Nearly $100 million destroyed: Iranian exchange Nobitex theft incident sorted out

転載元: chaincatcher
06/21/2025·14hAuthor: Lisa & 23pds
Editor: Sherry
background
On June 18, 2025, on-chain detective ZachXBT disclosed that Nobitex, Iran's largest crypto trading platform, was suspected to have been hacked, involving abnormal transfer of large amounts of assets in multiple public chains.

SlowMist further confirmed that the affected assets in the incident cover TRON, EVM and BTC networks, with preliminary estimates of approximately US$81.7 million.

(https://x.com/slowmist_team/status/1935246606095593578)
Nobitex also issued an announcement confirming that some infrastructure and hot wallets did encounter unauthorized access, but emphasized that user funds are safe.

(https://x.com/nobitexmarket/status/1935244739575480472)
It is worth noting that the attacker not only transferred funds, but also actively transferred a large amount of assets to a specially-made destruction address, with the "burned" assets worth nearly US$100 million.

(https://x.com/GonjeshkeDarand/status/1935412212320891089)
Timeline combing
June 18
-
ZachXBT disclosed that Iran's crypto exchange Nobitex is suspected to have been hacked and a large number of suspicious withdrawal transactions occurred on the TRON chain. SlowMist further confirmed that the attack involved multiple chains, with a preliminary estimate of approximately $81.7 million in losses.
-
Nobitex said that the technical team detected that some infrastructure and hot wallets were illegally accessed, and immediately cut off the external interface and initiated an investigation. The vast majority of assets are stored in cold wallets and the intrusion is limited to some of the hot wallets it uses for daily liquidity.
-
The hacker group Predatory Sparrow (Gonjeshke Darande) claimed responsibility for the attack and announced that it would release Nobitex source code and internal data within 24 hours.

(https://x.com/GonjeshkeDarand/status/1935231018937536681)
June 19
-
Nobitex issued a fourth statement, saying that the platform has completely blocked the external access paths of the server, and that the hot wallet transfer is "an active migration made by the security team to ensure funds." At the same time, it was officially confirmed that the stolen assets were transferred to wallets with non-standard addresses composed of arbitrary characters, which were used to destroy user assets, totaling about $100 million.
-
Hacker group Predatory Sparrow (Gonjeshke Darande) claims to have burned down about $90 million worth of crypto assets and called it a "sanctions evasion tool."
-
The hacker organization Predatory Sparrow (Gonjeshke Darande) exposes the Nobitex source code.

(https://x.com/GonjeshkeDarand/status/1935593397156270534)
Source code information
Based on the source code information released by the attacker, the folder information is obtained as follows:

Specifically, the following are involved:

