Tron TRON Industry Weekly: BTC consolidation may be beneficial to the counterfeit sector, ZKP integrates into AI training model

Reprinted from chaincatcher
05/26/2025·13D1. Forecast
1. Macro-level summary and future forecast
Last week, Trump posted on social media, suggesting that 50% tariffs on EU goods will be imposed on June 1, saying that the EU's trade deficit with the United States exceeded US$25 billion per year through trade barriers and other means. The move has sparked market concerns about the substantial decoupling of US-European trade. Although Trump agreed to extend the negotiation deadline to July 9 on May 25, the threat of high tariffs has impacted global supply chains and financial markets.
2. Market changes and early warnings in the crypto industry
After Bitcoin broke through $111,000 to hit a record high, the market entered a high-level volatility mode, with the total market value increasing from $3.1 trillion to $3.24 trillion, indicating that funds are gradually flowing to non-bitcoin assets, and the early signals of the "altcoin season" are beginning to appear. Meme Coin, AI, DePIN and other sectors are partially active, but the market is still dominated by institutions. Altcoins continue to maintain a volatile consolidation model. The comprehensive "altcoin season" may need to wait for Bitcoin to enter the sideways stage.
3. Industry and track hot spots
The Disney-like 3D meta-universe platform Puffverse is breaking the barriers of Web3 & Web2, allowing users to step into an extraordinary virtual world; Web3 social ecosystem UXLINK promotes users to participate in the Web3 world by integrating multiple modular Dapps.
2. Market hot tracks and weekly potential projects
1. Potential track performance
**1.1. A brief analysis of how the 3D meta-universe platform Puffverse
breaks the barriers of Web3 & Web2**
PuffWorld is a meta-universe that creates an immersive 3D experience for users, allowing users to step into an extraordinary virtual world. In PuffWorld, users can explore this infinitely wonderful universe, fully enhance the gaming experience, and establish meaningful connections with others.

