DeFi Dark Forest Survival Guide: When Smart Contract Authorization becomes Asset Harvester

Reprinted from panewslab
03/11/2025·2MCryptocurrency and blockchain technology are redefining financial freedom, but this revolution has also spawned a new type of threat: scammers no longer rely solely on technical vulnerabilities, but instead transform the blockchain smart contract protocol itself into an attack tool. Through carefully designed social engineering traps, they use the transparency and irreversibility of blockchain to convert user trust into a tool for asset theft. From forging smart contracts to manipulating cross-chain transactions, these attacks are not only hidden and difficult to track down, but are also more deceptive because of their "legalization". This article will use real case analysis to reveal how scammers can transform the protocol itself into an attack vector, and provide a complete solution from technical protection to behavioral prevention to help you move forward safely in a decentralized world.
1. How can legal agreements become tools for fraud?
The original intention of the blockchain protocol is to ensure security and trust, but scammers use their characteristics and combine them with user negligence to create a variety of secret attack methods. Here are some techniques and technical details to illustrate:
(1) Malicious Smart Contract Authorization (Approve Scam)
Technical Principles:
On blockchains such as Ethereum, the ERC-20 token standard allows users to authorize third parties (usually smart contracts) to withdraw a specified number of tokens from their wallets through the "Approve" function. This feature is widely used in DeFi protocols such as Uniswap or Aave, where users need to authorize smart contracts to complete transactions, staking or liquidity mining. However, scammers use this mechanism to design malicious contracts.
How to operate:
Scammers create a DApp that disguises itself as a legitimate project, usually promoted via phishing sites or social media (such as fake "PancakeSwap" pages). The user connects to the wallet and is induced to click "Approve", which is ostensibly authorized a small number of tokens, but in fact it may be an unlimited quota (uint256.max value). Once the authorization is completed, the scammer's contract address is granted permission, and he can call the "TransferFrom" function at any time to withdraw all corresponding tokens from the user's wallet.
Real case:
In early 2023, phishing sites disguised as “Uniswap V3 upgrades” resulted in hundreds of users losing millions of dollars in USDT and ETH. On-chain data shows that these transactions are fully compliant with the ERC-20 standard and victims cannot even be recovered through legal means because the authorization is signed voluntarily.
(2) Phishing Signature

Technical Principles:
Blockchain transactions require users to generate signatures through private keys to prove the legitimacy of the transaction. Wallets (such as MetaMask) usually pop up a signature request, and after the user confirms, the transaction is broadcast to the network. Scammers use this process to forge signatures and request to steal assets.
How to operate:
The user receives an email or Discord message disguised as an official notification, such as "Your NFT airdrop is to be collected, please verify your wallet". After clicking on the link, the user is directed to a malicious website, requiring the wallet to be connected and a "verification transaction" is signed. The transaction may actually be a call to the "Transfer" function, directly transferring the ETH or tokens in the wallet to the scam address; or a "SetApprovalForAll" operation, authorizing the scam to control the user's NFT collection.
Real case:
The Bored Ape Yacht Club (BAYC) community was hit by a signature phishing attack, and multiple users lost millions of dollars in NFTs for signing fake "airdrop collection" transactions. The attacker used the EIP-712 signature standard to forge seemingly secure requests.
(3) Fake tokens and Dust Attack
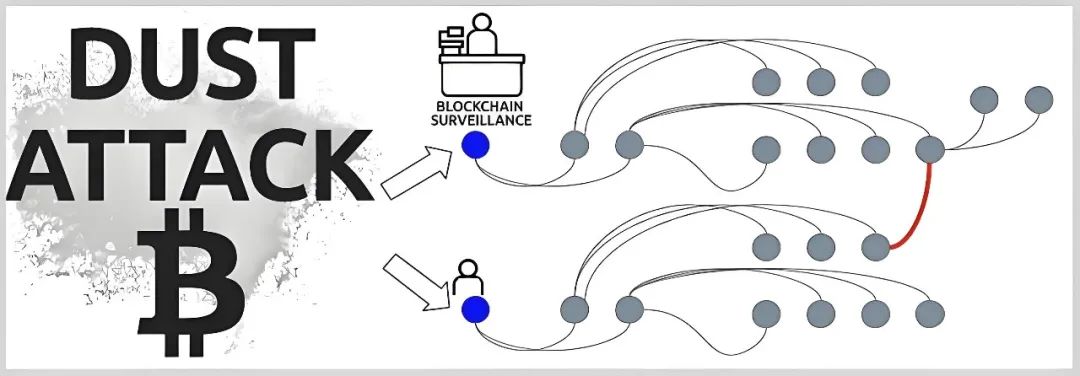
Technical Principles:
The disclosure of blockchain allows anyone to send tokens to any address, even if the receiver does not request it proactively. Scammers take advantage of this by sending small amounts of cryptocurrency to multiple wallet addresses to track wallet activity and connect it to the individual or company that owns the wallet. It starts with sending dust — sending a small amount of cryptocurrency to different addresses, and then the attacker tries to find out which belongs to the same wallet. The attacker then uses this information to launch a phishing attack or threat to the victim.
