First aid guide: Don’t be anxious when BTC is stolen, leave a message on the chain first

Reprinted from panewslab
04/24/2025·22DAuthor: Lisa
Editor: Sherry
background
On-chain message, as a special communication method in the blockchain world, has been frequently used in various security incidents in recent years. For example, SlowMist recently assisted KiloEx in conducting multiple rounds of communication with attackers through on-chain message, and ultimately successfully promoted the return of all stolen funds of US$8.44 million. In an anonymous environment, on-chain messages can be used as an effective tool to establish preliminary dialogue and lay the foundation for subsequent fund recovery.
In our previously published article "Message on the Chain of the Stolen First Aid Guide", we introduced in detail the way to leave messages on Ethereum. The Bitcoin network also supports on-chain messages, but the implementation methods of the two are slightly different. The core tool for leaving messages on the Bitcoin chain is the OP_RETURN instruction. It allows users to embed 80 bytes of custom data in transactions. This part of the data will not be used by nodes for transaction verification, nor will it affect the status of UTXO. It is purely used to record information and will be fully recorded in the blockchain.
How to use OP_RETURN to leave a message on the chain
Step 1: Encoding the content of the message
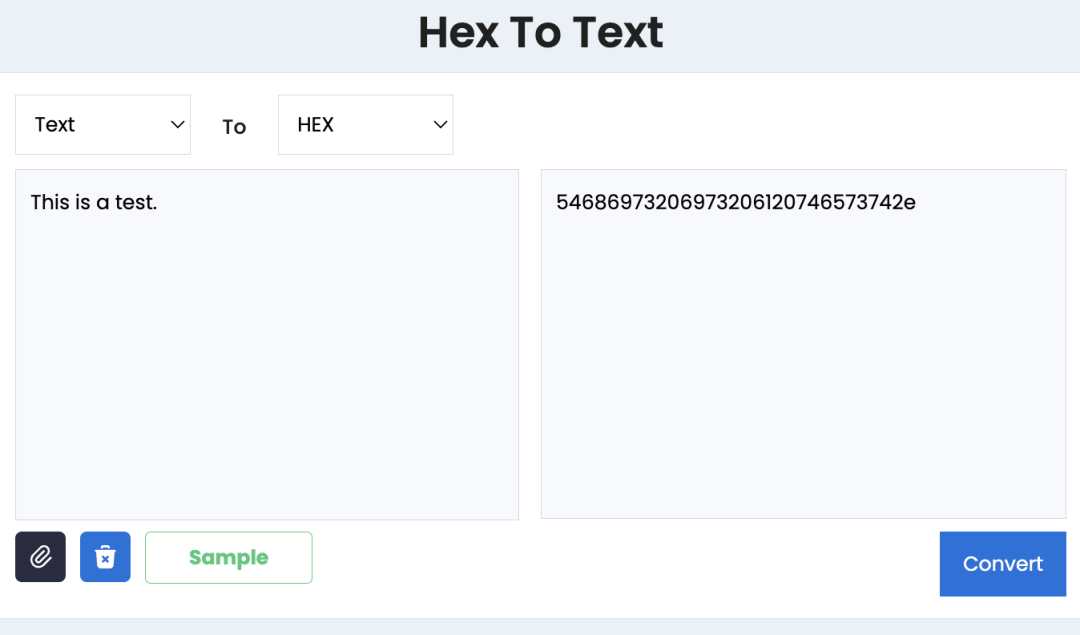
First, convert the text information to be sent to hexadecimal (HEX) format. The OP_RETURN instruction on the Bitcoin chain only accepts HEX format data.
For example, if you want to leave a message:
This is a test.
The converted HEX is:
54686973206973206120746573742e
It can be done using the online format conversion tool or through Python scripts:
text = "Hello, this is a test."hex_text = text.encode("utf-8").hex()print(hex_text)
The content of the message must be less than 160 hexadecimal characters, that is, 80 bytes. It is recommended to simplify the information or send multiple messages if it exceeds the length.
Step 2: Build a transaction with OP_RETURN
Next, you need to create a transaction with OP_RETURN output using a Bitcoin wallet or tool that supports custom transactions.
Taking Bitcoin Core as an example, use createrawtransaction to manually add OP_RETURN output:
bitcoin-cli createrawtransaction '[{"txid":"your_input_txid","vout":0}]' '[{"data":"54686973206973206120746573742e"}]'
The transactions constructed in this way will not actually transfer money, but will only write this message on the chain.