Currently, PuffWorld can accommodate up to 40 adventurers per channel, providing a high-quality and convenient interactive experience. Puffverse is under continuous development and will achieve the ability of a single channel to accommodate more than 10,000 players in the future.
Brief description of the architecture
$PFVS & vePUFF
PFVS and vePUFF are two important tokens in the Puffverse ecosystem, and they are closely related.
$PFVS is a circulating token in the main paid scenarios in Puffverse. Users can use $PFVS to make various consumptions, such as purchasing a PuffGo pass to participate in the PuffGo league, purchasing game props, editing UGC content, purchasing cloud gaming computing power, etc. This token not only encourages users to actively participate in ecological construction, but also provides rewards to developers who contribute to game development.
vePUFF is a governance token in Puffverse, which is mainly obtained through staking $PFVS, and can also be rewarded by participating in specific PuffGo games. Most importantly, vePUFF holders have the power to participate in the Puffverse decentralized governance (Puff DAO) vote.
The conversion between PFVS and vePUFF can be performed in a fixed ratio, with a redemption ratio of 100:1 , that is, 100 PFVS can be locked into 1 vePUFF, so as to enjoy ecological rewards and obtain governance voting rights. At the same time, the length and amount of time held by vePUFF will affect the final reward allocation.
Puffs NFT
The core asset in Puffverse is a main NFT called Puff .
Each NFT has a unique character and its corresponding appearance combination. Users can obtain these NFTs through the secondary market or participate in upcoming Puff and promotional activities.
A rich and diverse NFT universe is built in Puffverse, each with different but practical features in the ecosystem, including but not limited to:
- Puff Genesis : has the most privileges to participate in Puff NFTs for all products in Puffverse.
- Puff Limited Edition NFT : Including Puff Football Series, New Year Series, Astronaut Series, etc.
- Puff Classic : Can be used to simulate the placement of the game PuffSim to enhance the star rating of Puff NFT.
- Puff General : Puff NFT without special costumes, obtained through PuffGo Easter Egg hatching, and can be used in PuffGo games.
- Puff Ticket : It can be used to redeem game props in the future.
These NFTs not only have collection value, but also play a key role in various Puffverse products, forming a user experience with strong interaction and in-depth participation.
Product Introduction
PuffGo - Party Battle Royale Chain Game
PuffGo is a multiplayer online party battle royale game based on blockchain. Players can also make money while enjoying the fun of the game (Play-to-Earn). The game includes multiple levels and gameplay modes, supporting different forms of battles from single player to multiplayer. Players can collect game characters with different appearances, personalities, skills and costumes, and compete in different levels and modes based on the character's advantages. Diversified skill matching and strategy selection will play a key role in competing for high rankings and generous rewards.
The game aims to allow players to experience a fun and differentiated game process by manipulating various game characters, and bring an immersive entertainment experience through diverse themes, rich levels and personalized clothing. There are several main characters in PuffGo, with distinct personalities and unique appearance, and equipped with exclusive backstory and customized skills or attributes to show their strengths in different scenarios.
The vision of the development team is to create an NFT game universe that integrates entertainment and reward mechanisms, so that players can get both happiness and rewards here.
PuffTown (Pubble Town)
PuffTown is the control panel for managing all Puff-related assets. It can display your in-game data and on-chain data, support creating or importing wallets, managing your various assets, tracking game records, improving game experience, and allowing you to play simulation games and other functions.
In short, PuffTown is a comprehensive management platform for Puffverse users, connecting the on-chain and off-chain worlds, providing players with one-stop service and a more convenient operating experience.
PuffSim (Bubbles Simulator)
PuffSim is a simulated placement game that allows players to easily obtain passive benefits. Players can upgrade their character to improve their combat effectiveness and use them to participate in adventures. When selecting a certain number of characters to join the adventure, the player does not need to operate manually, just wait for the characters to fight automatically, and the reward after the battle will be determined based on the total combat power and time.
In short, players send characters to participate in the adventure. According to the adventure results, after a period of time, they will obtain the character experience and corresponding gold coins/diamond rewards, and there is a certain probability of obtaining a treasure chest. After opening the treasure chest, you can randomly get a certain number of gold coins or diamonds, and the probability of the two rewards is different.
In PuffSim, the reward does not directly generate game tokens, but is distributed in the form of "Coins" and "Diamonds" in the game. Among them, "diamonds" are vouchers for redemption. In the future, before TGE (token generation event), the diamonds held on your address will be automatically redeemed for IGO points (Initial Game Offering Points).
PuffWorld (Bubbles World)
PuffWorld is a meta-universe designed to gather users into a thrilling 3D virtual world, allowing users to step into an extraordinary immersive space. Users can explore in this endless virtual universe, enhance the gaming experience, and establish deep connections with others.
Currently, PuffWorld's single channel can accommodate up to 40 adventurers at the same time, providing a convenient and high-quality social interaction experience. Puffverse is constantly upgrading the system, and the capacity of a single channel will be expanded to more than 10,000 players in the future. At the same time, more fascinating areas, innovative gameplay and rich interactive functions will be unlocked, and the boundaries of the metaverse will be continuously expanded.
Comments
As a Disney-like 3D meta-universe, Puffverse combines Web3 and Web2, has a rich gaming ecosystem (such as PuffGo, PuffSim, PuffWorld) and a tradable NFT system, supporting users' immersive entertainment and asset appreciation, which are its main advantages. In addition, the PFVS and vePUFF dual token mechanisms have built a relatively complete economic closed loop to encourage users and developers to participate. But the disadvantage is that the current user carrying capacity is limited (for example, PuffWorld only supports 40 people with the same screen), ecological construction has not yet been fully implemented, and subsequent functions and user growth require time to verify. The fiercely competitive GameFi market is also a major challenge.
1.2. **Interpretation of Web3 social ecosystem UXLINK promotes users
to participate in the Web3 world by integrating multiple modular Dapps**
UXLINK's Social Growth Layer is a social growth infrastructure layer that includes core components such as chain abstraction, account abstraction, general Gas mechanism, and social protocols. It provides modular services for developers and various applications, helping third-party projects quickly achieve user growth and social functions integration, and accelerating the construction and expansion of the Web3 application ecosystem.

Brief description of the architecture
- One Account (Account Abstract)
UXLINK Account is an account abstraction protocol that combines social account abstraction with on-chain account abstraction . This protocol aims to open up the identity boundaries between users' Web2 and Web3, allowing users to seamlessly access multiple applications and services through a unified account, realize the integration and management of social identities and on-chain assets, and significantly improve user experience and system compatibility.