How to operate:
In most cases, the "dust" used by the dust attack is distributed to the user's wallet in the form of an airdrop. These tokens may carry names or metadata (such as "FREE_AIRDROP"), inducing users to visit a website to query details. Users will generally be happy to cash out these tokens, and then the attacker can access the user's wallet through the contract address attached to the token. The secret is that dust attacks will analyze user subsequent transactions through social engineering and lock the user's active wallet address, thereby implementing more accurate fraud.
Real case:
In the past, the “GAS token” dust attacks on the Ethereum network have affected thousands of wallets. Some users lost ETH and ERC-20 tokens due to curiosity interaction.
2. Why are these scams difficult to detect?
These scams are successful in large part because they are hidden in the legal mechanism of blockchain, making it difficult for ordinary users to distinguish their malicious nature. Here are a few key reasons:
- Technical Complexity:
Smart contract code and signature requests are obscure for non-technical users. For example, an "Approve" request may be displayed as hexadecimal data such as "0x095ea7b3...", and the user cannot intuitively judge its meaning.
- On-chain legality:
All transactions are recorded on the blockchain, which seems transparent, but victims often realize the consequences of authorization or signature afterwards, and the assets can no longer be recovered.
- Social Engineering:
Scammers exploit human weaknesses such as greed (“receive $1,000 tokens for free”), fear (“account abnormality requires verification”) or trust (disguised as MetaMask customer service).
- Exquisite disguise:
Phishing websites may use URLs similar to the official domain name (such as "metamask.io" to "metamaskk.io") and even increase credibility through HTTPS certificates.
3. How to protect your cryptocurrency wallet?
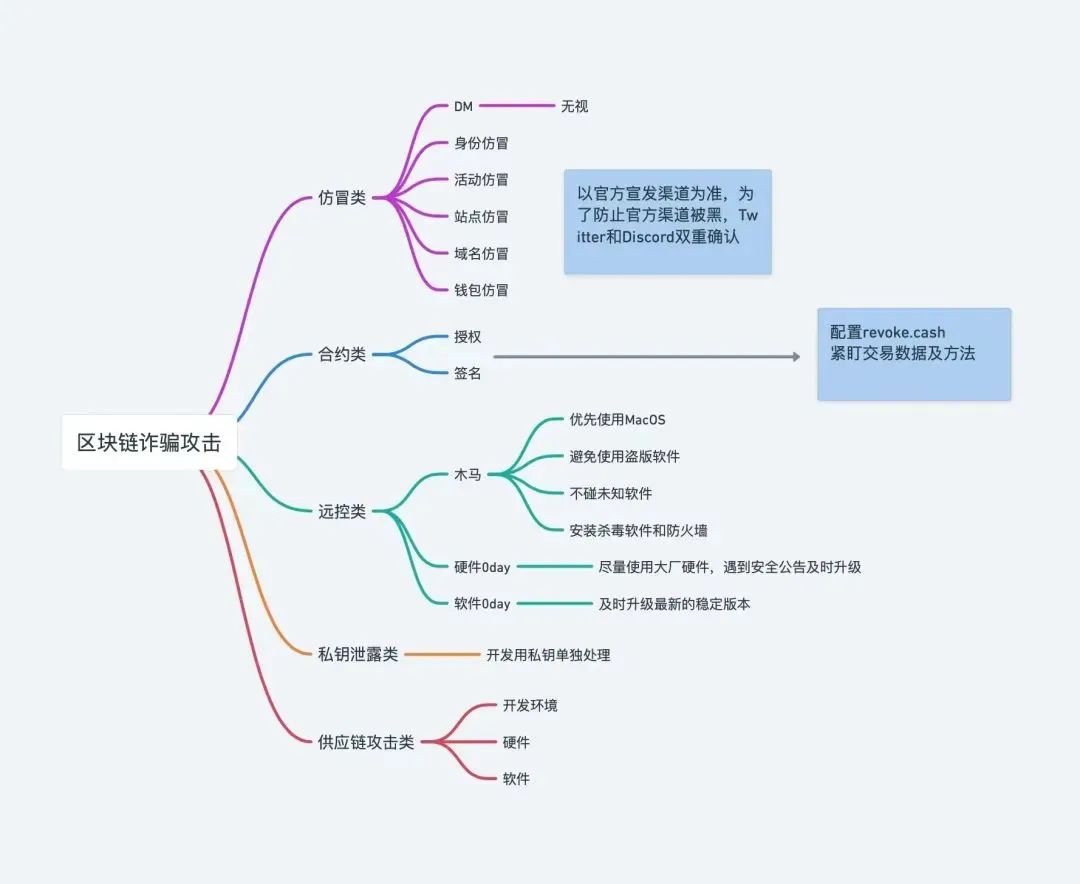
In the face of these scams where technical and psychological warfare coexist, blockchain security requires multi-level strategies to protect assets. The following are detailed precautions:
- Check and manage authorization permissions
Tool: Use Etherscan Approval Checker or Revoke.cash to check the wallet's authorization history.
Operation: Revoke unnecessary authorization periodically, especially unlimited authorization for unknown addresses. Before each authorization, make sure the DApp comes from a trusted source.
Technical details: Check the "Allowance" value. If it is "infinite" (such as 2^256-1), it should be revoked immediately.
