe) on multiple oracles, resulting in incorrect valuations. As a result, an attacker can borrow millions of dollars in just seven minutes. Hexagate detected the attack contract and its similar deployment approximately two days before the exploit.
Although the attacking contract was accurately detected in real time two days before the vulnerability was exploited, its connection to the exploited contract was not immediately apparent due to its design. This early detection can be further leveraged to mitigate threats with additional tools such as Hexagate's security oracles. Notably, the first attack, which resulted in a loss of $8.2 million, occurred minutes before subsequent attacks, providing another important signal.
Such alerts before major on-chain attacks have the potential to transform security for industry players, allowing them to completely prevent costly hacks rather than respond to them.
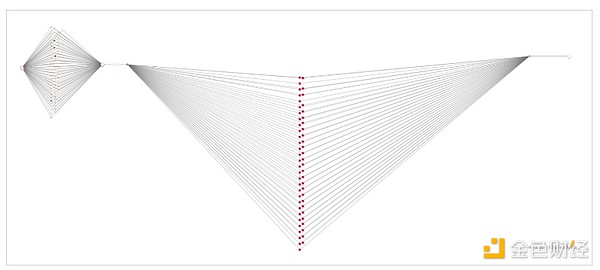
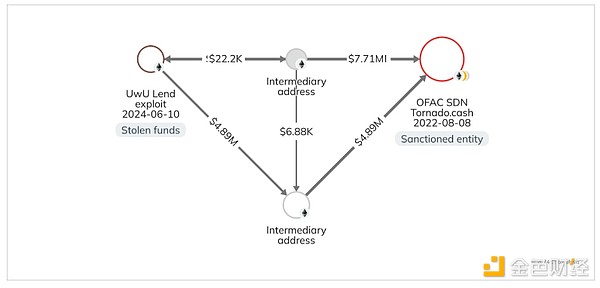
In the image below, we see the attacker moved the stolen funds through two intermediate addresses before the funds reached Tornado Cash, an OFAC-approved Ethereum smart contract mixer.
However, it is worth noting that mere access to these predictive models does not ensure protection against hackers, as protocols may not always have the appropriate tools to take action effectively.
Need for stronger cryptographic security
The rise in stolen cryptocurrencies in 2024 highlights the need for the industry to respond to an increasingly complex and evolving threat landscape. While the scale of cryptocurrency theft has not yet returned to 2021 and 2022 levels, the resurgence noted above highlights gaps in existing security measures and the importance of adapting to new exploitation methods. To effectively address these challenges, collaboration between the public and private sectors is crucial. Data sharing programs, real-time security solutions, advanced tracking tools, and targeted training can enable stakeholders to quickly identify and neutralize malicious actors while building the resiliency needed to protect crypto assets.
Additionally, as the cryptocurrency regulatory framework continues to evolve, scrutiny of platform security and customer asset protection is likely to increase. Industry best practices must keep pace with these changes to ensure prevention and accountability. By building stronger partnerships with law enforcement and providing teams with the resources and expertise to respond quickly, the cryptocurrency industry can strengthen its theft prevention capabilities. These efforts are critical not only to protecting personal assets, but also to building long-term trust and stability in the digital ecosystem.



 jinse
jinse