UXLINK Auth
UXLINK Auth is a secure, fast and convenient Dapp login solution for Web2 and Web3 users. It provides users with a seamless cross-platform login experience, and users can easily and securely access various Dapps regardless of whether they come from the traditional Internet or the blockchain ecosystem. This solution effectively simplifies the login process, allowing users to access the application more quickly and enjoy a smoother interactive experience.

UXLINK Account
UXLINK Account is the basic component of the One Account abstraction protocol, combining social account abstraction with on-chain account abstraction:
Social Account Abstraction (Off-Chain Account Abstraction)
Social account abstraction refers to the ability of UXLINK accounts to integrate multiple social media accounts of users (such as Telegram, X (formerly Twitter), Line, Kakao Talk, WhatsApp, Facebook, TikTok, etc.) into a virtual account to achieve unified management and authentication. Users can log in, authenticate and interact through social accounts, easily switch identities between different platforms and enjoy a cross-platform interactive experience.
On-chain account abstraction
On-chain account abstraction refers to the unified abstraction of UXLINK accounts that supports multi-chain blockchain accounts, allowing users to manage their accounts on different blockchain networks (such as Ethereum, Arbitrum, Mantle, TON, KAIA, BTC L2, Solana, etc.) without having to deal with complex on-chain operations. Through the UXLINK account, users can complete on-chain transactions, asset management and other operations more simplified.
- One Gas (Uniform Gas: $UXLINK)
UXLINK's One Gas (Unified Gas) mechanism aims to solve the problems of fragmentation of Gas tokens, inability to use tokens across chains, and high cross-chain transaction costs in the multi-chain ecosystem. With the One Gas feature, users can pay various transaction fees by simply holding $UXLINK in their account.
In the traditional way, users need to hold native tokens (such as ETH, BNB, MATIC, etc.) on each blockchain to pay for Gas, which not only increases the complexity of fund management, but also causes asset fragmentation. The One Gas mechanism realizes the experience of "one currency to multiple chains": users only need to hold $UXLINK to complete operations on multiple blockchains.
In addition, One Gas supports real-time dynamic calculation of cross-chain transaction fees, making multi-chain interaction more convenient and efficient, greatly reducing the threshold for users to use Web3 applications.

Using One Gas **
** When executing transactions through One Gas, UXLINK's Payment Hub adopts an
embedded Dapp model (implemented through UXLINK's transaction SDK and API),
allowing users to pay Gas fees directly using $UXLINK tokens. Users do not
need to switch between multiple tokens, and Gas fees will be automatically
processed through UXLINK native Paymaster.
All Gas fees will be settled seamlessly between the source and target chains at no additional cost. Therefore, when users conduct cross-chain transactions, they do not need to cross-chain bridge, manage cross-chain balances, or maintain native token pools of each chain, thus bringing a simplified and smooth one-stop cross-chain payment experience.
- Social Growth Protocols