- Verify links and sources
Method: Manually enter the official URL to avoid clicking on social media (such as Twitter, Telegram) or links in emails.
Check: Make sure the website uses the correct domain name and SSL certificate (green lock icon). Beware of misspellings or redundant characters.
Example: If you receive the "opensea.io" variant (such as "opensea.io-login"), you will immediately doubt its authenticity.
- Using cold wallets and multi-signature
Cold Wallet: Store most of your assets in a hardware wallet (such as the Ledger Nano X or Trezor Model T) and connect to the network only if necessary.
Multi-signature: For large assets, use tools such as Gnosis Safe to confirm transactions, requiring multiple keys to reduce the risk of single point errors.
Benefits: Even if a hot wallet (such as MetaMask) is compromised, cold storage assets are still safe.
- Handle signature requests with caution
Steps: Read the transaction details in the wallet pop-up window carefully every time you sign. MetaMask will display the "Data" field, and if it contains unknown functions (such as "TransferFrom"), the signature will be rejected.
Tools: Use Etherscan's "Decode Input Data" feature to parse signed content, or consult a technical expert.
Suggestions: Create a separate wallet for high-risk operations and store a small amount of assets.
- Respond to dust attacks
Strategy: Do not interact after receiving unknown tokens. Mark it as "garbage" or hide.
Check: Confirm the source of the tokens through the blockchain browser OKLink and other platforms. If it is sent in batches, be highly vigilant.
Prevention: Avoid publicizing wallet addresses or using new addresses for sensitive operations.
Conclusion
By implementing the above security measures, ordinary users can significantly reduce the risk of becoming victims of advanced fraud schemes, but true security is by no means a unilateral victory of technology. When hardware wallets build physical defense lines and multi-signals spread risk exposure, users' understanding of authorization logic and prudence of on-chain behavior are the last bastion to resist attacks. Each data analysis before signature and each authorization review are oaths of one's own digital sovereignty.
In the future, no matter how technology iterates, the most core line of defense will always be: internalize safety awareness into muscle memory and establish an eternal balance between trust and verification. After all, in the blockchain world where code is law, every click and every transaction are permanently recorded in the on-chain world and cannot be changed.

 jinse
jinse
