Bybit was stolen nearly $1.5 billion. Is it North Korean hackers who stepped on the brakes in the bull market?

Reprinted from panewslab
02/22/2025·2MAuthor: BitpushNews Mary Liu
While the crypto community is still hotly discussing the direction of the bull market, on February 21, a sudden black swan event "critical" the market. The veteran crypto exchange Bybit was hacked and nearly $1.5 billion of assets were stolen, mainly ETH, equivalent to about 401,347, worth about $1.12 billion.
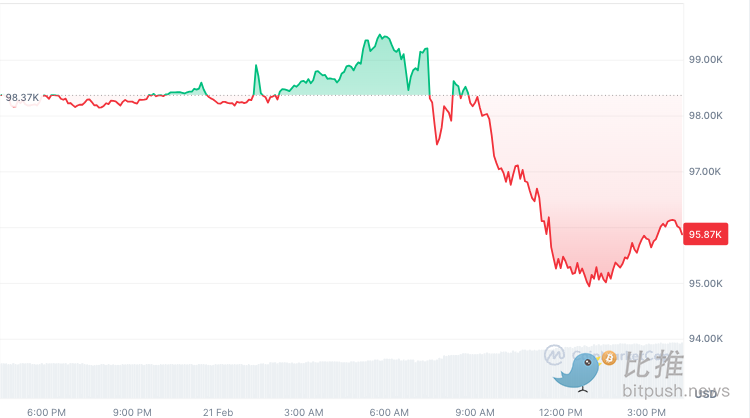
After the news came out, Bitcoin fell, falling below the $95,000 mark at one point; Ethereum, which was already weak, plunged 5% in the short term to $2,615, and rebounded to the $2,666 level as of press time.
The Bybit team responded quickly, CEO Ben Zhou started the live broadcast in the face of danger and promised users that the platform would never close the withdrawal channel. He said that even if the funds cannot be fully recovered, Bybit has the ability to fully compensate users' losses.
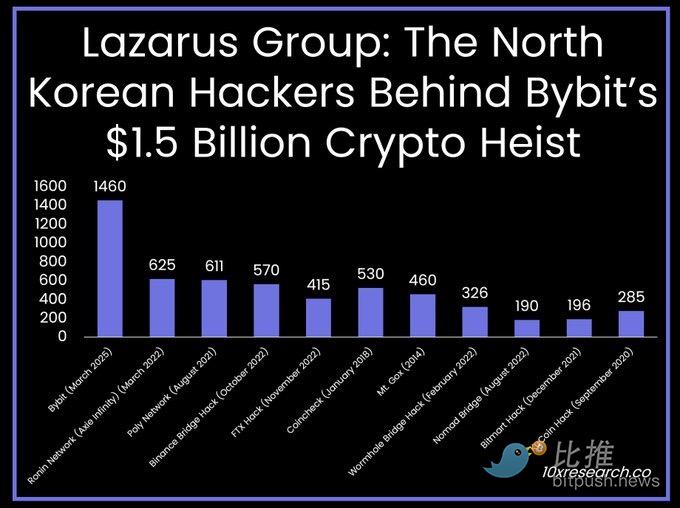
According to 10x Research statistics, the $1.46 billion stolen by Bybit exchange is the largest hacker attack in the history of crypto exchanges, and the second largest crypto theft was $611 million in Poly Network in 2021. In addition, on-chain detective ZachXBT has submitted conclusive evidence to confirm that the North Korean hacker group Lazarus Group is behind the attack.
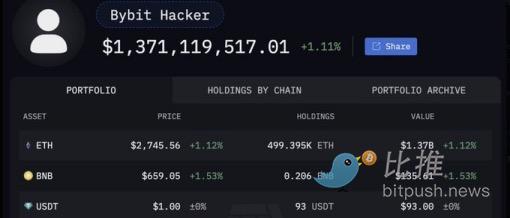
The trends of hacker addresses have become the focus of attention. On-chain data shows that Bybit hacker address has now become the 14th largest ETH holder in the world, holding about 0.42% of the total supply of Ethereum, exceeding Fidelity, Vitalik Buterin, and even the Ethereum Foundation. More than twice the amount.
Industry support: Bybit is definitely not FTX!
Coinbase executive Conor Grogan posted on social media to support Bybit: "After the hack, withdrawals seem to be working. They have more than $20 billion in assets on the platform and their cold wallet is unscathed. Given the signature I don't expect contagiousness to be contagious in the isolated nature of the hacker attack and Bybit's capital strength."
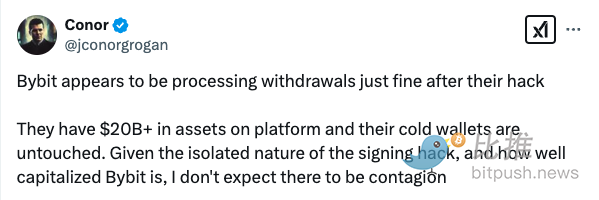
Grogan also stressed: "A minute after the run happened, it was obvious that they had no funds to withdraw. I know everyone has PTSD, but Bybit is different from FTX, and if so, I would shout out . They will be fine."
Faced with this incident, many industry participants expressed their support for Bybit.
In the early morning of February 22, Beijing time, on-chain data showed that addresses from Binance and Bitget transferred 50,000 ETH to Bybit cold wallet. Among them, Bitget's transfer volume accounts for one-quarter of its total ETH, which has attracted attention. According to Conor Grogan, the transaction was directly coordinated by Bybit, skipping commonly used deposit addresses.
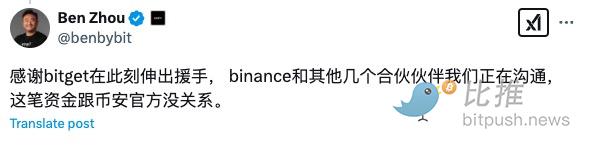
Ben Zhou responded to this: "Thanks to Bitget for lending a helping hand at this moment. We are communicating with several other partners. This fund has nothing to do with Binance."
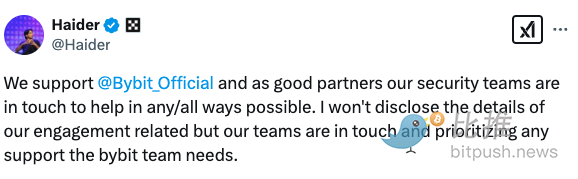
Tron founder Justin Sun said on social media that the Tron network is helping track funds. OKX Chief Marketing Officer Haider Rafique also said the exchange has deployed a security team to support Bybit's investigation.
KuCoin emphasized that encryption is "a common responsibility" and called for cross-exchange cooperation to combat cybercrime.
Safe security raises doubts