UXLINK has launched a social growth protocol system, including the following three major protocols:
-
X2EARN protocol **
** Based on the "behavior is profit" mechanism, users can receive rewards for various interactive behaviors on the platform (such as invitation, sharing, participating in tasks, etc.), which encourages users to continue to participate. -
Social Group Protocol **
** Support the construction and management of on-chain social groups, record group activities, membership relationships and interactive behaviors, and provide on-chain credible evidence for social data. -
Social Graph Protocol **
** With user relationships as the core, a portable and composable on-chain social relationship map is established to support various application scenarios such as recommendation systems, identity authentication, and user portraits.
X2EARN protocol
When users complete interactions with various Dapps in the UXLINK ecosystem, these behaviors will be safely and effectively verified and recorded in the UXLINK account system, and users will receive Universal Points (UXUY) provided by UXLINK as a reward.
What is Universal Points (UXUY)?
UXLINK has launched a unique incentive mechanism - Universal Points (UXUY). UXUY is a points system designed to encourage users to complete interactive tasks in Dapps connected to the One Account protocol. Through UXUY points, the project party can improve user activity, thus forming an efficient closed loop of user incentives.
Combining the universal points incentive mechanism and the X2Earn protocol, UXLINK can provide Dapp project parties with real and effective social data and on-chain behavior data. The X2Earn protocol records every interaction a user has in the Dapp and converts it into verifiable social data with on-chain interaction data.
Summarize
The advantage of UXLINK is that it builds a Web3 social infrastructure for the masses, combining modular capabilities such as account abstraction, unified Gas payment, and social growth protocols to open up the login, interaction, transaction and growth paths between Web2 and Web3 users, greatly reducing the threshold for using Web3; at the same time, the UXUY points mechanism is used to incentivize real user behavior, providing verifiable social and on-chain data for Dapp projects, which is conducive to rapid ecological growth.
The disadvantage is that its ecosystem is still in its early stages, and its attractiveness to external Dapps, the privacy protection mechanism of user data, and the security of the unified account system still need to be verified by the market and time. In addition, unified payment and cross-chain operations are highly dependent on the stability and execution efficiency of the underlying architecture, and pose certain technical challenges and scalability risks.
2. Detailed explanation of the project that week
**2.1. Detailed explanation of Base participation, enabling AI developers
to generate trustless protocols with zero-knowledge proof Giza**
Introduction
Giza is developing a detrustworthy protocol for decentralized machine learning inference computing to provide security for the open economy of open source AI. This protocol enables AI developers to generate Zero-Knowledge Proofs (ZKPs) to achieve transparency and trustworthiness when deploying verifiable machine learning models.
Giza builds the infrastructure that supports truly autonomous DeFi agents. It provides the agent with key components that enable it to perform tasks in a decentralized manner, respond to user intent in an unmanaged manner, and operate freely between multiple protocols while maintaining strong trust guarantees.
Through the popularization of advanced market intelligence acquisition, Giza broke down barriers, allowing all participants to enjoy algorithmic precision capabilities that were previously only available to top players, thus achieving fair competition.
Technical architecture analysis
There is an infrastructure gap between the potential of agents and actual deployment, which requires a specially built solution to address unique challenges in automated financial operations. Although existing blockchain infrastructures perform strongly in transaction execution, they lack the professional capabilities needed to support secure, non-custodial agent operations, and face inherent scalability limitations. Meanwhile, centralized automation solutions, while trying to solve performance bottlenecks, have compromised on security and user sovereignty, introducing unacceptable assumptions of trust.
The Giza protocol bridges this gap with a comprehensive architecture designed specifically for autonomous DeFi agents. The protocol establishes a secure operational boundary for the agent while supporting its seamless interaction with multiple financial protocols. By combining smart account infrastructure, crypto-economic security execution mechanisms implemented by EigenLayer-based AVS framework, and standardized and semantically rich protocol interfaces, Giza has built a safe and flexible operating environment. This scalable execution model supports millions of proxy operations without sacrificing the security required for decentralized finance.
The underlying layer of the Giza protocol is operated by three key architectural components to ensure that the agent can run safely and autonomously:
- Semantic Abstraction Layer : Transform complex protocol interactions into standardized operations, enabling agents to understand and execute financial policies between multiple protocols.
- Decentralized Execution Layer : Provides distributed computing with crypto-economic security through EigenLayer 's AVS framework . Operators need to pledge GIZA tokens to participate in the protocol operation.
- Agent Authorization Layer : Provides an unmanaged security mechanism through smart accounts and session keys , where users can grant agent specific permissions without giving up control of assets.
This system provides DeFi proxy with infrastructure that combines security, flexibility and scalability , making decentralized automated financial systems truly possible.