Nobitex's core system is mainly written in Python and is deployed and managed using K8s. Based on the known information, we speculate that the attacker may have broken through the operation and maintenance boundary and entered the intranet. The analysis will not be carried out here.
MistTrack Analysis
The attacker used multiple seemingly legal but actually uncontrollable "destroy addresses" to receive assets. Most of these addresses comply with the on-chain address format verification rules and were able to successfully receive assets, but once the funds were transferred in, it was equivalent to permanent destruction. At the same time, these addresses also had emotional and provocative words, which were attacking. Some of the "destroyed addresses" used by the attacker are as follows:
-
TKFuckiRGCTerroristsNoBiTEXy2r7mNX
-
0xffFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFDead
-
1FuckiRGCTerroristsNoBiTEXXXaAovLX
-
DFuckiRGCTerroristsNoBiTEXXXWLW65t
-
FuckiRGCTerroristsNoBiTEXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
-
UQABFuckIRGCTerroristsNOBITEX11111111111111111111111_jT
-
one19fuckterr0rfuckterr0rfuckterr0rxn7kj7u
-
rFuckiRGCTerroristsNoBiTEXypBrmUM
We used the on-chain anti-money laundering and tracking tool MistTrack for analysis. The incomplete statistics of Nobitex's losses are as follows:
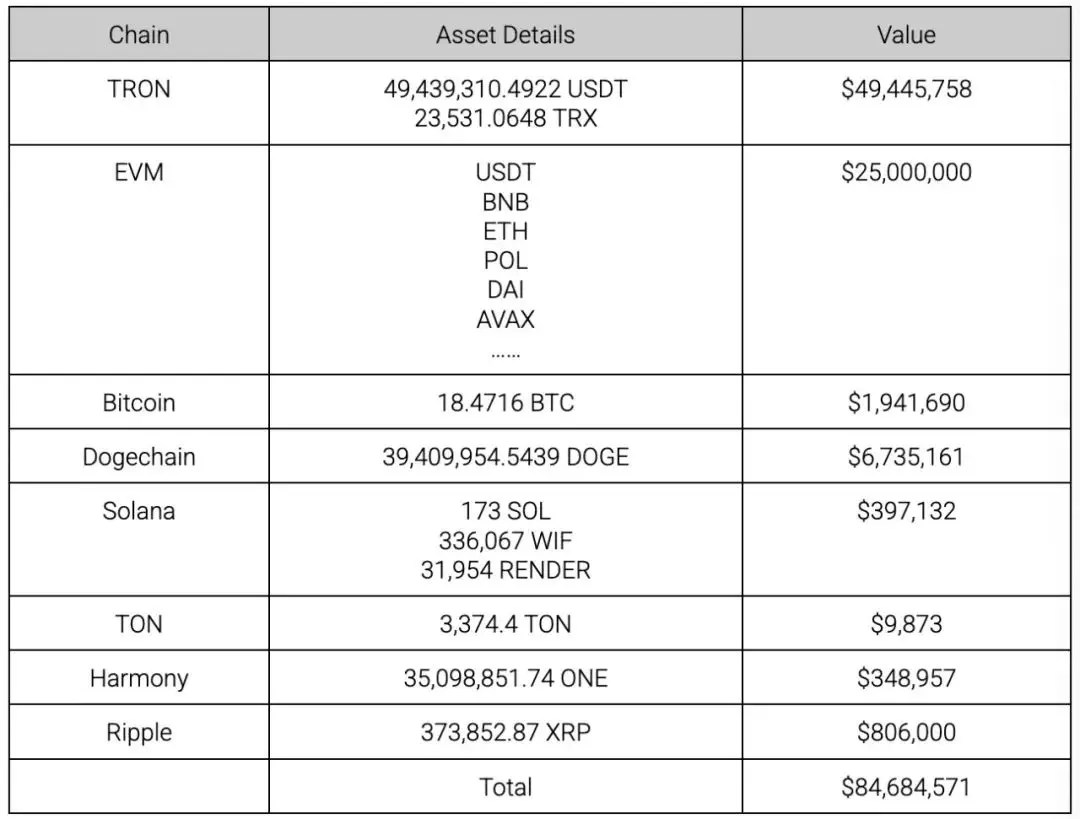
According to MistTrack analysis, the attacker completed 110,641 USDT transactions and 2,889 TRX transactions on TRON:

The EVM chains stolen by the attacker mainly include BSC, Ethereum, Arbitrum, Polygon and Avalanche. In addition to the mainstream currency of each ecosystem, it also includes various tokens such as UNI, LINK, SHIB.

On Bitcoin , the attackers stole a total of 18.4716 BTC, about 2,086 transactions.

On Dogechain, the attackers stole a total of 39,409,954.5439 DOGE, about 34,081 transactions.

On Solana, attackers steal SOL, WIF , and RENDER:

On TON, Harmony, and Ripple , the attackers stole 3,374.4 TON, 35,098,851.74 ONE and 373,852.87 XRP, respectively:

MistTrack has added the relevant addresses to the malicious address library and will continue to pay attention to the trends on the relevant links.
Conclusion
The Nobitex incident once again reminds the industry: security is a whole, and the platform needs to further strengthen security protection and adopt more advanced defense mechanisms. Especially for platforms that use hot wallets for daily operations, SlowMist suggests:
-
Strictly isolate the permissions of hot and cold wallets and access paths, and regularly audit the permissions of hot wallet calling;
-
Adopt on-chain real-time monitoring systems (such as MistEye) to obtain comprehensive threat intelligence and dynamic security monitoring in a timely manner;
-
Cooperate with the on-chain anti-money laundering system (such as MistTrack) to promptly detect abnormal capital flows;
-
Strengthen the emergency response mechanism to ensure that the attack can be effectively responded within the golden window after it occurs.
The incident is still under investigation, and the Slow Fog Security Team will continue to follow up and update the progress in a timely manner.