The core of this attack lies in a technology called "Blind Signing". Blind signing refers to users approving transactions without fully understanding the content of smart contracts. This technology is used by hackers to bypass security verification.
Bybit CEO Ben Zhou pointed out in the live broadcast that the attacker forged the multi-signal wallet user interface (UI) provided by Safe through "Musked" technology (i.e. obfuscating or spoofing transaction loads), allowing the signer to authorize malicious intentions without knowing it. trade. Specifically, the attacker displays the correct address and URL through the fake UI interface, but in fact the transaction load has been tampered with, causing the signer to inadvertently approve the transfer of funds.
Cryptocurrency security firm Groom Lake further found that the Safe multi-signment wallets deployed on Ethereum in 2019 and the 2024 Safe multi-signment wallets have the same transaction hash value, which is almost impossible mathematically.
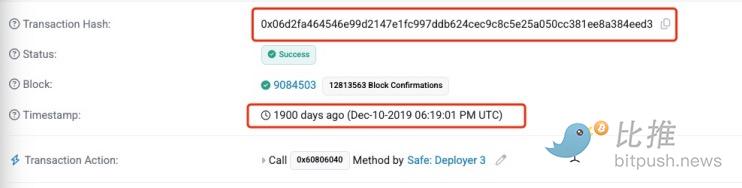
If the same transaction hash appears on Ethereum and Base, it indicates that an attacker may have found a way to make a single transaction work on multiple networks, or possibly reused across networks, anonymous Groom Lake researcher Apollo said Encrypt wallet signature or transaction data.
However, the Safe team denied that the attack was related to its smart contract vulnerability, saying that the transaction in question was a transaction that deployed a singleton contract and did not use EIP-155, a security measure to prevent cross-chain transaction replay attacks, to support cross-border Chain deployment. EIP-155 was launched in 2016 and ensures that transactions used for Ethereum cannot be valid on other chains such as Base by adding chain IDs to signed transactions. This means that even if the private key is leaked, the attacker cannot reuse old signed transactions on different chains. "If it is (smart contract vulnerability), the goal will not be Bybit," the Safe team said. Note: Safe protects over $100 billion in digital assets in more than 7 million smart accounts in total.
Is hardware wallet not omnipotent?
However, Safe's explanation does not completely eliminate industry doubts. Ido Ben Natan, CEO of Blockaid, blockchain security firm Blockaid, pointed out that "blind signing" technology is quickly becoming the favorite form of attack for advanced threat actors, such as North Korean hackers. This attack is the same type of attack used in the December 2023 Radiant Capital invasion and the March 2024 WazirX incident. Natan stressed that even with the best key management solutions, the signature process still relies on software interfaces that interact with dApps, opening the door to maliciously manipulating the signature process.
Security expert Odysseus pointed out that if the transaction is signed on an internet-connected laptop or mobile phone, the role of the hardware wallet will be greatly reduced. “These are highly targeted attacks, and generally speaking, if a device (computer or cell phone) is hacked, there is little to do except sign a transaction on an unnetworked and uninvased device,” he said.
Under bull market sentiment, safety issues are often easily overlooked. It is not too late to make up for the loss. What the community hopes to see is that Bybit can properly resolve the crisis and minimize the losses. But this attack once again reminds us: in the crypto world, security is always the first line of defense. From the vulnerabilities of multi-sign wallets to the risks of cross-chain transactions, from user education to industry collaboration, every link should be re-examined.


 jinse
jinse

 chaincatcher
chaincatcher