- Semantic abstraction layer: a bridge connecting artificial intelligence and blockchain
The semantic abstraction layer of Giza protocol provides a two-way communication framework between AI systems and blockchain protocols. This layer implements the "Model Context Protocol (MCP)" specification. By building standardized and semantic-rich interfaces, AI agents can interact with decentralized financial protocols with natural financial concepts, while retaining the security of the underlying blockchain infrastructure.
The semantic abstraction layer is composed of three interrelated technical components, jointly creating a comprehensive AI and blockchain interaction framework:
- MCP server implementation
The basis of the semantic abstraction layer is a dedicated implementation of the Model Context Protocol (MCP), which presents protocol services in the form of AI native construction:
- Resources : Expose protocol status, market conditions and historical data in the form of MCP-compliant resources, with rich semantic context;
- Tools : Denote protocol operations as tools with well-defined input/output interfaces and semantic descriptions;
- Execution Flow : The request processing process is verified based on the service definition and converted to a protocol-compatible format.
The MCP server runs as a client component through STDIO transport and is integrated into the MCP host to ensure separation between the core functionality of the protocol and the client-oriented interface. This technical design allows for the development of more adapters without changing the protocol itself.
- Protocol abstract framework
The intermediate layer implements adapters for specific protocols, unifying the interaction modes between different DeFi protocols:
- Operation Mapping : Convert the interface of a specific protocol into standardized operations with unified structure;
- State Transformation : converts the original protocol state into a context-rich data format with semantic significance;
- Safety Constraints : Set protocol-aware boundary conditions based on protocol usage, liquidity depth and volatility indicators;
- Execution Planning : Develop the best execution path based on Gas cost, slippage forecasts and protocol-specific factors.
- Agreement Service Registration Center
The Agreement Service Registration Center is responsible for maintaining the authoritative source of the agreement service definition and supporting secure service discovery and execution:
- Service Definition Storage : Implement version storage of service descriptions that comply with MCP standards, and attach a semantic context for AI interpretation;
- Version Management : Track multiple versions of each service and maintain a clear dependency map and compatibility matrix.
The semantic abstraction layer implements a two-way data processing pipeline that converts data and operations between the proxy system and the blockchain protocol:
Operation execution process
- Request Processing : The AI system submits a request through the MCP server, the server verifies it according to the service definition, and converts the request into a protocol-compatible format.
- Protocol Interaction : The operations passed by verification interact with the corresponding protocol adapter through the Decentralized Execution Layer, including service calls, transaction execution, task execution verification and session key permission verification.
- Result Transformation : The execution results are converted back to a semantically rich format for AI systems to understand and reason.
This bidirectional processing pipeline creates a secure feedback loop that enables AI systems to understand protocol states with natural financial concepts and perform precise operations within strict security boundaries.
- Decentralized execution layer
While proxy authorization provides a security boundary for autonomous operations, proxy policies need strong infrastructure support for a large-scale and stable implementation of their policies. The decentralized execution layer is designed to solve this core challenge, meeting the following three key design requirements:
- Decentralized computing : eliminate single point of failure through distributed node architecture;
- Crypto-economic security : Set quantifiable costs for malicious behavior through token staking mechanisms;
- Large-scale performance assurance : Maintain efficient execution performance while the number of protocols and on-chain applications continues to increase.
If these requirements are not met, the agent faces an irreconcilable trade-off between security, performance and censorship resistance. And this execution layer successfully breaks through these limitations through a network architecture built specifically for this purpose.
Core architecture
The execution layer forms the operation core of the Giza protocol and creates a decentralized node network to coordinate the execution of protocol services. The architecture utilizes the Othertic technology stack to implement EigenLayer’s Active Verification Service (AVS) framework to enable secure and minimal trusted computing off-chain and maintain credibility through strict security boundaries and crypto-economic assurances.
Through this design, Giza overcomes the scalability limitations inherent in on-chain execution while retaining the security attributes required for financial operations.
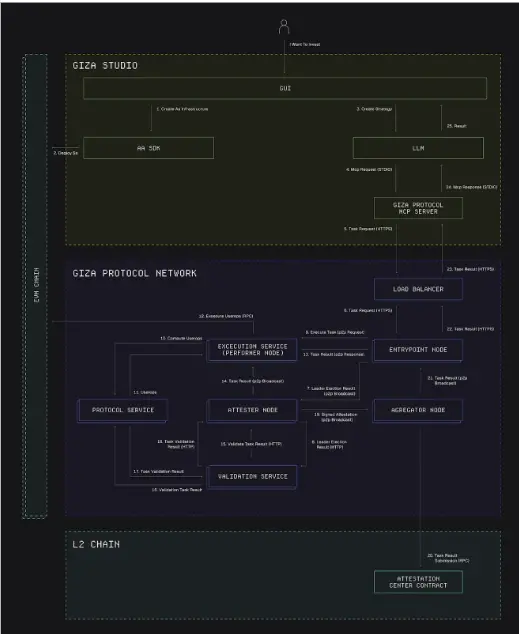
The network consists of four main node types and works in a coordinated manner:
- Entrypoint Nodes are responsible for coordinating task allocation, performing leader elections for incoming operations, and managing network communications through a secure point-to-point protocol layer to ensure that message propagation is tamper-proof.
- Performer Nodes calls the corresponding registered services under the direct instructions of the ingress node, i.e. perform operations when they are selected as leaders of the task. After executing the service call, the generated user operations will be submitted to the chain. Subsequently, the task proof is generated and broadcast to the verification node for verification.
- The Attester Nodes are responsible for verifying the execution results, ensuring that the tasks comply with the protocol requirements, and strictly verifying them through a predefined verification algorithm for each service type.
Aggregator Nodes are responsible for establishing consensus, processing verification results from multiple verification nodes, and using BLS signature aggregation to achieve efficient final result verification.
This separation of responsibilities forms a natural security boundary, combined with session key policies, which makes the operator's malicious behavior unprofitable and punishable. The architecture adopts task routing and verification mechanisms, where each node maintains a partial view of the current state while participating in the global consensus mechanism.
The entire system is based on EigenLayer's Active Verification Service (AVS) framework, integrating an Authentic technology stack that provides production-level customizable AVS contracts and aggregate nodes implementations for network booting. This integration bridges off-chain execution efficiency and on-chain security, eliminating single points of failure while maintaining the performance required for complex financial operations.
Security and economic mechanisms **
** The security of the Giza execution layer relies on a crypto-economic model
that creates direct economic incentives for correct operation while imposing
substantial penalties for malicious behavior. Through EigenLayer's re-staking
mechanism and native pledge, the protocol achieves quantifiable security
guarantees and expands with the increase in network adoption.
Network operators must pledge GIZA tokens as collateral to participate in verification, which not only establishes the basic purpose of the token, but also sets the actual cost for the attack. The system imposes slashing penalties for misconduct while allocating protocol fees to reliable operators, creating an economic cycle: the more use, the more rewards the participants who maintain the infrastructure receive. This method utilizes EigenLayer's Unique Stake model to provide isolation protection and protect the execution layer from external risks.
This economic framework combines protections defined in session keys to ensure that rational operators always act in the best interests of the network, as the rewards of correct operations far outweigh the benefits of malicious behavior. The result is a self-reinforced security model that becomes increasingly tough as protocol adoption increases.
Execution process