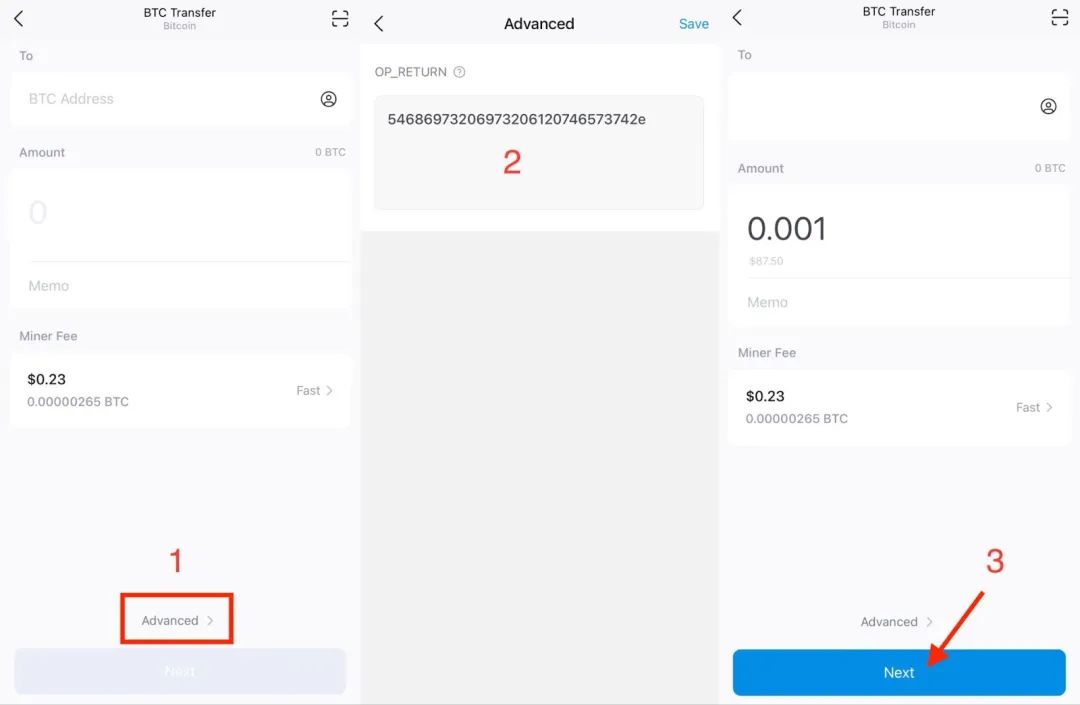
Take imToken wallet as an example, enter the BTC wallet transfer interface and open the "Advanced Mode". Enter hexadecimal information in the "OP_RETURN" input box. Click "Next" to complete the transaction information confirmation. Enter the transaction password and successfully send the transaction with OP_RETURN information. Please make sure "Input Amount = Output Amount + Miner's Fee".
Step 3: Broadcast transactions
Broadcast signed transactions over the Bitcoin network. Since the OP_RETURN transaction will not actually transfer money, it must include miner fees to process it. Wait for the miner to package it into the block. Once the transaction is confirmed, the message will be permanently saved in the Bitcoin blockchain.