Agent operations flow in a simple, efficient and secure process in the network:
-
Tasks are first entered through a protected load balancer to prevent potential attack vectors
-
Identify the nodes responsible for performing tasks through the leader election mechanism
-
Execute the service to call the corresponding protocol service
-
Attesters verify the results according to the protocol requirements
-
Aggregators establish consensus from multiple verification results
-
The final result is confirmed on-chain through the Attestation Center
For operations across multiple chains, dedicated message processors maintain state consistency between execution environments, thereby achieving a seamless cross-chain strategy without sacrificing security assurance.
Therefore, the decentralized execution layer forms the core infrastructure supporting Giza's permissionless agent ecosystem, creating a safe and efficient environment that allows autonomous strategies to operate freely.
- Agent authorization layer
The Giza architecture is based on its proxy authorization system built on a smart account infrastructure, allowing the proxy to perform operations through granular permission management without hosting:
- Users can grant specific operation permissions to the agent through the Session Keys, provided that the user always maintains full control of the assets.
- Programmable authorization policies create verifiable security boundaries for automated operations
- Modular smart accounts form the basis of this system, realizing the separation of asset custody and transaction authorization
This implementation uses a smart contract wallet compatible with ERC-7579 and supports modular expansion. This standard extends the functionality of smart accounts by allowing the deployment of specialized modules to define programmable operational boundaries and verification mechanisms.
This approach creates a verifiable security boundary for automated operations without sacrificing user sovereignty. Users always retain control over their assets, but can delegate specific execution permissions to the agent through a carefully designed authorization framework.
Summarize
Giza's advantage lies in the successful opening of the semantic gap between AI and blockchain through the semantic abstraction layer and decentralized execution architecture, allowing AI to safely operate DeFi protocols in a way that "understands financial concepts". Its modular design (such as ERC-7579-based smart accounts), EigenLayer-based execution network, and fine-grained authorization mechanisms jointly build a high-security, high-scalability and high-performance proxy operation infrastructure. But at the same time, Giza's disadvantage is its high system complexity and relies on multiple technology stacks (such as AVS, Othertic, MCP, etc.), which may increase the deployment and maintenance threshold, and also have a high learning cost for developers and users.
3. Industry data analysis
1. Overall market performance
1.1 Spot BTCÐ ETF

ETF market trends:
- Bitcoin ETFs Continue to Gain Money : BlackRock's iShares Bitcoin Trust has attracted $6.5 billion inflows in the past month, becoming the fifth largest ETF of the year.
- VanEck launches Onchain Economy ETF : VanEck launched the Onchain Economy ETF (code: $NODE) on May 14, a fund investing in 30 to 60 companies related to the blockchain economy, including exchanges, miners and businesses holding crypto assets.
- Asia 's first Ethereum-staking ETF is about to be listed : Huaxia Fund plans to launch Asia's first Ethereum-staking ETF in Hong Kong on May 15, allowing investors to receive rewards without directly participating in the pledge.
ETF application progress:
- XRP spot ETF applications have entered the review stage : XRP spot ETF applications submitted by Bitwise, Grayscale, 21Shares, WisdomTree and Canary Capital have entered the review stage of the SEC, and the preliminary reply is expected to be around May 19.
- The Solana spot ETF application is progressing smoothly : The Solana spot ETF application submitted by VanEck, Grayscale, Bitwise and other institutions has entered the public comment period, and the SEC is expected to provide a preliminary reply in mid-May.
- The prospect of Litecoin ETF approval : Canary Funds' Litecoin ETF application is expected to be ruled by the SEC on May 5, and analysts believe that the probability of it being approved is as high as 90%.
ETF, November 1, ET) Ethereum spot ETF total net outflow of 10.925,600 US dollars
1.2. Spot BTC vs ETH Price Trend

Analysis
BTC continues to maintain a 4H level upward trend at this stage. In other words, the upward pattern has not been destroyed. As shown in the figure, the adjustments in the three stages are very regular and healthy (after breaking through the upper track of the consolidation zone, the new high will stabilize above the previous high after breaking through the upper track of the consolidation zone). Therefore, it will continue to be bullish before falling below $106,800, but the current market should be in the three stages of consolidation after breaking through $111,900.
For users, they can only temporarily bearish after effectively falling below $106,800, and the first point that bears the price can be directly focused on the support of $100,600.

Analysis
Strictly speaking, ETH has just entered the 2nd stage of wide consolidation market, focusing on the range of US$2320 to US$2730. Therefore, the current trend can be regarded as a rise relay in the medium term, and it is still bullish before falling below US$2320. The upper resistance can be directly focused on the resistance of US$2730, as well as the second and third-tier resistance of US$2850 or even US$3040. These two points are the upper and lower tracks of the consolidation zone when it fell at the beginning of the year, and have effective resistance.
2. Public chain data
2.1. BTC Layer 2 Summary

Analysis
Main technological progress
- Stacks (STX)
- sBTC deposit cap increase : Stacks announced the completion of Cap-2 expansion of sBTC, raising the deposit cap by 2,000 BTC, bringing the total capacity to 3,000 BTC (approximately US$250 million) to enhance liquidity and support the growing demand for Bitcoin-backed DeFi applications.
- Nakamoto upgrade : Introduced sBTC, a decentralized Bitcoin anchor asset that allows users to seamlessly transfer BTC to the Stacks network for DeFi interaction.
- Bitlayer
- BitVM Integration : Bitlayer introduces BitVM-based bridging capabilities that allow users to transfer trustless assets between multiple networks, enhancing Bitcoin’s flexibility in DeFi applications.
- Mezo
- HODL consensus mechanism : Mezo introduced the Proof of HODL consensus mechanism, rewarding users with BTC locks to ensure network security and gain benefits. Its TVL reached $230 million in early 2025.
- Merlin Chain
- ZK-Rollup Technology : Merlin Chain uses ZK-Rollup technology to improve the scalability and efficiency of Bitcoin, and the main network is expected to be launched in the near future.
2.2. EVM &non-EVM Layer 1 Summary