Step 4: View the content of the message
After completing the transaction, a TXID will be obtained, which can be viewed through the block browser. The browser will usually automatically decode the OP_RETURN hexadecimal data back to ASCII, for example:
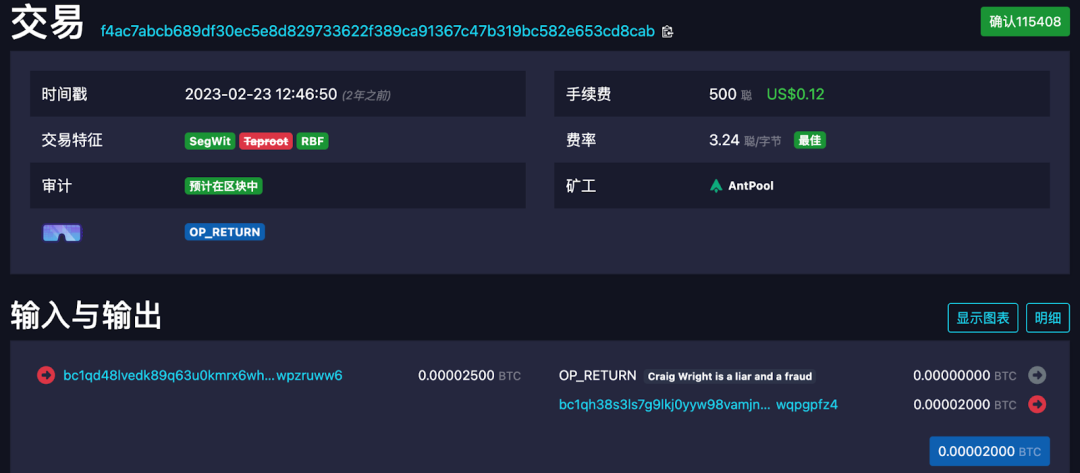
(https://mempool.space/tx/f4ac7abcb689df30ec5e8d829733622f389ca91367c47b319bc582e653cd8cab)
OP_RETURN Application
In security incidents, some attackers will leave messages on the chain using OP_RETURN to actively express their intention to return funds to the project party, or the project party and the white hat team also use this method to shout to the attacker and try to establish a connection. In addition to the scenarios applied to negotiations, OP_RETURN is also used for "marking" operations. For example, Chainalysis once disclosed that on the eve of the Russian-Ukrainian War in 2022, an unknown Bitcoin user used the OP_RETURN chain to leave a message, marking nearly 1,000 addresses suspected to be associated with the Russian security department. These messages are written in Russian, pointing out that these addresses may have been involved in cyber attacks or espionage:
- "GRU to SVR. Used for hacking!"
- "GRU to GRU. Used for hacking!"
- "GRU to FSB. Used for hacking!"
- "Help Ukraine with money from the GRU Khakir"
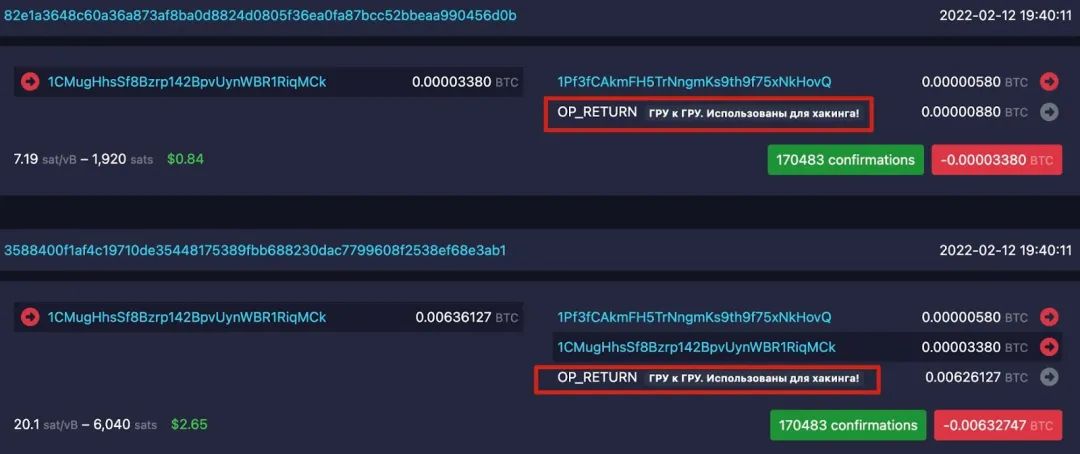
(https://mempool.space/address/1CMugHhsSf8Bzrp142BpvUynWBR1RiqMCk)
When this user issued these warnings, he did not just leave messages, but cooperated to burn a large amount of Bitcoin. Due to the OP_RETURN output nature, any bitcoin sent to such transactions will be burned and cannot be used. According to statistics, the user burned more than $300,000 worth of Bitcoin in this series of operations.
Summarize
On-chain messages, especially OP_RETURN in the Bitcoin network, provide an anonymous, public and tamper-free communication method, which is widely used in the early stages of fund recovery and information transmission. However, it should be noted that on-chain messages may also be used by attackers to guide victims to access malicious links or perform risky operations (such as entering private keys to decrypt them, etc.), so be sure to stay vigilant to avoid viewing and processing suspicious information on untrusted devices. When encountering a security incident, it is recommended to contact a professional security team as soon as possible to assist in the analysis to improve the success rate of fund recovery. At the same time, users and project parties should continue to strengthen their security awareness to avoid becoming targets of attack.


 jinse
jinse