Analysis
EVM Compatible with Layer 1 Important
- Ethereum expansion plan
- RISC-V architecture proposal : Vitalik Buterin proposes to replace Ethereum virtual machine (EVM) with RISC-V architecture to improve scalability and operational efficiency. This move is designed to simplify the execution layer while enhancing the performance of zero-knowledge proofs.
- EIP-9698 Proposal : It is planned to increase the gas limit of Ethereum by 100 times in the next four years, and can achieve processing power of about 2,000 transactions per second by 2029.
- Injective native EVM integration
- Injective announced that it will integrate native EVM support in its Layer 1 blockchain, allowing the Ethereum ecosystem's DApps to run seamlessly on the Injective network.
- Kadena launches Chainweb EVM
- Kadena launches "Chainweb EVM" to add 20 EVM-compatible chains to its multi-chain architecture, providing low-cost and high-scaling alternatives to meet the scaling challenges of Ethereum.
Non-EVM Layer 1 Dynamic
- Sui emphasizes the growth of user experience
- Sui is a user-centric Layer 1 public chain that continues to expand in low latency, stable fees and "object-centric" data models. Its parallel execution architecture supports high throughput and is a representative of rapid technological growth.
- TON Ecosystem Expansion
- The Open Network (TON) continues to expand its ecosystem, with the number of daily transactions on-chain reaching 1.2 million, and the total locked position exceeding US$350 million. Toncoin has also been integrated into Telegram's peer-to-peer transfer system, seamlessly introducing blockchain functions into social platforms.
2.3. EVM Layer 2 Summary

Analysis
Technology progress and network upgrade
- Pectra upgrade drives Ethereum expansion
On May 7, 2025, Ethereum successfully implemented the Pectra hard fork, one of the most important upgrades since the merger in 2022. Pectra introduces higher gas restrictions and more flexible staking mechanisms, which significantly improves the scalability of the network and interoperability with the L2 chain. After the upgrade, ETH price rose 25% in 24 hours to $2,400, the largest single-day gain in four years.
- Superchain expands its market share
The Superchain alliance led by Optimism currently accounts for 60% of Ethereum L2 transaction volume and is expected to reach 80% by the end of the year. The alliance includes key players such as Coinbase, Kraken, Sony, Uniswap and Sam Altman's World. Superchain's daily trading volume reached 11.5 million, with a total locked position value of more than US$4 billion.
4. Macro data review and key data release nodes next week
As the US Treasury Department's 20-year Treasury auction subscription multiple hit a new low this year, the secondary market quickly set a wave of selling US dollar assets.这一现象背后折射出市场对美国财政健康状况的深度担忧。据高盛最新报告,在财政支出刚性增长与税收收入预期下滑的双重挤压下,美国债务可持续性正面临严峻考验。与此同时,关税政策的频繁调整以及全球机构投资者资产配置结构的战略性调整,都将持续削弱美元资产的吸引力。
本周(5月26日-5月30日)重要宏观数据节点包括:
5月29日:美国至5月24日当周初请失业金人数
5月30日:美国4月核心PCE物价指数年率;美国5月密歇根大学消费者信心指数终值
五. 监管政策
美国:推动稳定币立法与加密货币储备
-
《GENIUS法案》进展 :美国参议院通过了旨在监管稳定币的《GENIUS法案》,标志着美国在加密货币立法方面迈出重要一步。该法案旨在为稳定币市场提供明确的监管框架,增强金融稳定性和消费者保护。
-
比特币价格波动 :受总统特朗普提出的新关税政策影响,比特币价格在经历短暂上涨后回落。此前,市场对加密货币监管改善持乐观态度,推动比特币价格上涨。
巴西:稳定币引发资本流动波动担忧
- 央行警告 :巴西中央银行副行长雷纳托·戈麦斯指出,美元支持的稳定币在国际汇款中的广泛使用导致资本流动波动性增加。约90%的加密资产流动与稳定币相关,绕过传统监管渠道,给金融监管带来挑战。
欧盟:计划禁止匿名加密货币和账户
- 反洗钱新规 :欧盟批准了一项新的反洗钱法规,计划自2027年起禁止使用匿名加密货币(如Monero和Zcash)和未进行身份验证的加密账户。该措施旨在提高金融交易的透明度,打击非法活动。
印度:呼吁在全球加密监管中发挥领导作用
- 政策倡议 :随着美国、欧盟、新加坡和迪拜等主要司法管辖区推进加密资产的整合,印度被呼吁采取积极措施,在全球加密监管中发挥领导作用,以确保在数字经济中占据重要地位。
尼日利亚:将比特币归类为证券
- 新投资法案 :尼日利亚总统博拉·艾哈迈德·蒂努布签署了《2025年投资和证券法案》,正式将比特币和其他数字资产归类为证券。该法案为尼日利亚提供了正式的加密货币监管框架,旨在增强投资者保护,促进透明度,并与国际标准接轨。

 jinse
jinse

